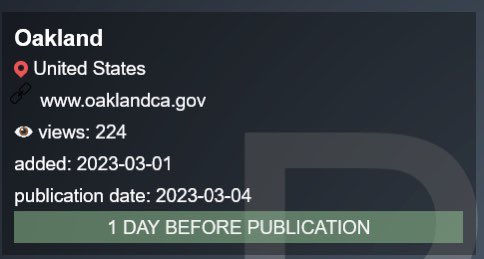
Play ransomware group has claimed responsibility for the attack on Oakland City, California.
According to a post on the ransomware group’s leak site, Oakland municipality was added as a victim on March 1. The group threatens to publish the leaked data on March 4 unless the ransom was paid. The post ended with the line, “1 DAY BEFORE PUBLICATION” suggesting that the exfiltrated data from the city’s government systems would be leaked publicly in a day.
The city’s IT systems were down on February 8, prompting the city administration to concede that it was a ransomware attack. Within days, the administration declared a local state of emergency on February 14.
Despite concerns raised by the local police department regarding response delays, the city assured residents that emergency services, such as the fire department and 911 dispatch, remained unaffected.
To report non-emergency issues, users were advised to use online file reports. The attack also affected government services from telephone services to tax and fine filing systems.
According to the latest update from the civic body, it is making “persistent efforts” to test and revive the remaining affected systems.
City of Oakland ransomware attack: Timeline
February 10
The civic body conceded that the network outage that began on February 8 was indeed a ransomware attack. “The Information Technology Department is coordinating with law enforcement and actively investigating the scope and severity of the issue,” the disclosure said.
February 13
Several civic services are affected, as the City took the network offline to contain the attack. The administration commissioned a “leading forensics firm” for incident response and analysis and “additional cybersecurity and technology firms” for remediation and recovery.
February 14
Interim City Administrator G. Harold Duffey declared a local state of emergency, as Oakland grappled with network outage that took several services including phone lines within the city down or out.
February 15
The city administration closed several office and service buildings, as the facilities to collect payments, process reports, and issue permits and licenses went offline. “We encourage the public to email the service counters they want to visit before coming to City buildings,” the administration advised.
February 16
The city administration declared a 45-day extension for paying Business Tax License and assured that it will not impose a late fees until April 17. “We continue working nonstop to safely restore systems and bring impacted services back online as quickly as possible. However, this process – done correctly – will take time to complete,” the administration announced.
February 20
The IT Department was able to restore access to public computers, and scanning, printing, copying and internet service at the city libraries, and wireless internet throughout the local government facilities. Critical Public Safety services were also restored.
February 22
Work continues on restoring public facing systems like business tax online payments, permitting, contracting and work order. The city phone system, Parking Citation Assistance Center, Business Tax Licenses, city permit permits application etc. are still down.
February 28
Phone line, contracting and funding systems, and permits services are back, but Parking Citation Assistance Center and the business tax online payments system still inaccessible. “Taxpayers will be granted a 45-day extension from the March 1 due date to pay without incurring penalties, interest, and late fees,” the administration reiterated.
The ransomware gang’s playbook
Play ransomware gang is notorious for targeting local administrations and civic bodies.
It’s recent attack on the city of Antwerp, Belgium, was in the cybersecurity news due to its unconventional encryption method. Digipolis, the IT management company for Antwerp, fell victim to Play, leading to disruptions in the city’s email, phone, and IT services.
It was shortly followed by an attempt on on Empresa Argentina de Soluciones Satelitales Sociedad Anónima, usually known simply as ARSAT, Argentina’s state-owned telecommunications company.
According to Trend Micro’s assessment, Play Ransomware borrows from the playbooks of Hive and Nokoyawa and shares similarities with them, indicating that they are operated by the same group of people.
The ransomware earns its name from its unique extension ” .play” that it adds after encrypting files. Additionally, the ransom notes feature the term “PLAY” along with the group’s email contact. In the latest attack, the heading was “PLAY NEWS.”
Despite similarities with Hive and Nokoyawa, Play Ransomware employs AdFind, a command-line query tool, to gather information from Active Directory (AD) during discovery, as reported by Trend Micro.