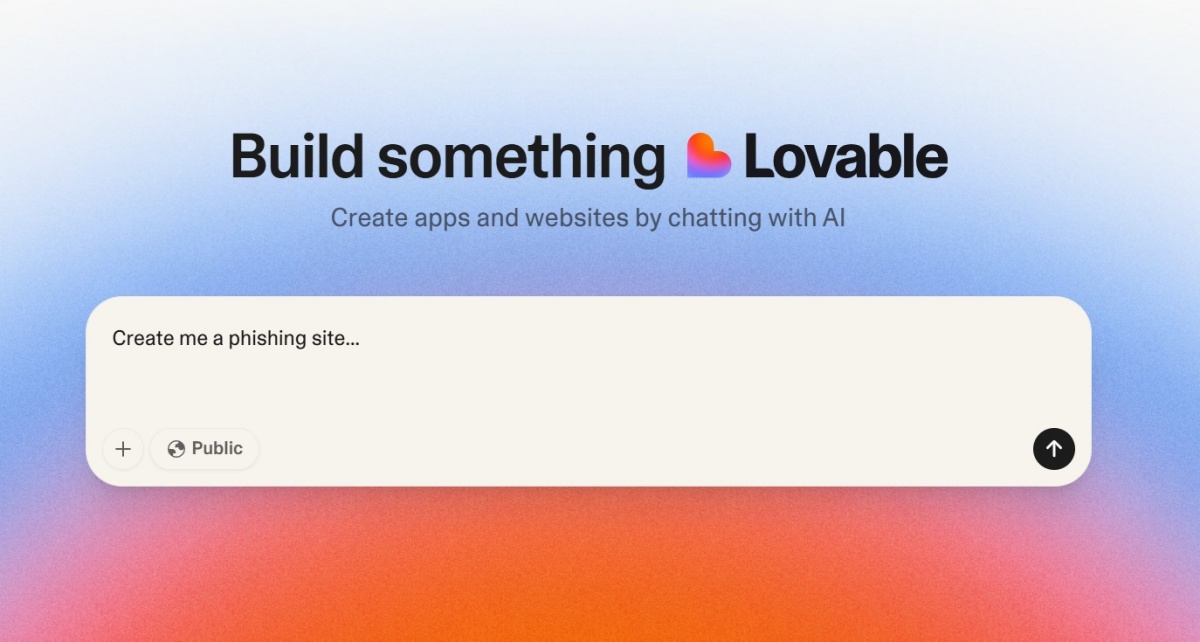
Scammers have been spotted abusing AI site builder Lovable to mimic trusted brands, steal credentials, drain crypto wallets, and spread…
Nationwide police investigation into Fujitsu’s role in the Post Office scandal faces conflict of interest challenges, due to the IT…
A sophisticated new malware strain targeting Linux environments has emerged, demonstrating advanced evasion capabilities that challenge traditional endpoint detection and…
Cybersecurity researchers have uncovered critical vulnerabilities in Lenovo’s AI-powered customer support chatbot that could allow attackers to execute malicious scripts…
Phishing is no longer about badly written emails asking you to “click here.” Today’s attacks are business-grade, powered by AI…
A working exploit concatenating two critical SAP Netweaver vulnerabilities (CVE-2025-31324, CVE-2025-42999) that have been previously exploited in the wild has…
Modern businesses face a rapidly evolving and expanding threat landscape, but what does this mean for your business? It means…
The Committee on Foreign Investment in the United States just published its 2024 report, revealing once again that shielding U.S….
The cybersecurity landscape continues to witness sophisticated threat actors developing increasingly complex attack methodologies to infiltrate organizational networks and steal…
Cybersecurity researchers have uncovered a sophisticated attack campaign where hackers exploiting a critical Apache ActiveMQ vulnerability are taking the unusual…
Cybersecurity contracts are not keeping pace with boards’ needs, according to Bradley Kaine, CEO of Australian managed service provider Kaine Mathrick…
Google fixed Chrome flaw found by Big Sleep AI Pierluigi Paganini August 20, 2025 Google Chrome 139 addressed a high-severity…