The list of Cl0p ransomware victims, which already includes Shell, Sony, PWC, EY, Boston Globe, Norton LifeLock, and even the US Energy Department, continues to grow as the ransomware group claimed the GUS Canada data breach.
“Cl0p has listed #GUS Canada, which operates a number of schools, including Toronto School of Management and Canadian College of Technology and Business,” read a tweet by threat analyst Brett Callow.
Global University Systems Canada is the Canadian arm of Global University Systems (GUS), a private limited company registered in the Netherlands that operates an international network of higher education institutions.
Meanwhile, more and more Cl0p ransomware victims have started conceding that they were indeed hit by cyber attacks, most of them disclosing that MOVEit file transfer vulnerabilities were used in the attacks
However, no major company mentioned by Cl0p on Thursday—PWC, EY, Sony, and Andesa Services—have confirmed their involvement in the MOVEit attacks.
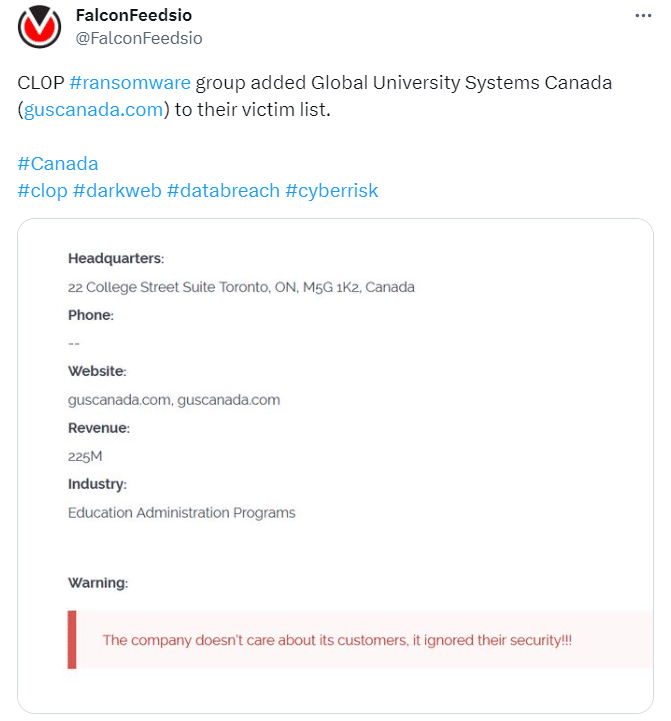
GUS Canada data breach, and the growing list of Cl0p ransomware victims
Global University Systems B.V. is a Dutch private limited company, with an extensive presence in the for-profit education sector. It possesses and manages numerous private colleges and universities in the UK, Canada, Israel, and Europe.
In addition, GUS oversees various brands and companies within the education industry, including InterActive, an e-learning provider.
As of 2018, GUS was recruiting students for its universities and colleges from more than 175 countries through a network of approximately 1,100 independent education agents and 500 staff in its own marketing, sales and business development departments.
According to Moody’s Investors Service, the company was deriving approximately 27% of its revenues in 2018 “from leveraging its agent network and marketing capabilities predominantly to source students for third-party institutions.”
Global University Systems Canada is the latest in the list of Cl0p ransomware victims, which fell for the ongoing global hacking campaign that tapped the MOVEit vulnerabilities.
Cl0p ransomware victims and MOVEit vulnerabilities
Among the targeted organizations are multinational media conglomerate Sony, as well as two prominent accounting firms, PricewaterhouseCoopers (PWC) and Ernst & Young (EY).
Additionally, Pennsylvania-based policy lifecycle management provider Andesa Services was also added to the list of victims.
PWC and Ernst & Young are globally recognized as part of the prestigious “Big Four” accounting firms, responsible for auditing over 80% of all US companies, according to industry experts.
PWC, ranked as the second-largest accounting firm worldwide, reportedly had more than 121GB of information, including company archives, stolen by Cl0p. On the other hand, Ernst & Young allegedly suffered a theft of 3GB of data and archives.
Cl0p had previously threatened to expose the names of its victims and their stolen data if they failed to meet the ransom demands by June 14.
The gang claims to have exploited a zero-day bug in the MOVEit system, utilizing SQL database injection to gain unauthorized access to sensitive information.
While specific details regarding the stolen data from Sony and Andesa Services have not been disclosed by Cl0p, their inclusion in the attack further highlights the broad reach of this hacking spree.
Previous victims of the MOVEit campaign include renowned names such as the BBC, the Boston Globe, Norton LifeLock, and even US federal agencies like the US Energy Department.
Cl0p ransomware and MFT vulnerabilities
Cl0p, known for its utilization of double-extortion tactics, had previously targeted Shell Global, an oil and gas giant, in a separate attack in March.
During that incident, the gang exploited a vulnerability in the Fortra GoAnywhere file management system. The current MOVEit attack, with the potential of impacting hundreds of victims, could surpass the consequences of the earlier breach.
Additionally, in December 2020, Clop targeted over 100 companies by exploiting zero-day vulnerabilities in Accellion’s outdated file-transfer application software, resulting in data theft.
Interestingly, in all three instances, Clop did not deploy its signature ransomware. Instead, they employed data extortion tactics as their chosen method of attack.
The Cl0p ransomware syndicate, which has been active since 2019 and has connections to Russia, operates under various aliases, including TA505, Lace Tempest, Dungeon Spider, and FIN11.
Typically focusing on organizations with revenues exceeding $5 million, the gang employs double-extortion techniques, threatening to release stolen data if the ransom demands are not met.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
