PureVPN’s Linux clients leak users’ IPv6 addresses when Wi-Fi reconnections or system resumes occur, and also obliterate host firewall rules without restoring them upon disconnect.
This undermines privacy guarantees and leaves systems more exposed than before VPN use, with critical failures in the kill-switch and firewall handling modules.
PureVPN Linux Client Flaws
Anagogistis stated that during testing on Ubuntu 24.04.3 LTS with kernel 6.8.0 and iptables-nft backend, both PureVPN GUI (v2.10.0) and CLI (v2.0.1) clients demonstrated an inability to reapply IPv6 kill-switch protections after toggling Wi-Fi or resuming from suspend.
With the IKS (IPv6 kill-switch) feature enabled, the CLI client automatically reconnects and reports the status as “connected.” However, the system regains a default IPv6 route via Router Advertisements (fe80::1) before the client can reinstate ip6tables rules.
Because ip6tables OUTPUT retains its default ACCEPT policy, IPv6 traffic resumes off-tunnel. In GUI mode, the client’s disconnect dialog correctly blocks IPv4 but neglects IPv6, allowing leaks until the user manually clicks Reconnect.
In real-world scenarios, this meant that IPv6-preferred websites loaded with the ISP-assigned address and email clients like Thunderbird continued sending SMTP traffic outside the VPN tunnel, despite the interface indicating full protection.
A second critical flaw is the client’s handling of host firewall rules. At VPN connection, PureVPN wipes existing iptables configurations: the default chain policies are reset to ACCEPT, and all custom and UFW chains, such as Docker jumps or user-defined rules, are flushed, Anagogistis said.
Upon disconnect, these changes are not reverted, leaving the INPUT and OUTPUT chains set to ACCEPT. The sequence is demonstrated below:
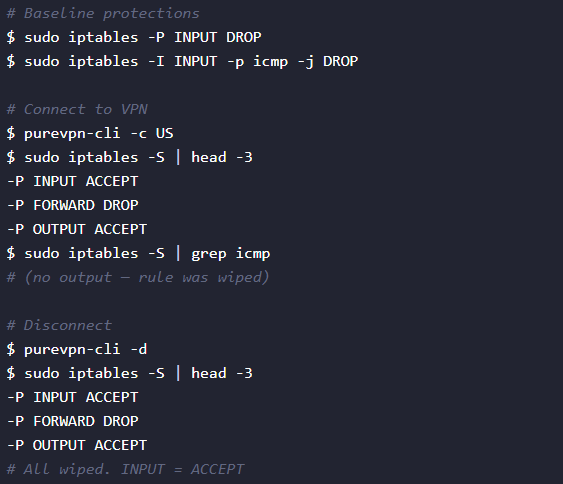
After disconnect, no custom rules remain, and SSH, ping, and other traffic are no longer filtered.
This behavior contradicts user expectations and defeats local deny-by-default strategies, effectively exposing services and enabling unwanted inbound connections.
Both issues have practical consequences for privacy-conscious Linux users relying on PureVPN for secure connectivity.
Until PureVPN addresses these flaws, users should exercise caution, consider disabling IPv6 at the OS level, and manually manage firewall rules or switch to clients with verified kill-switch reliability.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
