Kiddowares ‘Parental Control – Kids Place’ app for Android is impacted by multiple vulnerabilities that could enable attackers to upload arbitrary files on protected devices, steal user credentials, and allow children to bypass restrictions without the parents noticing.
The Kids Place app is a parental control suite with 5 million downloads on Google Play, offering monitoring and geolocation capabilities, internet access and purchasing restrictions, screen time management, harmful content blocking, remote device access, and more.
Researchers at SEC Consult have found that the Kids Place app versions 3.8.49 and older are vulnerable to five flaws that could impact the safety and privacy of its users.
The five security issues are the following:
- User registration and login actions return the unsalted MD5 hash of the password, which can be intercepted and easily decrypted. MD5 hashes are no longer considered cryptographically secure, as they can be brute-forced using modern computers.
- The customizable name of the child’s device can be manipulated to trigger an XSS payload in the parent web dashboard. Children or attackers can inject malicious scripts to execute on the parent’s dashboard, achieving unauthorized access. The issue has received the identifier CVE-2023-29079.
- All requests in the web dashboard are vulnerable to cross-site request forgery (CSRF) attacks. The attack requires knowledge of the device ID, which is obtainable from the browser history. The issue has received the identifier CVE-2023-29078.
- An attacker could exploit the app’s dashboard feature, originally intended for parents to send files up to 10MB to their child’s device, to upload arbitrary files to an AWS S3 bucket. This process generates a download URL which is then sent to the child’s device. No antivirus scan takes place on the uploaded files, so these can contain malware.
- The app user (child) can temporarily remove all usage restrictions to bypass parental controls. Exploiting the flaw, tracked as CVE-2023-28153, does not generate a notification to the parent, so it goes unnoticed unless a manual check is performed on the dashboard.
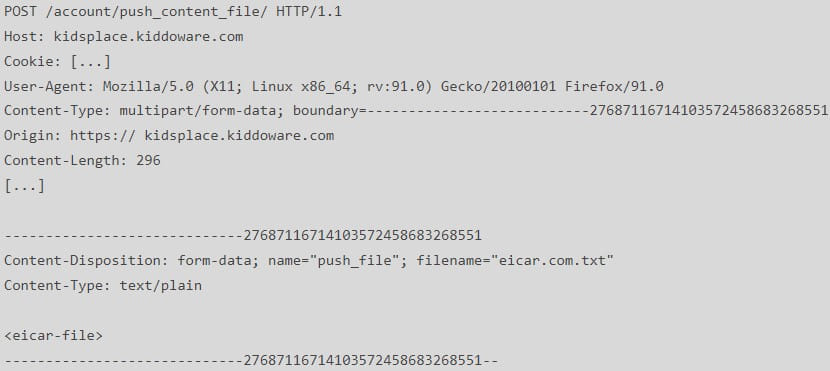
SEC Consult’s report contains proof-of-concept requests or step-by-step instructions on exploiting the above issues, making it easy for threat actors to exploit the vulnerabilities on older versions of the apps or for children to bypass restrictions.
Therefore, it is essential to update to a secure version of the app, which is 3.8.50 or later.
The analysts discovered the flaws on November 23, 2022, while testing Kids Place 3.8.45 and reported it to the vendor, Kiddoware.
The vendor eventually addressed all problems with version 3.8.50, released on February 14, 2023.
App users can update to the latest version by opening the Google Play store, tapping their account icon, selecting ‘Manage apps & device,’ and tapping on ‘Check for updates.’
Alternatively, long-press the app’s icon and then select App info → App details → Update.
