I was thrilled to catch up with Cyera during Black Hat USA 2024. Over 90% of the world’s data was created in the last two years – making data the fastest growing attack surface. Despite this, 70% of security leaders struggle to secure their data since they have no way to easily discover data across their environment, understand what data is most important, know the real time posture of their data security, nor the identities (both human and non-human) that have access to it.
“The world of data has changed tremendously. When we look at the latest trends this past year, generative AI rocking the boat, getting everyone excited, but also a bit scared, I think that the importance of being able to differentiate between the data that matters – the stuff that is proprietary to our enterprise, the stuff we do not want to find in some Gen AI service out there in the Internet, and the data that clutters – is greater than ever before.” – Yotam Segev, Co-founder and CEO of Cyera.
Cyera uses a combination of agentless and AI-backed technology to quickly discover data, classify it with 95% precision, determine the blast radius, then put necessary controls in place to prevent data risks, and accelerate response to data incidents – should they occur.
Data is the lifeblood of every organization today. Cyera is a data security platform that helps security leaders discover the sensitive data within their environment, protect data, comply with industry regulations, respond to threats and ultimately make data safely accessible to the business so they power AI adoption, cloud migration projects, M&A and divestitures and much more.
With its foundation in Data Security Posture Management (DSPM), Cyera developed one of the most trusted data discovery and data classification modules on the market (4.7 Gartner Peer Rating). The DSPM module uses API-based deployment within any SaaS, IaaS, PaaS or on-prem environment to activate within five minutes, scans the environment, and then continues to perform ongoing discovery of new datastores within the environment. In 24 hours, the environment is fully scanned and data classifications are provided to determine the criticality of the data based on a combination of pattern and AI-backed learned classifications. Given that 40% of customer data is unique to customers, the learned classifications enhance classification beyond normal pattern-based matching and help them classify data that they would not have been able to, given legacy classification methods. Once the discovery and classification is complete, the security team can then determine the overall posture of their environment. This includes full visibility into existing data exposure, any misuse, or data drifting. The live event feed provides near real-time updates of relevant data security events and ongoing detection of new data exposure of posture events.
“Cyera’s data discovery and AI-powered classification provides deep context and understanding of the data we are responsible for, as well as detailed insight and remediations for security, privacy, and compliance. With this simple extension of coverage to include on-premises databases and file shares, we now have for the first time a single solution for end-to-end visibility and control over all of our data, no matter where it resides,” said Mike Melo, LifeLabs’ Chief Information Security Officer.
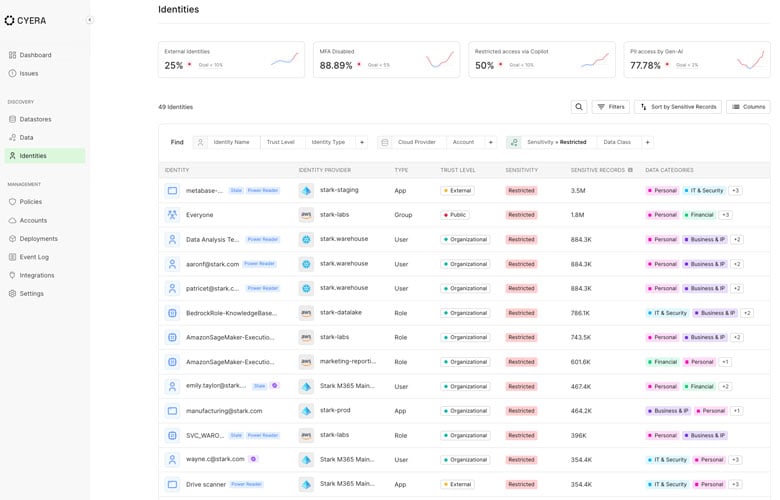
The platform then combines this posture with its ability to auto-discover the identities that exist with the customer environment – both human (i.e. employees, customers, partners) as well as non-human identities aka “NHI” (i.e. AI services, SaaS apps, Services etc.), and determine their level of access to sensitive data (which the DSPM module provided). Given the high precision of the Cyera platform, identity access can reduce over privileged access from users and third-parties. NOTE: With AI Copilots like Microsoft Copilot, Salesforce Gemini, and AWS Sagemaker becoming more and more popular, understanding what sensitive data is accessible by these services is critical. But Cyera’s value expands beyond just its software, it also provides data security services. More recently, Cyera introduced its Cyera Incident Response Service, which makes an elite group of security pros available in times of need – like a data breach. The service helps understand the blast radius, develop a recovery plan, and determine the materiality of a data incident. This is why Cyera is one of the fastest growing software companies in the world.
“Cyera offers an enterprise data security solution that stands out in the industry,” said Pete Chronis, CISO of Paramount. “Its data classification accuracy, comprehensive technology coverage, and user-friendly interface surpasses similar solutions.”
Cyera helps customers protect their data by uncovering the sensitive data in their environment, reducing the impact of non-compliance, and helping security respond faster to data security. In doing so, not only does Cyera help to protect the business, but also empowers its leaders to use data to drive innovation.
For more information and a demo visit: https://www.cyera.io/demo. Find them on Twitter (X): @cyera_io #datasecurityposturemanagement #dataaccessgovernance #datasecurity #datadetectionandresponse
About the Author
 Gary Miliefsky is the publisher of Cyber Defense Magazine and a renowned cybersecurity expert, entrepreneur, and keynote speaker. As the founder and CEO of Cyber Defense Media Group, he has significantly influenced the cybersecurity landscape. With decades of experience, Gary is a founding member of the U.S. Department of Homeland Security, a National Information Security Group member, and an active adviser to government and private sector organizations. His insights have been featured in Forbes, CNBC, and The Wall Street Journal, as well as on CNN, Fox News, ABC, NBC, and international media outlets, making him a trusted authority on advanced cyber threats and innovative defense strategies. Gary’s dedication to cybersecurity extends to educating the public, operating a scholarship program for young women in cybersecurity, and investing in and developing cutting-edge technologies to protect against evolving cyber risks.
Gary Miliefsky is the publisher of Cyber Defense Magazine and a renowned cybersecurity expert, entrepreneur, and keynote speaker. As the founder and CEO of Cyber Defense Media Group, he has significantly influenced the cybersecurity landscape. With decades of experience, Gary is a founding member of the U.S. Department of Homeland Security, a National Information Security Group member, and an active adviser to government and private sector organizations. His insights have been featured in Forbes, CNBC, and The Wall Street Journal, as well as on CNN, Fox News, ABC, NBC, and international media outlets, making him a trusted authority on advanced cyber threats and innovative defense strategies. Gary’s dedication to cybersecurity extends to educating the public, operating a scholarship program for young women in cybersecurity, and investing in and developing cutting-edge technologies to protect against evolving cyber risks.
