The pro-Russian hacktivist collective NoName057(16) has emerged as a notable participant in a coordinated wave of cyberattacks targeting Israeli infrastructure during the October 7 anniversary period.
The group claimed responsibility for multiple distributed denial-of-service (DDoS) attacks against government portals, financial institutions and online commerce platforms, marking a significant escalation in hacktivist operations aligned with pro-Palestinian cyber campaigns.
Between October 6 and 8, 2025, NoName057(16) conducted a series of DDoS attacks targeting Israeli government assets, including websites of political parties and municipal administrations.
This participation reaffirmed the group’s previously announced alliances with pro-Palestinian hacktivist networks, demonstrating a convergence of anti-Western and anti-Israeli cyber operations.
The broader hacktivist mobilization during this period saw over 57 DDoS attack claims recorded on October 7 alone, representing more than 14 times the daily average observed throughout September 2025.
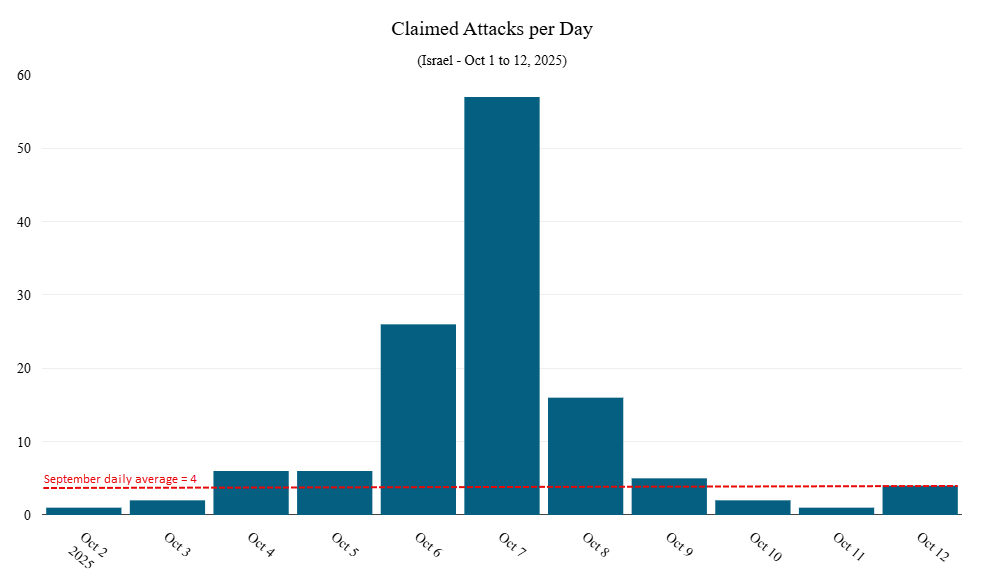
The average number of attack claims per week increased by nearly 200 percent compared to the weeks preceding October 7, highlighting the significant coordination among multiple threat groups responding to calls for cyber action.
Government and Commerce Sectors
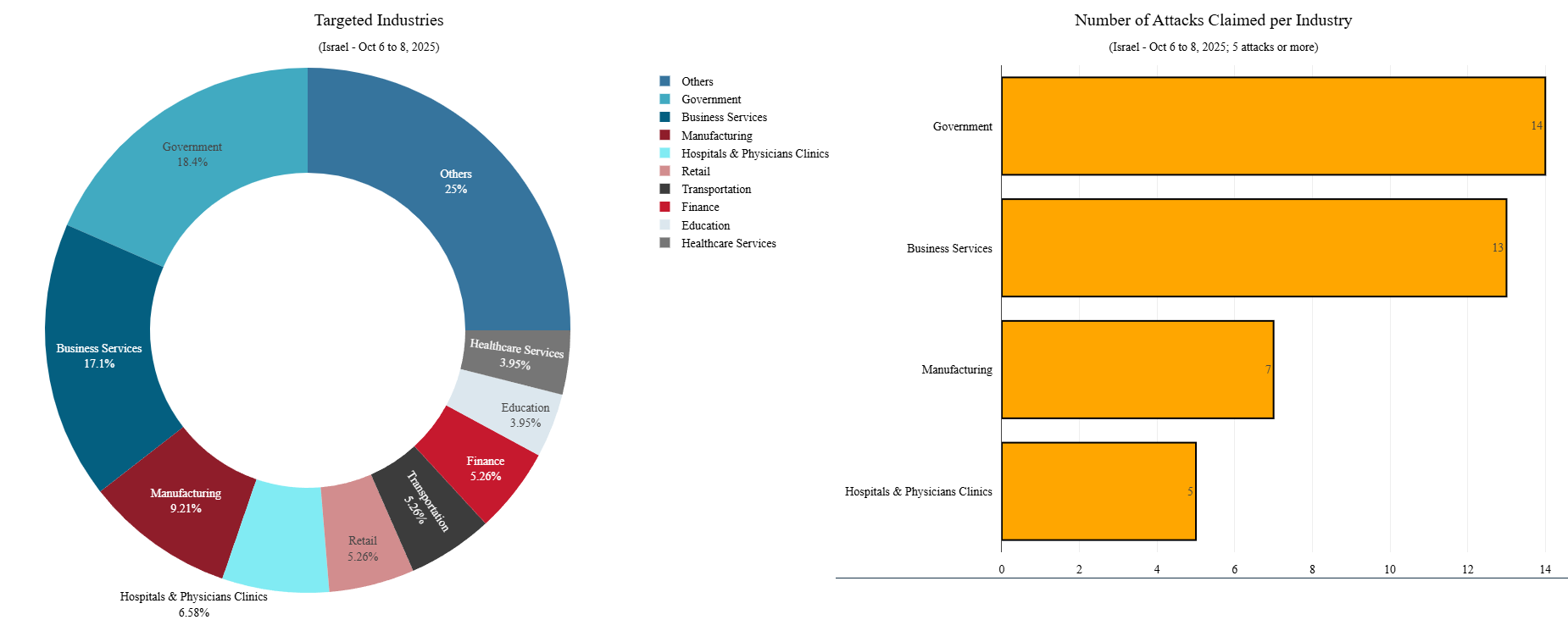
During the October 6-8 activity window, government portals emerged as the most frequently targeted sector, accounting for the largest share of claimed DDoS attacks.
Sylhet Gang primarily focuses on disseminating narratives, coordinating like-minded hacktivist groups and amplifying attack claims rather than executing attacks directly.
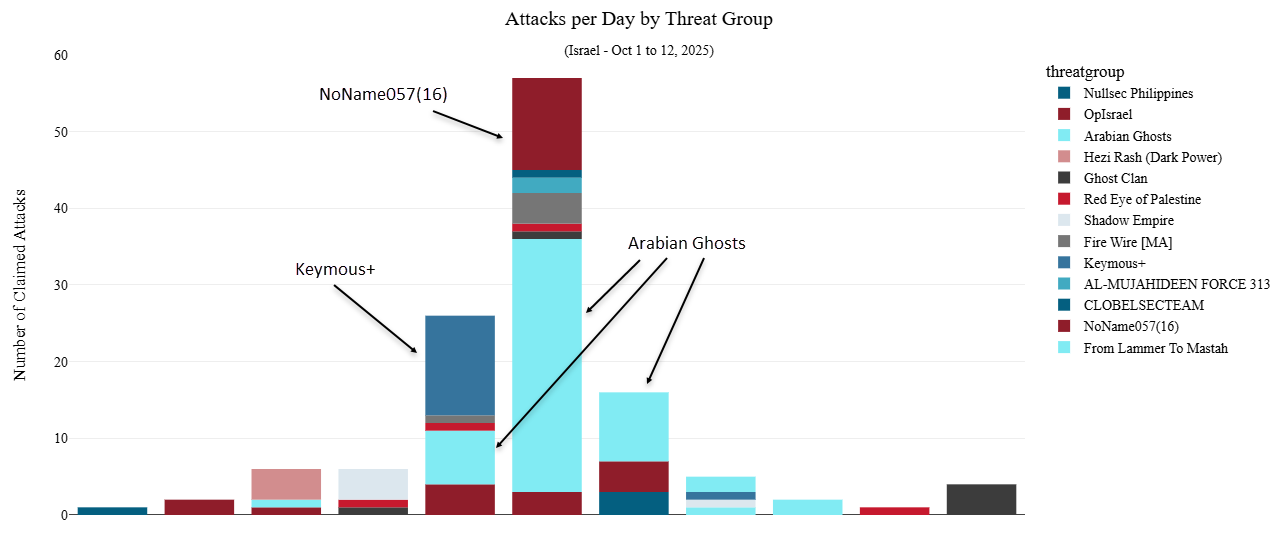

