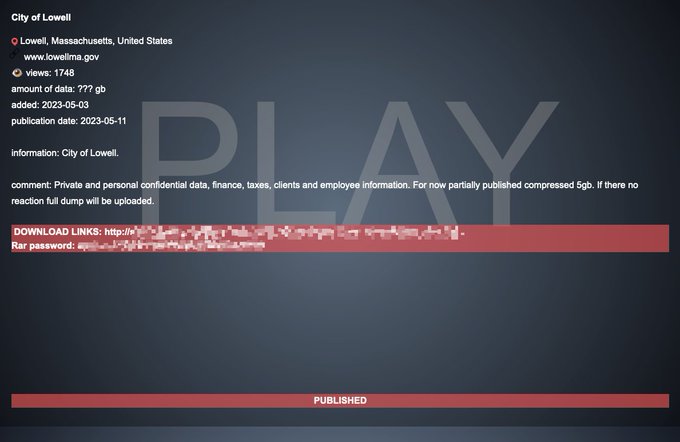
The Play ransomware group has leaked 5GB of pilfered data allegedly from the City of Lowell cyber attack.
The official website of the City of Lowell has been functional with updates about the changes made to systems post the security incident.
Play ransomware group added the City of Lowell as its victim on May 5. The group claimed then that is has access to passports, IDs, finance, payroll, department documents, budget, and other confidential information.
In a post on their leak site, Play ransomware group stated that they will leak more data if their demands were not met.
The City of Lowell cyber attack details
The city also known as the ‘cradle of the American Revolution’ had its sensitive user data accessed and partially leaked on the dark web.
The Play ransomware group wrote that they have possession of the following information from the City of Lowell cyber attack:
- Private confidential data
- Financial information
- Details about taxes
- Client information
- Employee data
The post concluded with a link to the download allegedly to the database stolen from the City of Lowell cyber attack with a Rar password.
What the City of Lowell has announced so far
The City of Lowell’s social media platforms has been regularly updated with messages for readers about the ongoing investigations and developments regarding ‘interruptions in technology services’, as it has been called.
On April 24, an update on the Facebook page of the city read, “Please be aware that City Hall is experiencing an interruption in technology services, which is impacting a variety of systems — including our phones.”
On April 25, the official website published an alert titled “Status of City Networks,” that stated that the cyber-related incident likely began early Monday morning on April 23. The systems were isolated post the incident.
Following this, servers, networks, phones, and other systems were rendered inaccessible.
However, on April 27, the City of Lowell’s Management Information Systems Department (MIS) enabled the telephone services while working on other restoration works due to the cyber incident.
Statements from experts, and officials about the City of Lowell cyber attack
Threat Analyst Brett Callow addressed the data leak on the dark web and said, “The info is out there, and while at the moment it’s on the dark web, there is no way knowing where else it may appear, or when it may appear,” The Sun reported.
Brett further said that it is unknown how many individuals have accessed the leaked data.

About ransomware attacks Brett said, “Ransomware attacks have two parts to them. The first part is that the hackers steal a copy of the data. Then they encrypt and lock the system from those that they’ve stolen. Then they ask for a ransom that covers two things: Firstly, unlocking the locked systems, and secondly, destroying that stolen data. Or supposedly destroying it.”
The FAQ page of the Play ransomware group detailed its modus operandi and answered some questions that threatened to leak system data if their demands were not met.

In an answer, the group wrote, “All customers are given a reasonable price, we study income, expenses, documents, reports and more before setting a price.”
Earlier, this May, MassHire Greater Lowell Workforce Board announced that they had received a grant of $2 million for the YouthWorks Employment and Training Program. This may have prompted the hacker collective to target the city.
The City of Lowell cyber attack is still under investigation as the City Manager Tom Golden confirmed. “At this time, Lowell continues to work with our partners in Federal and State law enforcement,” added Tom as reported on The Sun.
Lowell cyber attack: Latest in Play Book
The Lowell cyber attack is the latest in the playbook of Play ransomware group. Its recent victims include the City of Antwerp, Argentine judiciary, and the City of Oakland, USA.
Play ransomware is observed to adopt several tactics similar to those of Hive and Nokoyawa ransomware, such as the use of comparable file names and file paths for their respective tools and payloads.
Researchers at Trend Micro recently found indications suggesting a connection between the attackers behind Nokayawa and those behind Hive due to the numerous similarities in their attack chains.
Symantec’s threat hunter team reported last month that the Play ransomware group is using a customized network-scanning tool called Grixba to enumerate all computers and users in the domain.
Along with it, the ransomware gang uses a .NET executable that allows attackers to copy files from the Volume Shadow Copy Service (VSS), which are typically locked by the operating system.
According to researchers, “the use of proprietary tools… provides ransomware operators with greater control over their operations.”
By keeping their tools proprietary and exclusive, ransomware groups can maintain a competitive advantage and maximize their profits, as widely available tools can be reverse-engineered or adapted by other attackers, potentially weakening the effectiveness of the initial attack.
Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
