The Paraguay military is warning of Black Hunt ransomware attacks after Tigo Business suffered a cyberattack last week impacting cloud and hosting services in the company’s business division.
Tigo is the largest mobile carrier in Paraguay, with its Tigo Business division offering digital solutions to the enterprise, including cybersecurity consulting, cloud and data center hosting, and wide area network (WAN) solutions.
Over the weekend, local media reported that companies were dealing with outages in their websites hosted at Tigo Business since Thursday.
While it was suspected that Tigo suffered a cyber attack, the company did not officially confirm the attack until the weekend, when they released a statement.
“On January 4, we were victims of a security incident in our Tigo Business Paraguay infrastructure as a service, which has affected the normal supply of some specific services to a limited group of clients in the corporate segment (companies).” reads a statement from Tigo Business.
The statement goes on to say that much of the news reported online is inaccurate and that the attack did not affect internet, telephone services, and Tigo Money electronic wallets.
While Tigo did not provide any details regarding the cyberattack, numerous reports on social media indicate that they suffered an attack by the Black Hunt ransomware operation.
These reports stated that over 330 servers were encrypted, and backups were compromised during the attack.
The next day, Paraguay’s General Directorate of Information and Communication Technologies of the Armed Forces of Paraguay (FFAA) issued an alert warning companies in the country of Black Hunt ransomware attacks.
“The DSIRT-MIL of the DIGETIC/FFAA, issues an official alert in relation to the recent cybersecurity incident that has significantly impacted one of the main internet service providers in the country and that has had a direct impact on more than 300 companies associated with said operator, compromising backups, web pages, emails and their cloud storage,” read a now-deleted warning from Paraguays DSIRT-MIL.
“The incident that occurred, according to reports from cybersecurity specialists, is a ransomware infection linked to a group of cybercriminals called Black Hunt.”
The bulletin was soon deleted, with DSIRT-MIL stating it was not linked to any cybersecurity incident.
Who is Black Hunt ransomware
The Black Hunt ransomware operation launched at the end of 2022 when cybersecurity researchers began reporting attacks. From numerous victims seen by BleepingComputer, the threat actors commonly attack companies in South America.
Like other ransomware operations, the threat actors breach corporate networks and silently spread laterally to other devices until they gain enough access to deploy the encryptors on the network.
When the encryptors are launched, they will perform the following commands to clear Windows event logs, delete Shadow Volume Copies and NTFS journals, and disable Windows recovery options.
cmd.exe /c vssadmin.exe Delete Shadows /all /quiet
cmd.exe /c bcdedit /set {default} recoveryenabled No
cmd.exe /c bcdedit /set {default} bootstatuspolicy IgnoreAllFailures
cmd.exe /c fsutil.exe usn deletejournal /D C:
cmd.exe /c wbadmin.exe delete catalog -quiet
cmd.exe /c schtasks.exe cmd.exe /change /TN "MicrosoftWindowsSystemRestoreSR" /disable
cmd.exe /c wevtutil.exe cl Setup
cmd.exe /c wevtutil.exe cl System
cmd.exe /c wevtutil.exe cl Application
cmd.exe /c wevtutil.exe cl Security
cmd.exe /c wevtutil.exe cl Security /e:false
In addition to the above, Black Hunt will perform a large amount of changes to Windows, including disabling Microsoft Defender, adding new users, disbaling System Restore, and disabling Task Manager and the Run command.
While all Windows devices should be restored after a malware infection, those infected with Black Hunt will be fairly unusable until Windows is reinstalled.
When encrypting files, the ransomware encryptor will append an extension in the format [unique_id].[contact_email].Hunt2 (new versions) or [unique_id].[contact_email].Black (old versions).