This was closely followed by business and e-commerce websites, reflecting the hacktivists’ strategic intent to disrupt both symbolic government services and high-visibility commercial operations that impact public access and economic activity.
Financial services also represented a significant portion of targeted sectors, comprising roughly seven percent of total attack claims alongside education, healthcare, manufacturing and retail.
The distribution of attacks across these multiple sectors suggests an opportunistic targeting approach designed to maximize perceived operational impact and generate widespread disruption across Israel’s digital infrastructure.

NoName057(16) has historically leveraged its DDOSIA volunteer network for crowdsourced DDoS operations, blending political opportunism with technical persistence.
The group recorded 12 claimed DDoS attacks during this three-day window, positioning itself as the only Russian-aligned hacktivist collective to participate in the pro-Palestinian campaign.
The group’s methodology consistently includes sharing check-host verification links to substantiate attack claims, establishing a pattern of public proof-sharing that distinguishes its operations from less verifiable hacktivist activities.
Beyond Israeli targets, NoName057(16) extended its October campaign to include German websites, which the group characterized as pro-Israeli in its messaging.
This cross-targeting pattern reflects the collective’s broader information warfare agenda, where geopolitical alignment dictates target selection.
By attacking both Israeli and Western European infrastructure, NoName057(16) positioned itself as part of a coalition of anti-Western actors, reinforcing narratives of solidarity with other ideologically aligned hacktivist groups.
Hacktivist Mobilization
This period functions as a symbolic rallying point for pro-Palestinian and anti-Israeli groups globally, with renewed calls for coordinated cyber action amplified through Telegram channels and other communication platforms.
Each post was accompanied by the hashtags #OpIsrael and an Arabic tag translating to Al-Aqsa Flood. Al-Aqsa Flood is the codename used by Hamas and allied Palestinian armed groups for the October 7 attacks in 2023.

The October 7 anniversary has consistently served as a catalyst for increased hacktivist activity over the past two years.
The temporal correlation between public mobilization messages and subsequent attack waves demonstrates the strong mobilization effect within hacktivist ecosystems.
NoName057(16)’s participation in the October 7 campaign exemplifies how established pro-Russian hacktivist collectives exploit major geopolitical flashpoints to amplify visibility and reinforce ideological messaging.
The group continues to leverage major anniversaries and political events to conduct operations that blur the lines between cyber activism, information warfare and coordinated digital disruption targeting critical government and commercial infrastructure.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
