The rise of Pro-Russian hacker groups in recent years has posed a looming threat to the security world.
Among these groups, UserSec has recently announced its collaboration with eight other Pro-Russian hacker groups, forming a powerful alliance.
In a tweet, threat intelligence service provider Falcon Feed shared details about the UserSec’s alliance.
The announcement was accompanied by two images in English and Russian from a threat actor’s post, showcasing the support and cooperation between these Pro-Russian groups.
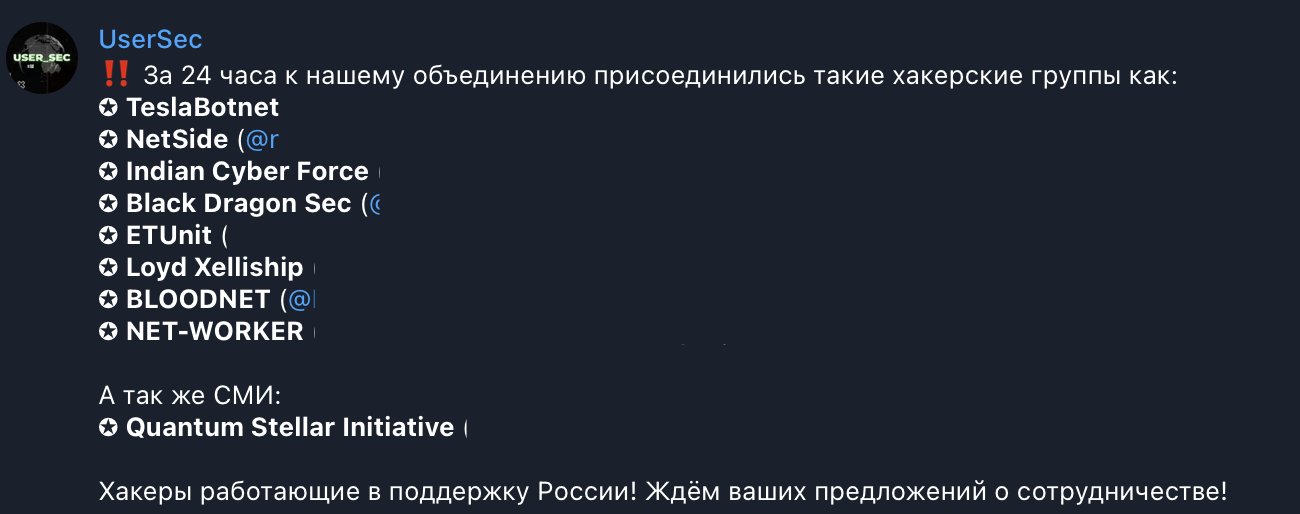
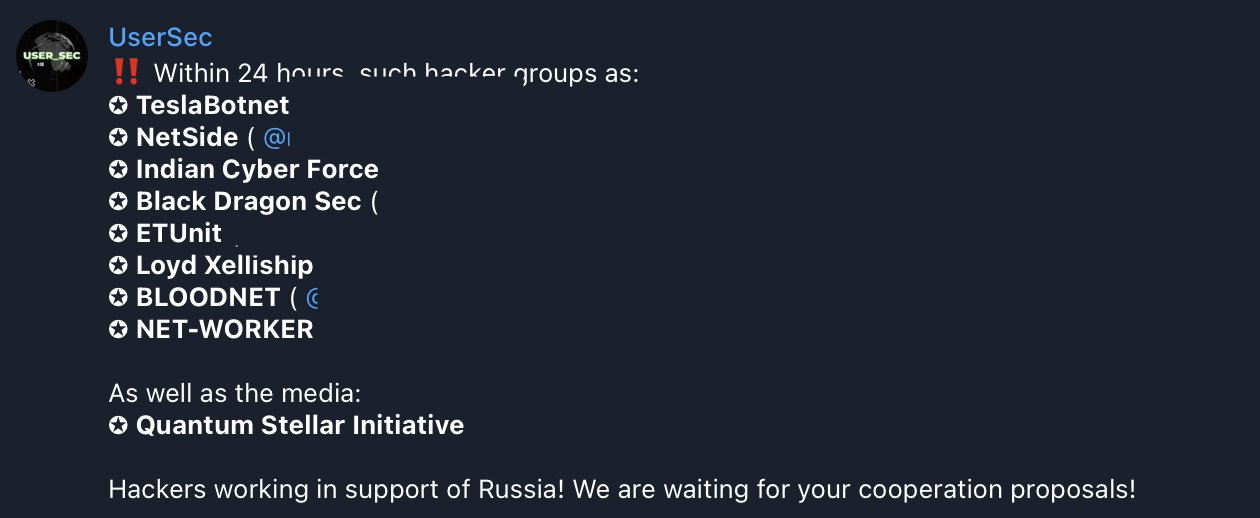
The newly formed alliance includes TeslaBotnet, NetSide, Indian Cyber Force, Black Dragon Sec, ETUnit, Loyd Xelliship, BLOODNET, and NET-WORKER.