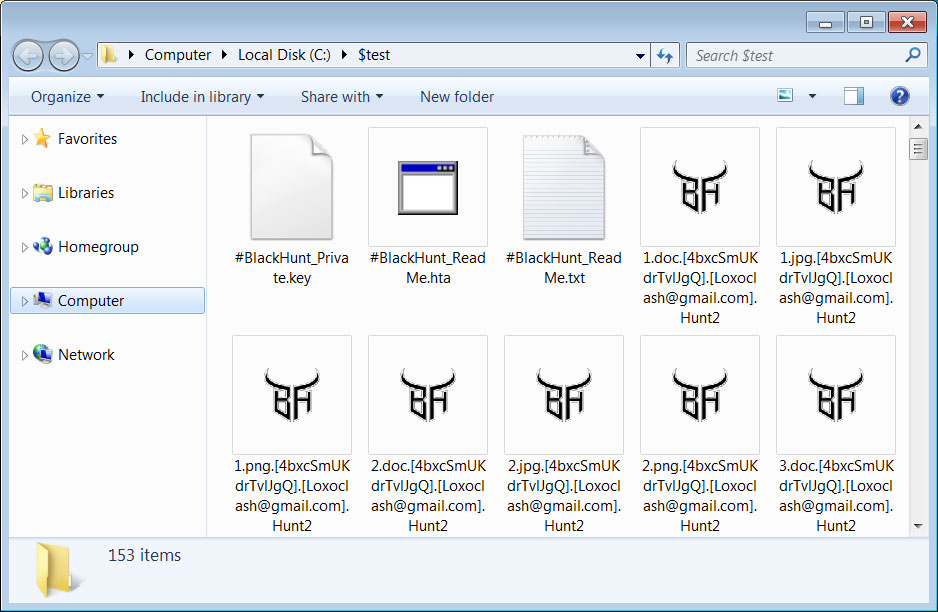
Source: BleepingComputer
In every folder, the encryptor will create ransom notes named #BlackHunt_ReadMe.hta and #BlackHunt_ReadMe.txt, which contain information about the attack and email addresses that can be used to contact the threat actors.
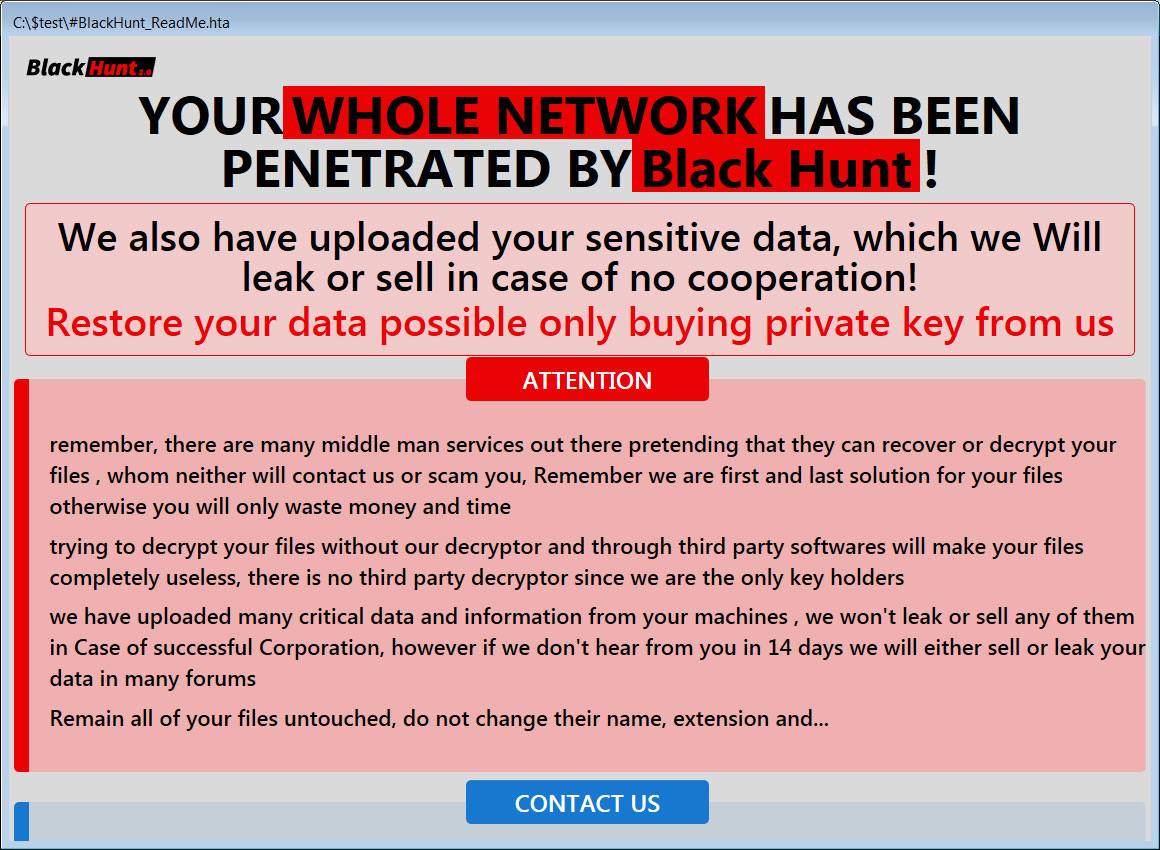
Source: BleepingComputer
While the ransom notes claim that the hackers steal data during attacks, there have not been any known instances of the ransomware operation leaking stolen data.
Furthermore, a Tor site listed in the HTML version of the ransom note does not work and appears fake.
However, as the threat actors had full access to encrypted devices, it is safer to assume that the data was exposed during attacks.