A threat actor has been targeting government entities with PureCrypter malware downloader that has been seen delivering multiple information stealers and ransomware strains.
Researchers at Menlo Security discovered that the threat actor used Discord to host the initial payload and compromised a non-profit organization to store additional hosts used in the campaign.
“The campaign was found to have delivered several types of malware including Redline Stealer, AgentTesla, Eternity, Blackmoon and Philadelphia Ransomware,” the researchers say.
According to the researchers, the observed PureCrypter campaign targeted multiple government organization in the Asia-Pacific (APAC) and North America regions.
Attack chain
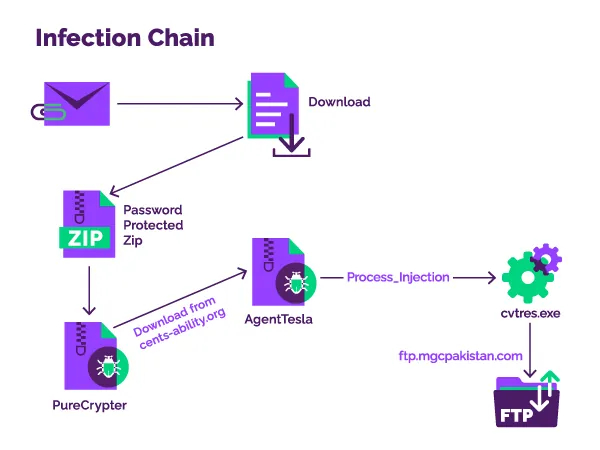
The attack begins with an email that has a Discord app URL pointing to a PureCrypter sample in a password-protected ZIP archive.
PureCrypter is a .NET-based malware downloader first seen in the wild in March 2021. Its operator rents it to other cybercriminals to distribute various types of malware.
When executed, it delivers the next-stage payload from a command and control server, which is the compromised server of a non-profit organization in this case.
The sample that the researchers at Menlo Security analyzed was AgentTesla. When launched, it establishes a connection to a Pakistan-based FTP server that is used to receive the stolen data.
The researchers found that the threat actors used leaked credentials to take control of the particular FTP server rather than setting it up their own, to reduce identification risks and minimize their trace.
AgentTesla still in use
AgentTesla is a .NET malware family that has been used by cybercriminals for the last eight years. Its usage peaking in late 2020 and early 2021.
A recent report by Cofense highlights that despite its age, AgentTesla remains a cost-effective and highly-capable backdoor that has received continual development and improvement over the years.
AgentTesla’s keylogging activity accounted for roughly one-third of all keylogger reports Cofense Intelligence recorded in 2022.
The malware’s capabilities include the following:
- Log the victim’s keystrokes to capture sensitive information such as passwords.
- Steal passwords saved in web browsers, email clients, or FTP clients.
- Capture screenshots of the desktop that could reveal confidential information.
- Intercept data that is copied to the clipboard, including texts, passwords, and credit card details.
- Exfiltrate stolen data to the C2 via FTP or SMTP.
In the attacks examined by Menlo Labs, it was discovered that the threat actors used process hollowing to inject the AgentTesla payload into a legitimate process (“cvtres.exe”) to evade detection from antivirus tools.
Furthermore, AgentTesla uses XOR encryption to protect its communications with the C2 server, like its configuration files, from network traffic monitoring tools.
Menlo Security believes that the threat actor behind the PureCrypter campaign is not a major one but it is worth monitoring its activity due to targeting government entities.
It is likely that the attacker will keep using compromised infrastructure for as long as possible before being forced to find new one.
