DDoS-for-hire service DigitalStress was taken down on July 2 in a joint law enforcement operation led by the United Kingdom’s National Crime Agency (NCA).
The Police Service of Northern Ireland also arrested its owner (known as Skiop) this month, and NCA agents infiltrated the communication services used to plan distributed denial-of-service (DDoS) attacks, collecting data on DigitalStress’s “customers.”
NCA will share this information with other law enforcement agencies to help with investigations targeting this criminal marketplace’s admins and users and to contact U.K. citizens who have used the platform.
“The disruption targeting digitalstress.su, a criminal marketplace offering DDos capabilities, was made in partnership with the Police Service of Northern Ireland,” the NCA says in a seizure banner displayed on the DigitalStress website.
“The National Crime Agency has collected substantial data from those who have accessed this domain. We will share this data with International Law Enforcement for action. Individuals in the UK who engaged with this site will be contacted by Law Enforcement.”
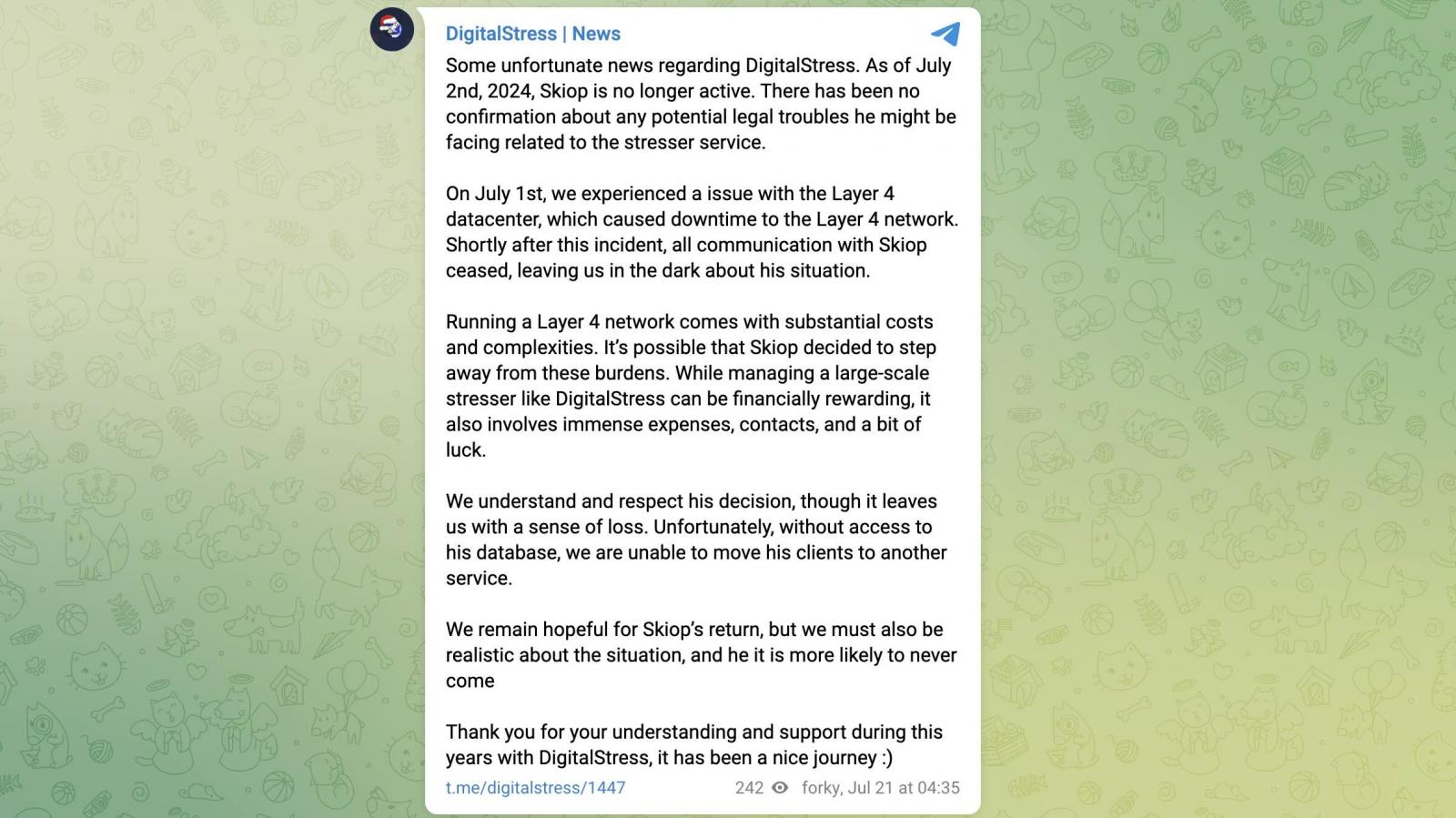
Others involved in the booter service confirmed on the operation’s Telegram channel that Skiop has been unreachable since July 2. They also warned against accessing the digitalstress[.]net because they believed it was a honeypot.
They also confirmed the service’s takedown, saying that “without access to his database, we are unable to move [..] clients to another service.”
“Booter services are an attractive entry-level cyber crime, allowing individuals with little technical ability to commit cyber offences with ease,” said Paul Foster, the head of NCA’s National Cyber Crime Unit.
“Anyone using these services while our mirror site was in place has now made themselves known to law enforcement agencies around the world.”
DigitalStress’ takedown and its owner’s arrest are part of a long-running and ongoing law enforcement effort known as Operation PowerOFF, which started in December 2018 with the seizure of 15 websites linked to DDoS-as-a-service platforms.
In December 2022, the Department of Justice seized 48 Internet domains linked to stresser platforms, charging six suspects with operating the booter services.
Six months later, in May 2023, the U.S. DOJ announced the seizure of 13 additional web domains linked to DDoS-for-hire services.
Last week, Spanish authorities also arrested three suspects linked to DDoS attacks against governments and organizations in NATO countries using DDoSia, a DDoS platform operated by pro-Russian hacktivists.
Active since August 2022, DDoSia has been using volunteers’ bandwidth to launch crowdsourced DDoS attacks against government organizations in Poland and Switzerland.
As cybersecurity firm Sekoia said in June 2023, the DDoSia platform saw a massive 2,400% growth, reaching over 13,000 users on its Telegram channel.




