A recent threat hunting session has revealed a sophisticated PowerShell script, named y1.ps1, hosted in an open directory on a Chinese server (IP: 123.207.215.76).
First detected on June 1, 2025, this script operates as a shellcode loader, employing advanced in-memory execution techniques to bypass traditional disk-based detection mechanisms.
The discovery, attributed to Shenzhen Tencent Computer Systems Company Ltd., highlights a growing trend of stealthy post-exploitation tools leveraging cloud infrastructure and reflective loading to remain undetected.
Stealthy Malware Deployment
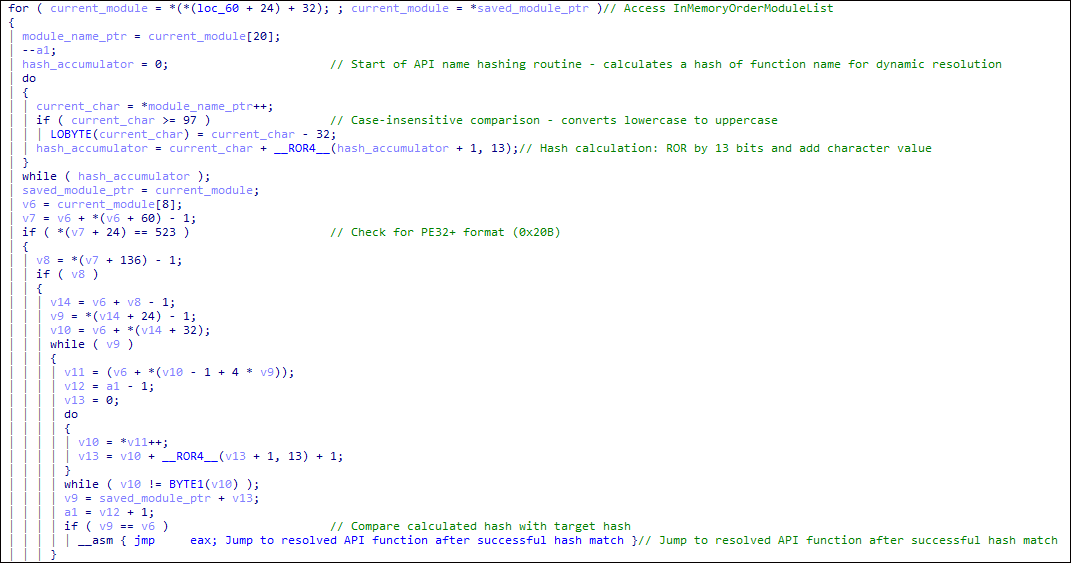
Detailed analysis shows the script dynamically resolves Windows API functions, decrypts embedded shellcode using XOR operations with a key of 35, and executes malicious payloads directly in memory via VirtualAlloc, rendering it nearly invisible to conventional antivirus solutions.
Further investigation into the script’s behavior uncovered connections to a second-stage command-and-control (C2) server hosted on Baidu Cloud Function Compute (y2n273y10j[.]cfc-execute[.]bj.baidubce[.]com).
The shellcode employs API hashing to obfuscate function calls, crafting unique hashes for Windows APIs like LoadLibraryA and InternetOpenA, and uses forged User-Agent strings mimicking legitimate browser traffic to evade network monitoring.
Cobalt Strike Infrastructure
The final payload communicates with a Cobalt Strike Beacon at IP 46.173.27.142, tied to Beget LLC in Russia, with SSL metadata explicitly referencing “Major Cobalt Strike” as the certificate subject.
This infrastructure, combined with reflective DLL injection for in-memory execution, aligns with known Cobalt Strike deployment patterns often exploited in post-exploitation phases by threat actors using cracked versions of the framework.
Beyond China and Russia, additional indicators of compromise (IOCs) point to servers in the United States, Singapore, and Hong Kong, suggesting a distributed network leveraging global cloud platforms for resilience and anonymity.
The use of short-lived IPs and ephemeral C2 nodes further complicates attribution and mitigation efforts.
According to the Report, This finding underscores the quiet yet effective combination of evasion techniques.
The PowerShell loader, discovered via tools like Attack Capture File Manager and code searches for reflective execution functions such as “func_get_delegate_type,” represents a broader trend of financially motivated threat campaigns.
Mitigation requires stringent PowerShell execution policies, robust endpoint detection and response (EDR) solutions to detect in-memory attacks, and vigilant monitoring of SSL certificates bearing hallmarks like “cobaltstrike.”
Blocking known malicious IPs and domains, alongside restricting internet access from sensitive systems, is critical to countering such threats.
Indicators of Compromise (IOCs)
| Type | Value |
|---|---|
| PowerShell Script SHA-256 Hash | cdd757e92092b9a72dec0a7529219dd790226b82c69925c90e5d832955351b52 |
| C2 Server Domain | y2n273y10j[.]cfc-execute[.]bj.baidubce[.]com |
| C2 Server IP | 46.173.27.142 |
| Host IP (Open Directory) | 123.207.215.76 |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
