A sophisticated multi-stage malware campaign leveraging living-off-the-land techniques and in-memory payload delivery has been discovered targeting Windows systems.
The attack employs Pulsar RAT, a full-featured remote access trojan combined with advanced stealer capabilities, using evasion techniques designed to bypass traditional security controls and maintain persistent access.
The infection chain begins with a hidden batch file that establishes persistence through the per-user Run registry key at HKCUSoftwareMicrosoftWindowsCurrentVersionRun.
The malware creates a hidden folder within %APPDATA%Microsoft with randomized naming conventions to avoid detection during casual system inspection.
The batch file registers itself using a benign-looking value name, ensuring automatic execution at every user logon without requiring elevated privileges.
This persistence stub copies itself to the hidden location and employs a retry loop for robustness, ensuring the malware survives system reboots.
The batch file extracts an embedded Base64-encoded payload marked by a predefined delimiter, decoding it into a PowerShell script stored in the %TEMP% directory.
This PowerShell stage executes with a bypassed execution policy and implements self-cleaning mechanisms to minimize forensic artifacts.
Investigation uncovered a sophisticated, multi-stage malware campaign leveraging living-off-the-land techniques and in-memory payload delivery to evade traditional security controls.
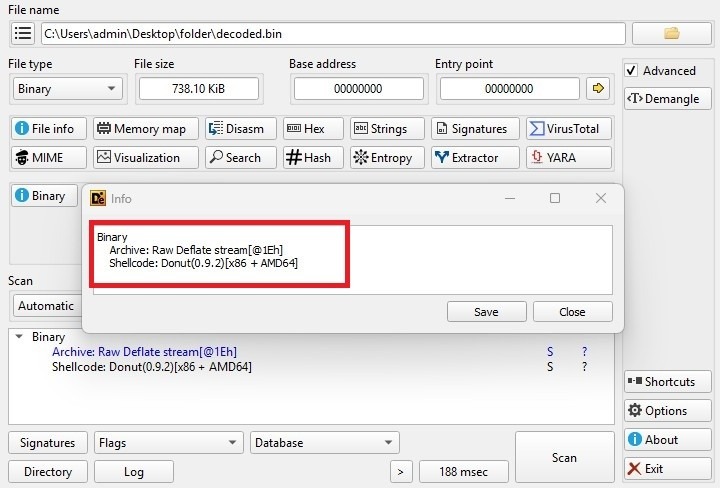
The decoded script contains a large byte array that undergoes bitwise XOR decryption, revealing Donut-generated shellcode designed for position-independent execution.
The PowerShell loader performs classic CreateRemoteThread process injection, utilizing Win32 APIs including OpenProcess, VirtualAllocEx, WriteProcessMemory, and CreateRemoteThread.
After an intentional 80-second delay intended to evade behavioral monitoring systems, the shellcode is written into allocated memory with PAGE_EXECUTE_READWRITE permissions.
The malware implements a watchdog mechanism that continuously monitors the injected process, automatically migrating to explorer.exe whenever the current host terminates, ensuring resilient persistence.
Advanced Anti-Analysis Capabilities
The decrypted payload reveals a heavily obfuscated .NET assembly implementing comprehensive anti-analysis protections.
The malware performs extensive virtualization, sandbox, and emulation detection checks before execution, targeting automated analysis environments commonly used by security researchers.
A background thread continuously monitors for injected threads, suspicious memory base addresses, and both managed and native debuggers, immediately terminating upon detection of tampering.
The malware employs user-mode anti-debugging through window enumeration, scanning active window titles for known reverse-engineering tools including x64dbg, WinDbg, dnSpy, and IDA.
Additionally, the payload conducts thorough system reconnaissance, collecting detailed operating system, process, and runtime information for environment profiling.
Pulsar RAT implements modular data exfiltration targeting remote administration tools including AnyDesk, TeamViewer, and PuTTY, FTP clients such as FileZilla and WinSCP, VPN software including NordVPN and ExpressVPN, messaging platforms like Discord and Telegram, gaming platforms including Steam and Epic Games, and developer tools such as GitHub and JetBrains.
After executing the XOR script, the decoded.bin file is written. We then determine what file type it is.
The stealer component harvests browser credentials, cookies, autofill data, credit cards, and authentication tokens across multiple profiles.
Command Infrastructure
The malware features real-time surveillance capabilities including clipboard monitoring for cryptocurrency wallet addresses, webcam activation with frame capture, and continuous audio recording using Windows Core Audio APIs.
The malware exfiltrates these archives through Discord webhooks and Telegram Bot API endpoints, sending multipart POST requests with victim metadata including username, machine name, OS version, and malware version.
System control features allow remote attackers to turn on or off Task Manager and User Account Control, significantly reducing user visibility and resistance.
Stolen data is aggregated into ZIP archives containing a detailed summary file labeled “InteliX by dead artis” associated with the threat actor @aesxor.
Indicators of compromise
| MD5 Hash | Filename | Description |
|---|---|---|
| 648c0ba2bb1cde47fa8812f254821a72 | 0a1a98b5f9fc7c62.bat | Batch script file |
| 69392e0d2b877cb932ab709ebe758975 | ps_7b948266.ps1 | PowerShell script |
| 666493877fb7328c3e8c313fbcfdfd1e | Client.exe | Executable client component |
| 0020b06dc2018cc2b5bf98945a39cbd3 | Pulsar.Common.dll | Associated DLL module |
| 3abcad7678dd78832a164349aceeaa59 | Stealerv37.dll | Potential stealer module |
| — | 185[.]132[.]53[.]17:7800 | Command & Control (C2) Domain |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




