Cybersecurity researchers have uncovered a sophisticated Linux malware campaign exploiting the critical React2Shell vulnerability (CVE-2025-55182) to deploy multiple post-exploitation payloads.
A newly identified backdoor dubbed “PeerBlight” that leverages the BitTorrent DHT network for resilient command-and-control communications.
CVE-2025-55182, publicly disclosed on December 3, 2025, is a critical-severity unauthenticated remote code execution vulnerability affecting React Server Components with a CVSS score of 10.0.
The vulnerability stems from insecure deserialization in React Flight protocol processing, allowing attackers to execute arbitrary code through a single malicious HTTP request.
Threat actors have been actively exploiting this vulnerability since December 4, 2025, targeting organizations across sectors, including construction and entertainment.
The exploitation campaigns demonstrate both automated scanning and manual post-exploitation activities, with attackers deploying multiple malware families depending on the compromised environment.
PeerBlight: BitTorrent-Powered Backdoor
The most notable discovery from these campaigns is PeerBlight, a Linux backdoor that implements a full-featured command-and-control framework with unique resilience capabilities.
The attacker also executed a command to test shell code execution (echo $((41*271))), followed by discovery commands such as “whoami” and “hostname” to enumerate user context and system information.
The malware uses the BitTorrent Distributed Hash Table network as a fallback C2 mechanism, making it extremely difficult to neutralize through traditional domain takedowns.
PeerBlight establishes persistence through multiple mechanisms depending on privilege level. When executed with root access, it installs a systemd service named “systemd-agent.service” disguised as a legitimate system daemon.
For non-root users, it creates hidden directories mimicking systemd’s PrivateTmp naming convention and copies itself as “softirq”.
The backdoor implements sophisticated process masquerading by overwriting its argv in memory to appear as “[ksoftirqd]”, mimicking legitimate kernel soft interrupt handler threads.
On initial execution, PeerBlight overwrites argv[0] in memory to hide its original path (e.g., /tmp/backdoor) and replaces it with [ksoftirqd].
![PeerBlight overwrites argv[0] and calls prctl() to masquerade as [ksoftirqd].](https://cdn.builder.io/api/v1/image/assets%2F3eb6f92aedf74f109c7b4b0897ec39a8%2F6fb75cf79f694fa3a4d4acfbb670a6a1?format=webp&width=1600)
This technique modifies both /proc/pid/cmdline and /proc/pid/comm, ensuring the malicious process appears legitimate across different system monitoring tools.
BitTorrent DHT Infrastructure
PeerBlight’s most innovative feature is its BitTorrent DHT fallback mechanism. The backdoor bootstraps into the DHT by connecting to legitimate BitTorrent infrastructure including router.bittorrent.com, router.utorrent.com, and dht.transmissionbt.com.
Upon joining the network, it registers itself with a node ID beginning with the hardcoded prefix “LOLlolLOL”, serving as a botnet identifier.
Active scanning of the BitTorrent DHT network confirmed over 60 unique nodes with the LOLlolLOL prefix distributed across residential ISPs worldwide.
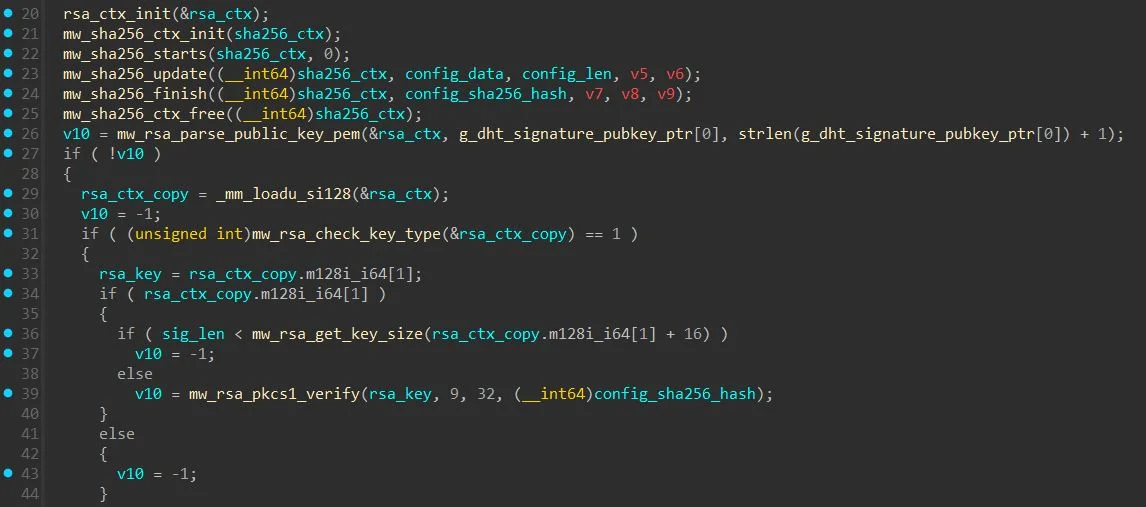
The configuration distribution protocol requires valid client version verification and includes RSA signature validation to prevent unauthorized parties from hijacking the botnet through fake configurations.
Researchers successfully extracted a live configuration from the DHT network dated October 30, 2025, revealing an active C2 server at 49.51.230[.]175:9898 hosted on Tencent Cloud infrastructure, confirming the campaign continues to distribute updated C2 actively addresses through the peer-to-peer network.
The tool provides comprehensive remote access capabilities including SOCKS5 proxy for network pivoting, TCP proxy for generic port forwarding, HTTP proxy with traffic manipulation features, FTP proxy for file transfers, and MSTSC for tunneling Remote Desktop Protocol connections.
The telnet server component spawns on port 2323 by default, providing interactive shell access to authenticated attackers.
Security teams also identified ZinFoq, a Go-based post-exploitation implant featuring interactive reverse shells, SOCKS5 proxy for network pivoting, and timestomping capabilities for anti-forensics.
The malware communicates with C2 infrastructure at api.qtss[.]cc using hex-encoded payloads and masquerades as Safari on macOS through its User-Agent string.
A Kaiji botnet variant was observed combining DDoS capabilities with persistence mechanisms and hardware watchdog abuse.
The malware opens /dev/misc/watchdog and writes null bytes continuously, forcing system reboots if the payload is killed, after which persistence mechanisms automatically restart it.
Mitigations
CVE-2025-55182 affects versions 19.0, 19.1.0, 19.1.1, and 19.2.0 of react-server-dom-webpack, react-server-dom-parcel, and react-server-dom-turbopack packages.
Organizations must immediately update to patched versions 19.0.1, 19.1.2, or 19.2.1. For Next.js applications affected by the downstream CVE-2025-66478 (now rejected as duplicate), Vercel has released the fix react2shell package.
Security teams should monitor for exploitation indicators including unauthorized systemd services, processes masquerading as kernel threads like [ksoftirqd], unexpected BitTorrent DHT traffic, and outbound FRP connections.
Network defenders should implement egress filtering to prevent reverse proxy tunneling and monitor for connections to identified C2 infrastructure including 185.247.224[.]41:8443, 49.51.230[.]175:9898, and associated domains.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.


