Pakistan-linked APT36 abuses Linux .desktop files to drop custom malware in new campaign Pierluigi Paganini August 25, 2025 APT36 uses…
A novel macOS infostealer malware, designated as Mac.c, has emerged as a formidable contender in the underground malware-as-a-service (MaaS) ecosystem….
Electronics manufacturer Data I/O took offline operational systems following a ransomware attack Pierluigi Paganini August 25, 2025 Electronics manufacturer Data…
Cybersecurity researchers at the Cofense Phishing Defense Center (PDC) have uncovered a fresh surge in credential harvesting attacks that leverage…
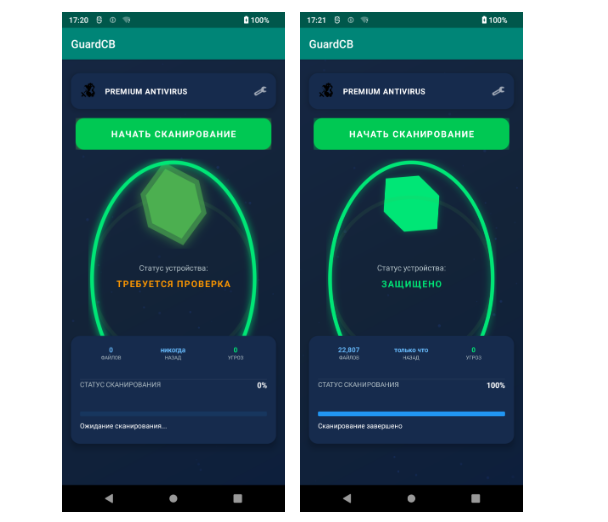
Android.Backdoor.916.origin malware targets Russian business executives Pierluigi Paganini August 25, 2025 New Android spyware Android.Backdoor.916.origin is disguised as an antivirus…
August 25, 2025, marks the 34th anniversary of Linux, a project that began as a modest hobby and has grown…
The manufacturing sector is entering a new phase of digital transformation. According to Rockwell Automation’s 10th Annual State of Smart…
Last week on Malwarebytes Labs: Stay safe! We don’t just report on threats – we help protect your social media…
A cybersecurity researcher has unveiled a sophisticated new method for extracting Windows credentials and secrets that successfully evades detection by…
Satellites play a huge role in our daily lives, supporting everything from global communications to navigation, business, and national security….
A critical zero-click remote code execution vulnerability in Apple’s iOS has been disclosed with a working proof-of-concept exploit, marking another…
Insider threats are among the hardest attacks to detect because they come from people who already have legitimate access. Security…