The cybersecurity incident at the Netherlands-based geriatric healthcare service provider Attent Zorg Behandling turned out to be a ransomware attack, with the Qilin ransomware group claiming responsibility of it.
Attent Zorg en Behandeling is a non-profit organization that provides services in the field of housing, welfare and care to elderly people.
On February 18 Attent posted about a technical glitch on its communication channels it was suffering from February 17. The update disclosed having experienced unauthorized access on its network causing inaccessibility to its systems, emails, and telephones.
Attent Zorg en Behandeling and Qilin ransomware attack
The ransomware group claims to have access to ‘several hundred gigabytes’ data that belongs to the healthcare facility. The group warns that they will continue to download more data and post about the details on how they did it using an unpatched vulnerability in the network of Attent Zorg Behandling.
According to the Quilin ransomware group post, the vulnerability is yet to be patched. The post about the Attent Zorg Behandling data leak was made on March 1.
Image courtesy: Qilin leak site, via FalconFeedsio
Qilin ransomware group claims that that the geriatric facility tried to deceive its customers by saying that the services remained uninterrupted, despite the cybersecurity incident and the resultant data breach. In a series of news updates, the healthcare noted that there were technical malfunctions posing a delay in connecting to its locations through online communication channels.
The Attent Zorg Behandling news release also clarified that the cyber incident has not affected the care provided by it. The last update so far was made on February 28 that read the email communications were back to normal. While the telephone lines were restored on the 20th. The healthcare staff was handling the client files in a safe manner while the legal bodies continue their investigations.
Qilin ransomware group
Qilin follows a ransomware-as-a-service model that has mainly been targeting manufacturing and IT industries from several countries. The group has been in the news for developing ransomware in Rust besides Golang.
Rust has been known for its extended benefits like lower detection ratio as compared those made in other language. Moreover, ransomware written in Rust is more difficult to analyze. Qilin has been linked to the Agenda ransomware group that was found to be using Rust-based ransomware strain in the wild.
Agenda ransomware is used for partial encryption by configuring the percentage of file content to be encrypted. This technique helps in encrypting faster and also avoids detection, researchers from Trend Micro said in a report.
Several other gangs like Hive, RansomExx, and BlackCat have been found to have developed versions of their ransomware in the cross-platform language of Rust. It works across operating systems like Linux and Windows.
European healthcare and ransomware attacks
European healthcare providers have been facing a serious threat from ransomware attacks for many years, noted cybersecurity company Morphisec. COVID-19 has worsened the situation.
While inherent vulnerabilities within healthcare networks are no surprise, recent events put them into focus. Aside from highlighting insufficient frontline staffing and bed provision, pandemic-led digitization has also shed light on archaic and ineffective cybersecurity procedures still used within the healthcare sector,” said the report.
Morphisec’s report also warns that healthcare providers in Europe are likely to face even more ransomware attacks in the future, as threat actors become more sophisticated and target their attacks on vulnerable organizations.
The State of Ransomware in Healthcare 2022 report by Sophos, shows that the healthcare sector is experiencing an alarming increase in ransomware attacks, with 66% of healthcare organizations surveyed being targeted in 2021, up from 34% in 2020.
Furthermore, the healthcare sector is facing a more challenging threat environment, with a 69% increase in volume and a 67% increase in perceived complexity of cyber attacks, as well as a 59% increase in their impact.
The report also highlights the evolving relationship between ransomware and cyber insurance in healthcare, revealing that the industry is the most likely to pay the ransom, with 61% of organizations paying to get their encrypted data back. This is almost double the percentage of healthcare organizations that paid the ransom in 2020.

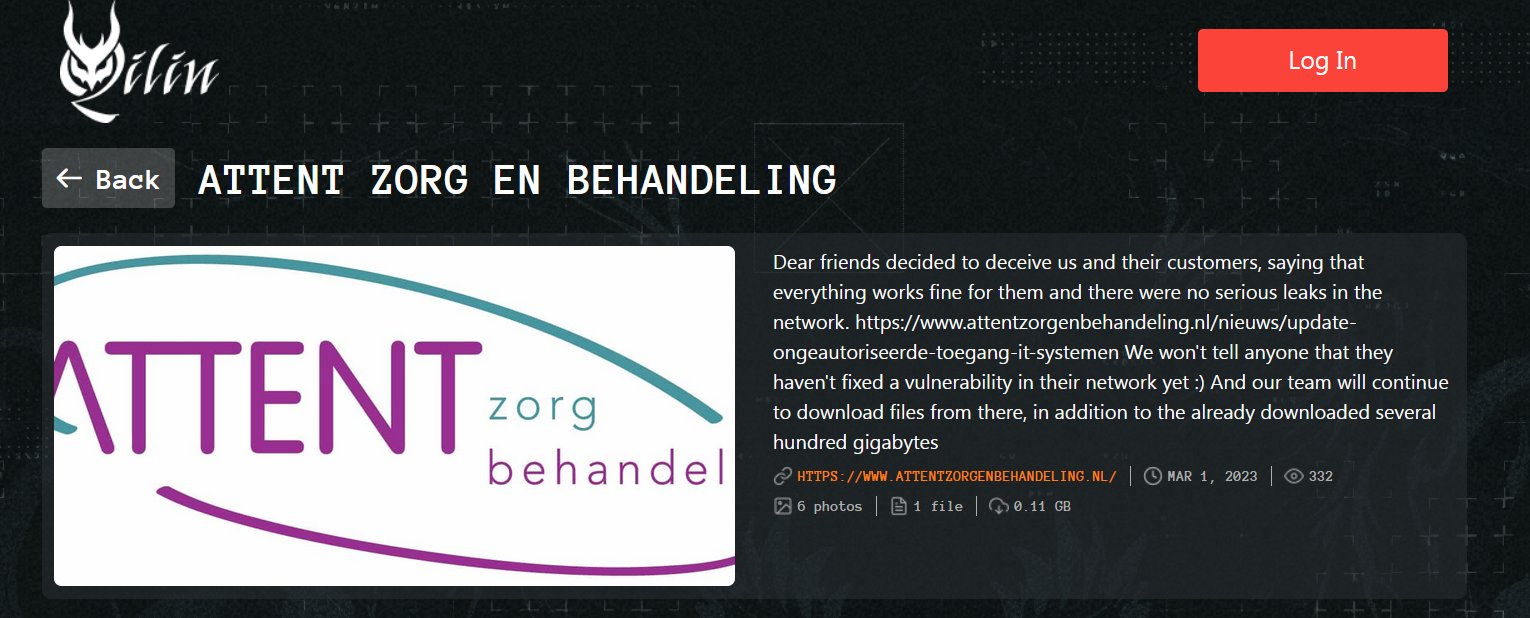 Image courtesy: Qilin leak site, via FalconFeedsio
Image courtesy: Qilin leak site, via FalconFeedsio