The Chinese state-backed threat group Silk Typhoon has raised the pace of attacks targeting government, technology, legal and professional services…
The Kali Linux team has announced a significant enhancement of its Vagrant image build process, streamlining development and simplifying deployment…
Researchers have discovered a complex campaign using trojanized software that uses authentic code-signing certificates to avoid detection and turn compromised…
Qilin ransomware claims a 4TB data breach at Nissan CBI, leaking car design files, financial data, 3D models, and VR…
Federal Trade Commission Chair Andrew Ferguson warned U.S. tech companies not to accede to laws in foreign countries that weaken…
A sophisticated cyber espionage campaign attributed to APT MuddyWater has emerged targeting Chief Financial Officers and finance executives across Europe,…
Adversaries are using AI-powered website builders to expedite the development of harmful infrastructure in a quickly changing threat landscape, hence…
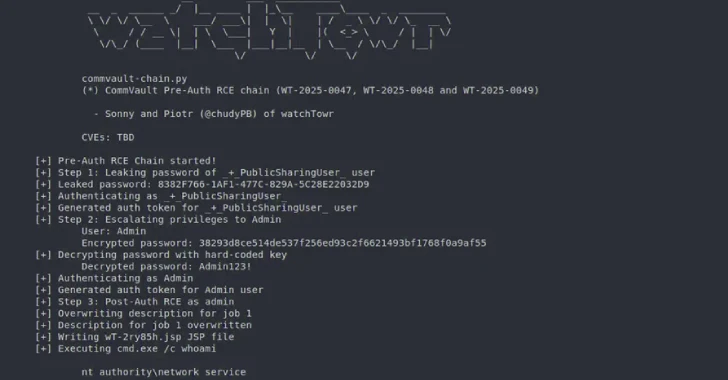
Aug 21, 2025Ravie LakshmananVulnerability / Software Security Commvault has released updates to address four security gaps that could be exploited…
Apple addressed the seventh actively exploited zero-day Pierluigi Paganini August 21, 2025 Apple addressed a vulnerability impacting iOS, iPadOS, and…
Mozilla has released Firefox 142 to address multiple high-severity security vulnerabilities that could allow attackers to execute arbitrary code remotely…
The week of August 4th, I had the opportunity to attend two exciting conferences in the cybersecurity world: Black Hat…
The Warlock ransomware group has intensified its operations by targeting unpatched on-premises Microsoft SharePoint servers, leveraging critical vulnerabilities to achieve…