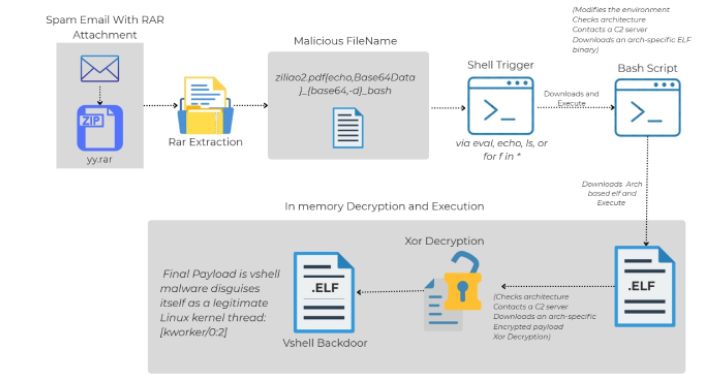
Cybersecurity researchers have shed light on a novel attack chain that employs phishing emails to deliver an open-source backdoor called…
A sophisticated cryptojacking campaign has emerged, exploiting misconfigured Redis servers across multiple continents to deploy cryptocurrency miners while systematically dismantling…
In its recently released 2025 Threat Hunting Report, Crowdstrike pointed out an interesting trend: a 136% surge in cloud intrusions….
The Lumma information stealer has evolved from its 2022 origins into one of the most sophisticated malware-as-a-service (MaaS) ecosystems in…
Microsoft Threat Intelligence has spotlighted the escalating adoption of the ClickFix social engineering technique, a sophisticated method that manipulates users…
22 Aug Women Know Cyber: Inspiring Stories On Social Media Posted at 08:59h in Blogs by Amanada Glassner This week…
Aug 22, 2025Ravie LakshmananOnline Fraud / Financial Crime INTERPOL on Friday announced that authorities from 18 countries across Africa have…
A sophisticated supply chain attack has emerged targeting developers through a malicious Go module package that masquerades as a legitimate…
The figures are appalling – 60% of small businesses fail within six months of a cyber-attack. Cyber attackers are all…
The Zscaler ThreatLabz team has uncovered significant advancements in the Anatsa malware, also known as TeaBot, an Android banking trojan…
22 Aug Women Know Cyber: Inspiring Stories On Social Media Posted at 08:59h in Blogs by Amanada Glassner This week…
Cybersecurity researchers are calling attention to malicious activity orchestrated by a China-nexus cyber espionage group known as Murky Panda that…