Data backup and replication specialist Commvault has issued patches covering off four vulnerabilities in its core software product that, left…
The pharmaceutical and biotechnology company Inotiv Inc. is investigating a cyberattack that led to hackers encrypting the firm’s data, it…
Security leaders today are rethinking email security, not because traditional methods have failed outright, but because the threat landscape and…
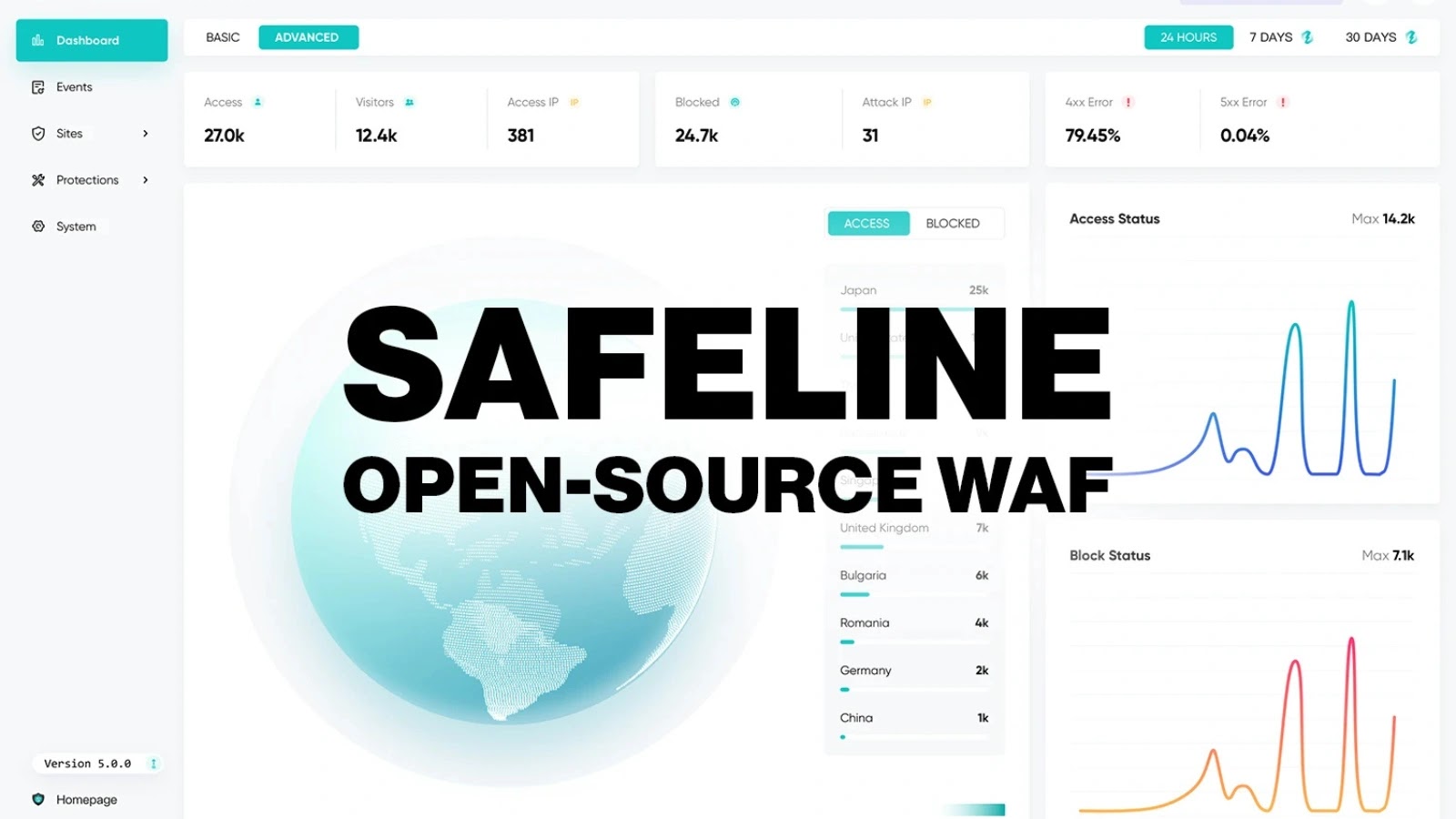
Every type of organization—whether it’s a multinational giant with thousands of employees or a single tech enthusiast running a homelab—needs…
United States Custom and Border Protection officials have sweeping powers to search anyone’s phone when they are entering the country—including…
The proliferation of generative AI (GenAI) platforms has revolutionized web-based services, enabling rapid code assistance, natural language processing, chatbot deployment,…