While their exact motives remain unknown, it is believed that this collaboration between Pro-Russian hacker groups aims to target NATO.
Rise of Pro-Russian Hacker Groups
The images offer a glimpse into the world of the threat actors, revealing UserSec’s involvement in promoting Pro-Russian agendas.
Alongside UserSec, another group named NoName057(16) has been working closely with other threat actors to further these agendas.
Moreover, in May 2023, UserSec declared its intention to launch a cyber campaign aimed at defacing websites belonging to NATO member nations.
The group announced its official UserSec Telegram channel, initially reported by the threat intelligence platform Falcon Feed.
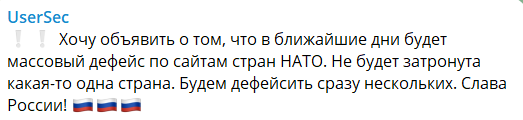

The translated message from the post reads, “I want to announce that in the coming days, there will be a massive defacement of the websites of NATO countries. No one country will be affected. We will deface several at once. Glory to Russia!”
UserSec operates independently and claims not to receive orders from the state. The group identifies itself as an entity working for the betterment of Russia, intending to attack Europe, the West, and all NATO countries.
This declaration underscores their determination to carry out cyber operations that have far-reaching implications.
KillNet: The Pro-Russian hacker group targeting NATO
KillNet, one of the most prominent Pro-Russian hacker groups, initiated its campaign against NATO last month. UserSec’s recent collaboration with KillNet suggests a growing trend of hacker groups joining forces to amplify their impact.
KillNet had previously leaked the personal information of over 4,000 individuals affiliated with NATO on a dedicated Telegram channel created for their NATO-targeted attacks.
The timing of the attack coincided with the NATO Secretary General’s visit to Ukraine, causing further concerns about the group’s intentions.
Following the leak, KillNet’s leader declared their transformation into a private mercenary group, offering hacking services to private organizations and state-sponsored entities.
Cybersecurity agencies from the Five Eyes nations in April issued a warning, urging critical infrastructure entities to prepare for potential attacks from groups supported by or sympathetic to the Kremlin.
This advisory came amidst significant Western opposition to Russia’s invasion of Ukraine.
The joint alert, issued by cybersecurity authorities in the United States, United Kingdom, Australia, Canada, and New Zealand, includes specific technical information about over a dozen Russian state-sponsored hacking groups and cybercriminal organizations aligned with Russia.
“We know that malicious cyber activity is part of the Russian playbook, which is why every organization – large and small – should take action to protect themselves during this heightened threat environment. ,” CISA Director Jen Easterly said in a statement.
In addition to the collaboration with KillNet, UserSec has actively supported their operations. They participated in a distributed denial-of-service (DDoS) campaign against the U.S. medical sector.
Another group, Anonymous Sudan, also expressed its support for campaigns against NATO members, with UserSec claiming to have collaborated with them to support KillNet’s attacks.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
