The Gotham Stealer has emerged as a new threat in the murky depths of the dark web. Formerly known as the Pirate Stealer, this information-stealing entity possesses a robust arsenal of features and capabilities. This is an advanced information-stealing tool.
It is equipped with the ability to execute various functions like Discord Injection, Startup Injection, Wallets Stealing, Browser Data Extraction, System Information Harvesting, Auto-Parsed Cookies, and a plethora of other information stealing functionalities.
The information stealer can also act as a Roblox Session Stealer, Steam Stealer, Minecraft Stealer, and Process Hider and prides itself on its unwavering undetectability (FUD).
What sets this information stealer apart are its screen-watching and screen-clicking functionalities, granting users unprecedented control over the victim’s screen.
Now available on the dark web
The actors behind this digital tool took to their Telegram channel to announce the return of the Pirate Stealer rebranded as Gotham Stealer, stating, “Hello, as team of Pirate Stealer, we announce that we are reopening Pirate, coming back as Gotham (developed by Sabo).”
According to the GitHub repository, the Pirate Stealer was hailed as a “multi-purpose Discord logger with endless features,” earning it a reputation for having one of the most sophisticated and reliable tools of its kind.
At its core, this Information Stealer is a Discord-centric malware with advanced features.
Discord, a widely used instant messaging platform, became a prime target for cybercriminals due to its surging popularity. Consequently, year 2023 witnessed a sharp rise in malware attacks targeting the platform.
While GitHub harbors a slew of similar information stealers, the newly rebranded information Discord Stealer distinguishes itself with an expanded repertoire of features, making it one of the hottest item on dark web forums.
Gotham Stealer boasts impressive features
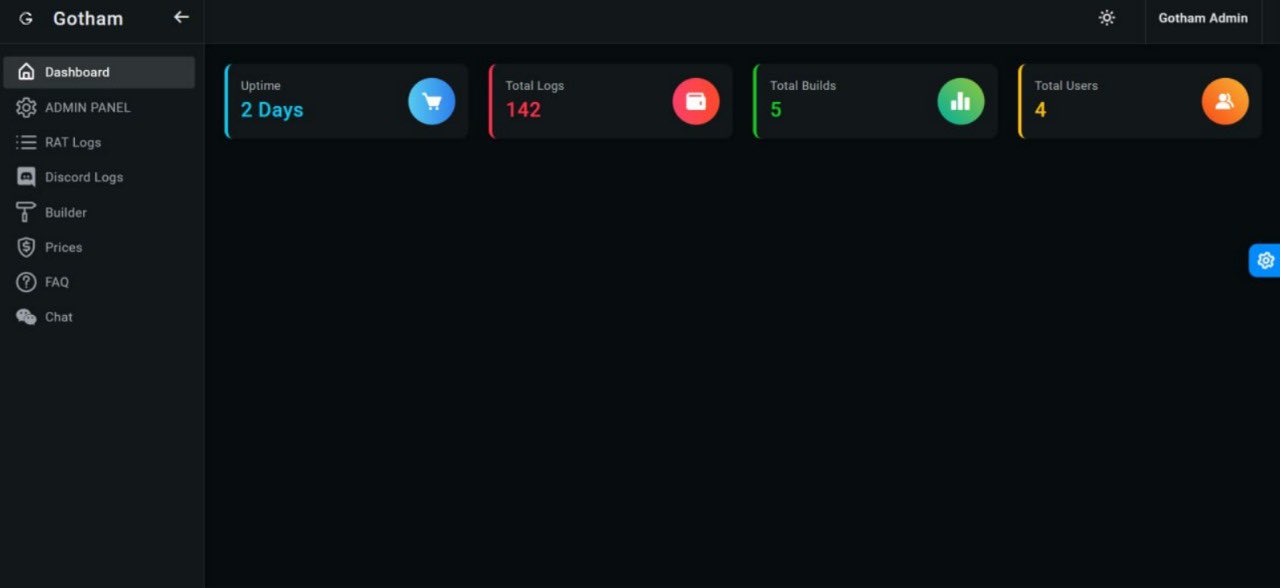
What sets this malware further apart is its sleek and intuitive dashboard, boasting a graphical user interface. Within its arsenal lies an admin panel, RAT logs section, Discord logs, Builder, FAQ, and a chat function.
This user-friendly interface empowers individuals to craft tailored projects, including the creation of Discord bots with customizable panels.
This flexibility grants users the power to decide whether they wish to terminate Discord sessions or log out victims when generating their .exe files.
The Gotham Stealer, in essence, belongs to the notorious category of information stealer-type malware. Crafted with the explicit purpose of exfiltrating information from compromised devices, it has found its way into the underground markets.
Upon infiltration, the Information Discord Stealer commences its operation by gathering crucial device data, including details like device name, hardware specifications, and operating system version. The malware’s primary focus lies in extracting data from browsers and other installed applications.
From browsers, the Stealer targets internet cookies and stored login credentials, including usernames and passwords. Discord, a favored platform for gamers and communicators alike, is a prime objective, where it aims to snatch passwords, 2FA codes, and other sensitive data.
The Information Stealer has been spotted for sale on hacker forums, highlighting that its distribution hinges on the whims of cybercriminals.
Typically, malware infiltrates systems through deceptive means like phishing and social engineering tactics. These codes often masquerade as innocuous files, be they executables, archives, documents, or scripts.
Conclusion
The emergence of Gotham Stealer introduces a potent and versatile information-stealing threat. Its user-friendly interface and adaptability make it a formidable adversary. As it circulates on dark web forums, vigilance and robust cybersecurity practices are crucial in mitigating this evolving threat.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
