Panama’s Ministry of Economy and Finance (MEF) has disclosed that one of its computers may have been compromised in a cyberattack..
The government noted that it activated the security procedures for these situations, stating that the incident has been contained and didn’t impact core systems that are vital to its operations.
“The Ministry of Economy and Finance informs the public that today an incident involving possible malicious software was detected on one of the Ministry’s workstations,” MEF says in an official statement.
“The established security protocols were immediately activated, and preventive measures across the entire IT system were reinforced to contain the intrusion.”
“It is important to emphasize that none of MEF’s central systems or platforms have been compromised and they continue operating normally.”
Panama’s MEF is an important ministry in the country, managing fiscal policy, public spending, and debt management. Most importantly, it handles the Panama Canal revenues, the country’s largest source of income.
The MEF says that personal and institutional data are safe, and all industry-standard measures are in place to prevent future incidents.
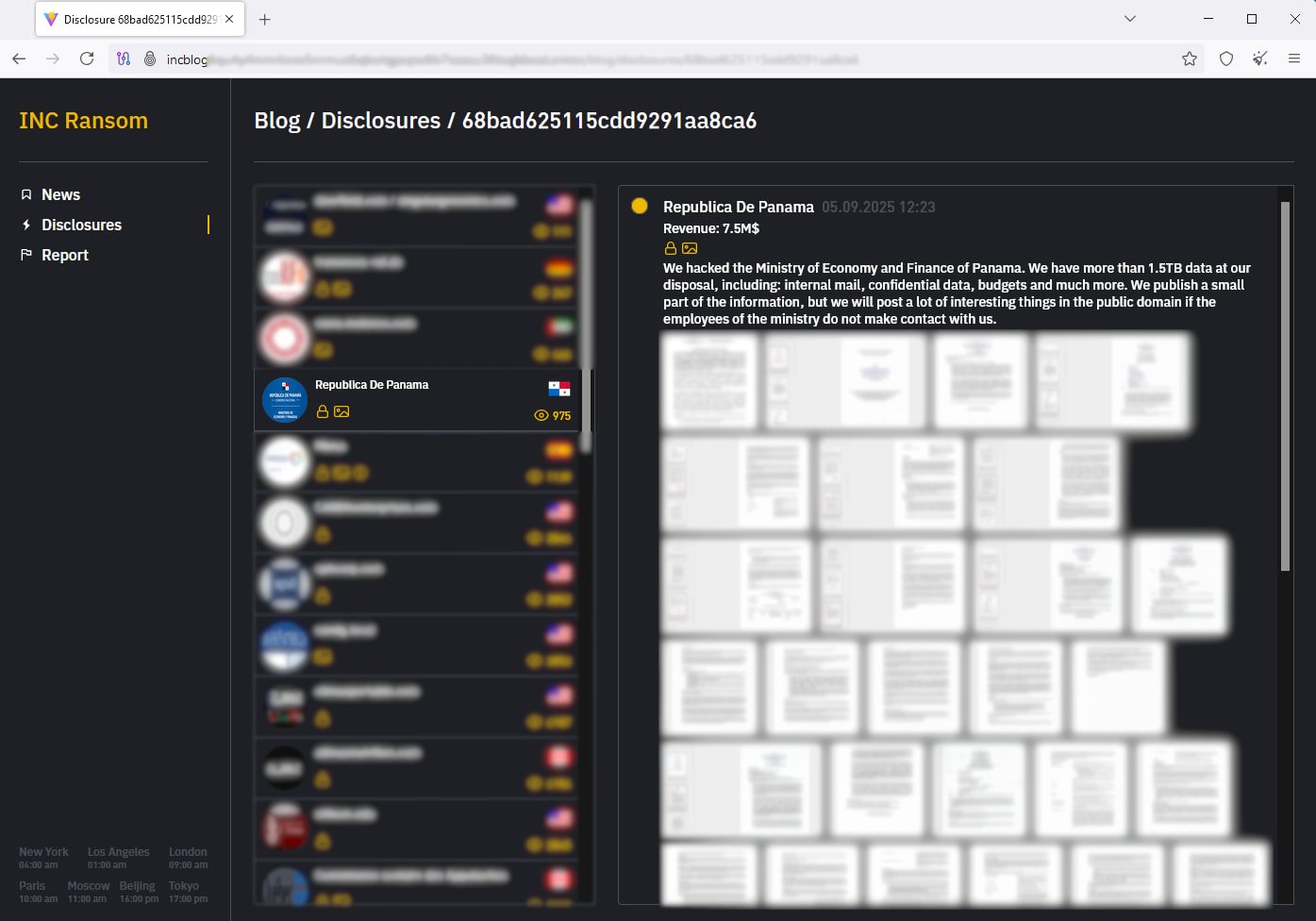
Hoewever, the INC Ransom gang has claimed an attack on MEF last week in a post on its data leak site. The hackers say that they stole more than 1.5 TB of data from MEF’s systems, including emails, financial documents, budgeting details, and more.
The threat group added MEF to its list of victims on the dark web on September 5, and leaked data samples in the form of internal documents as proof of the breach.
Source: BleepingComputer
BleepingComputer contacted MEF to ask about the validity of INC Ransom’s claims, but we have not received a response by publication time.
INC Ransom emerged in mid-2023 as a ransomware-as-a-service (RaaS). They targeted multiple high-profile victims such as Yamaha Motor, Xerox Business Solution, Scotland’s NHS, McLaren Health Care, the Texas State Bar, and Ahold Delhaize.
In May 2024, a threat actor using the moniker “salfetka” posted on the Russian-speaking hacking forums that they had the source code for the ransomware and offered to sell it for $300,000.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.

