Malware authors continue to adopt legitimate software protection tools to shield their malicious code from security researchers. A prime example is the “VVS Stealer,” a Python-based malware family actively targeting Discord users.
By leveraging Pyarmor, a tool designed to protect Python scripts, VVS Stealer employs complex obfuscation to evade static analysis and signature-based detection, making reverse engineering significantly more difficult.
Pyarmor is typically used by developers to secure intellectual property, but in this context, it serves to blind security tools.
Originally marketed on Telegram in April 2025, VVS Stealer is designed to exfiltrate sensitive data such as Discord tokens, browser credentials, and session cookies.
However, its most notable feature is not just its theft capabilities, but the advanced cryptographic layers it uses to hide them.
The Pyarmor Challenge
The VVS Stealer samples analyzed by Unit 42 were packaged using PyInstaller and protected by Pyarmor version 9.1.4.
The obfuscation relies on BCC mode (ByteCode-to-Compilation), which converts Python functions into C functions stored within a separate dynamic-link library (DLL).
This means the core logic is not visible in standard Python bytecode. Furthermore, the malware utilizes AES-128-CTR encryption to lock its bytecode and strings.
Decrypting the payload requires extracting specific keys and nonces hidden within the Pyarmor runtime DLL a process that defeats many automated analysis sandboxes.
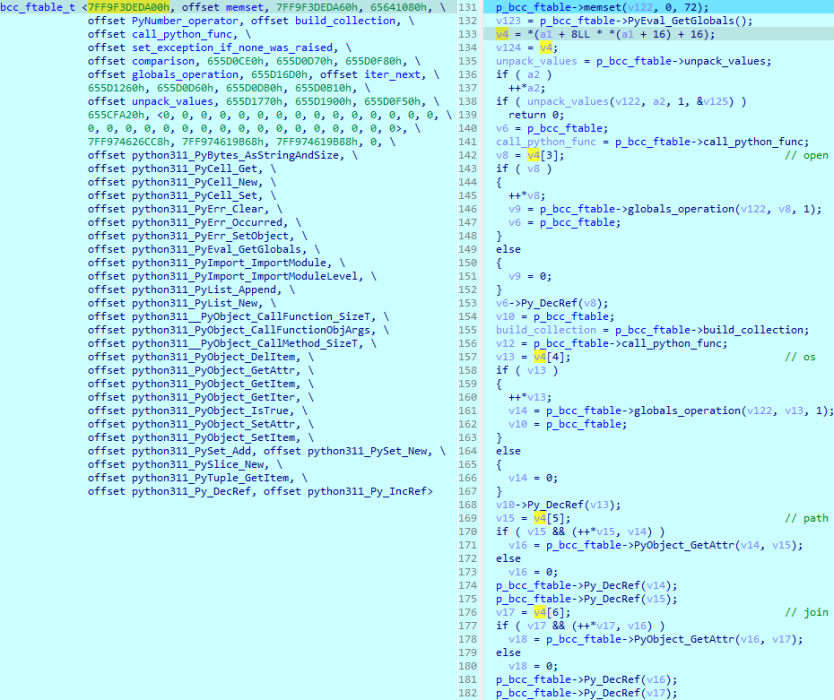
Researchers successfully deobfuscated the malware by restoring the Python bytecode header and using tools like Pycdc to recover the source code. This process revealed the malware’s true operational scope.
Capabilities and Persistence
Once stripped of its Pyarmor armor, the VVS Stealer reveals a suite of invasive features:
- Discord Injection: The malware kills running Discord processes and injects malicious JavaScript into the application’s core files. This allows it to intercept logins, password changes, and even bypass multi-factor authentication (MFA).
- Data Exfiltration: It targets a wide range of browsers including Chrome, Edge, and Opera to steal cookies, history, and autofill data. Stolen information is compressed into a ZIP archive and exfiltrated via Discord webhooks.
- Persistence: To ensure longevity, the malware copies itself to the Windows Startup folder. It also employs social engineering tactics, such as displaying a fake “Fatal Error” message box that instructs the victim to restart their computer, masking the infection process.
The VVS Stealer case highlights the dual-use nature of software protection tools. While Pyarmor provides legitimate security for developers, its adoption by threat actors necessitates more advanced deobfuscation workflows for defenders.
Palo Alto Networks customers are protected against VVS Stealer through Cortex XDR and XSIAM, which employ the Malware Prevention Engine to block such threats.
Additionally, Advanced WildFire and Advanced URL Filtering identify and block the malicious domains and payloads associated with this campaign.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




