It has been observed that a new Proxyjacking campaign attack SSH servers and subsequently builds Docker services that share the victim’s bandwidth for money.
This is an active campaign that Akamai Security Intelligence Response Team (SIRT) has identified. Through this, the attacker uses SSH for remote access and malicious scripts that discreetly enroll target servers for peer-to-peer (P2P) proxy networks like Peer2Proxy or Honeygain.
.png
)
Additionally, it enables the attacker to make money from the excess bandwidth of an unaware victim using a small fraction of the resources needed for crypto-mining and with less risk of detection.
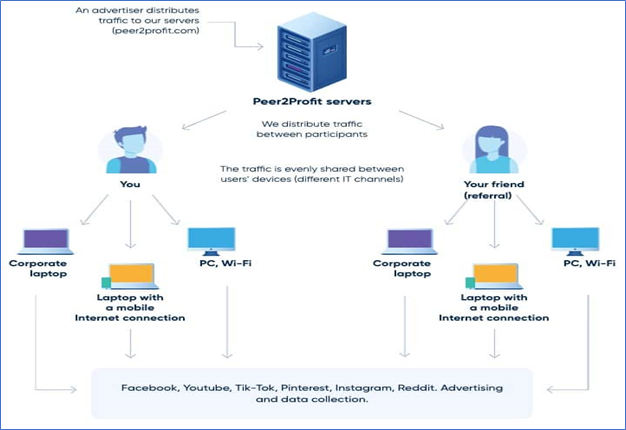
What is Proxyjacking?
The most recent method for hackers to profit from hacked devices in both the corporate and consumer ecosystems is proxyjacking. Here, the attacker takes advantage of the victim’s unused bandwidth in addition to stealing resources.
“The victim’s system is covertly used to run various services as a P2P proxy node that the attackers have recently started to monetize through organizations such as Peer2Profit or Honeygain”, researchers explain.
Researchers added that it is a more stealthy alternative to crypto-jacking and has serious consequences that can worsen the problems caused by proxied Layer 7 assaults.
P2P Proxy Monetization Schemes
Peer2Profit and Honeygain, two P2P proxy monetization schemes with public Docker images that each had more than 1 million downloads, were identified in this campaign.
“In these cases of proxyjacking, the proxy is getting used by theoretically legitimate, but potentially unscrupulous, companies for purposes such as data collection and advertising,” researchers said.
These applications are advertised as voluntary services that allow consumers to offer up their idle internet bandwidth in return for cash; thus, they are not intrinsically dangerous.
The entire process is very simple; however, some of these businesses sometimes advise customers to install the software on their work PCs despite improperly verifying the origin of the IPs in the network.
When an application is launched without the user’s knowledge or agreement, effectively using their resources, the situation radically changes.
“The attacker, by commandeering multiple systems and their bandwidth, effectively amplifies their potential earnings from the service, all at the victims’ expense,” researchers explain.
The activity, according to Akamai, is intended to compromise vulnerable SSH servers and deploy a bash script that has been encrypted to download essential dependencies from a hacked web server, including the curl command-line tool by disguising it as a CSS file (“csdark.css”), among many others.
Therefore, as long as these incentives remain and businesses are ready to disregard the ethics of sourcing, criminal enterprises will be developed around utilizing these practices.
Mitigation
The accumulation of proxies has another feature that makes it particularly important and alarming: The one main drawback of crypto-jacking—the discovery via excessive CPU usage—is substantially eliminated by proxyjacking.
Proxyjacking can get around some of the detection techniques that were previously employed for crypto-jacking by using little CPU power and depending instead on unutilized internet bandwidth.
You should look into the intrusion, ascertain how the script was uploaded and launched, and carry out a thorough cleanup if you check your local operating Docker services and discover any unauthorized resource sharing on your system.
“AI-based email security measures Protect your business From Email Threats!” – Request a Free Demo.