If you crank up the Wayback Machine and load the websites of today’s biggest managed security service providers (MSSPs), you’ll…
A Russian state-sponsored espionage group has been systematically compromising network devices worldwide for over a decade, exploiting a seven-year-old vulnerability…
Hackers are using a novel technique that combines legitimate office.com links with Active Directory Federation Services (ADFS) to redirect users to…
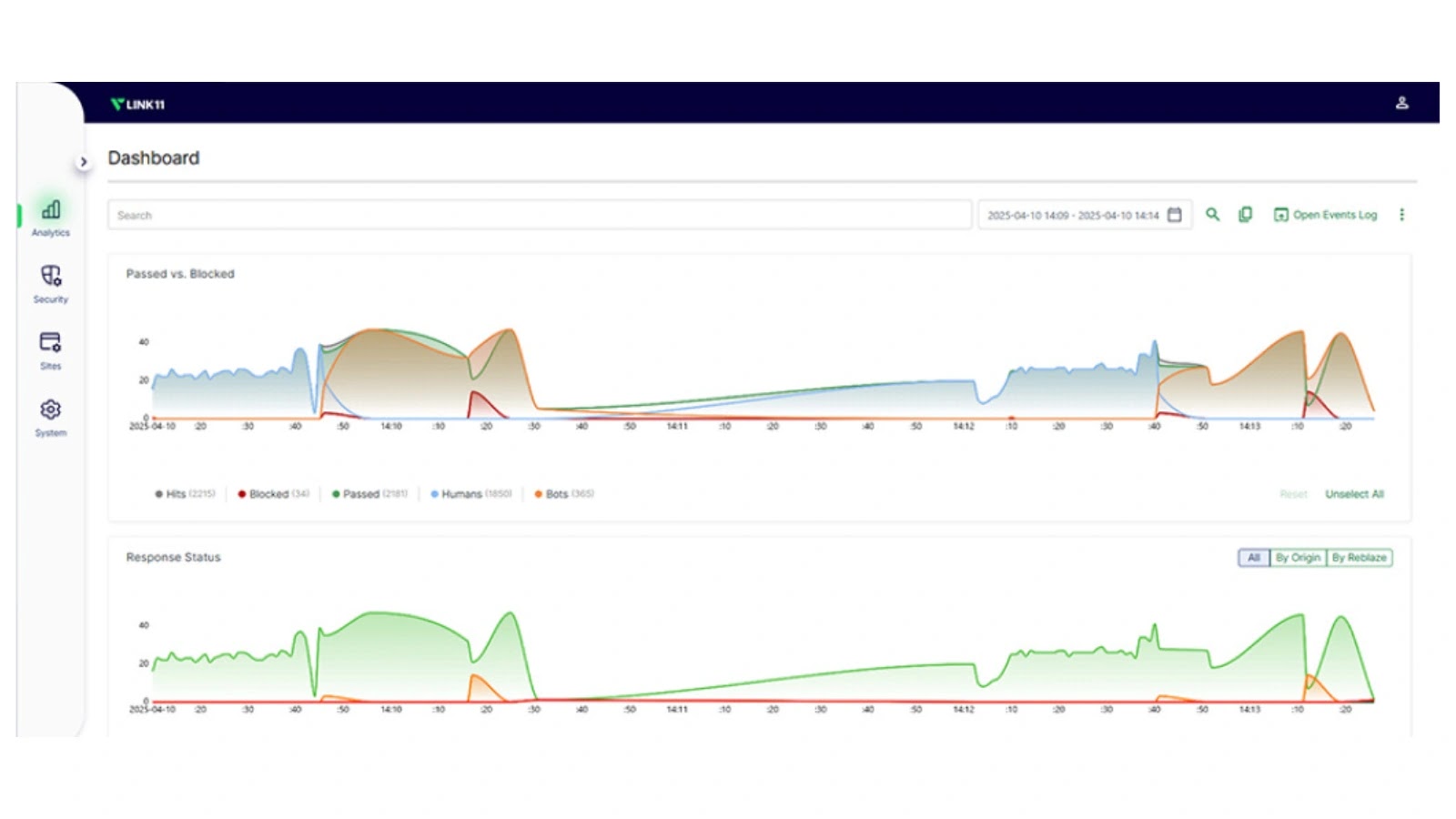
Link11, a Germany-based global IT security provider, has released insights into the evolving cybersecurity threat landscape and announced the capabilities…
Security researchers have disclosed a critical vulnerability in Kubernetes Capsule v0.10.3 and earlier versions that allows authenticated tenant users to…
Doctor Web warns of Android.Backdoor.916.origin, a fake antivirus app that spies on Russian users by stealing data, streaming audio and…