Qilin ransomware–an increasingly prolific ransomware-as-a-service (RaaS) operation–has intensified its global extortion campaigns by exploiting a covert network of bulletproof hosting (BPH) providers.
These rogue hosting services, often headquartered in secrecy-friendly jurisdictions and operated through labyrinthine shell-company structures, allow Qilin’s operators and affiliates to host malware, data leak sites, and command-and-control infrastructure with near impunity.
In late September, Qilin claimed responsibility for an attack that crippled Japanese brewing giant Asahi Group Holdings for nearly two weeks, underscoring the real-world impact of this clandestine hosting framework.
Since emerging in mid-2022 under the name “Agenda,” Qilin has evolved into a sophisticated RaaS platform offering affiliates a user-friendly web panel to configure attacks, manage victims, and negotiate ransoms.
The gang’s core developers maintain the ransomware codebase—written in Golang and Rust—and supply spear-phishing toolkits, remote monitoring and management (RMM) exploits, and double-extortion capabilities to an international affiliate network.
Affiliates keep the majority share of ransom payments, typically 80–85 percent, while the operators retain a 15–20 percent cut.
Central to Qilin’s resilience is its reliance on bulletproof hosting providers that promise zero know-your-customer checks, no abuse remediation, and resistance to law enforcement takedowns.
In April 2024, Qilin’s Tor-hosted data leak site referenced IP addresses tied to Cat Technologies Co. Limited in Hong Kong and to Red Bytes LLC in Saint Petersburg—companies embedded within a BPH conglomerate run by director Lenar Davletshin.
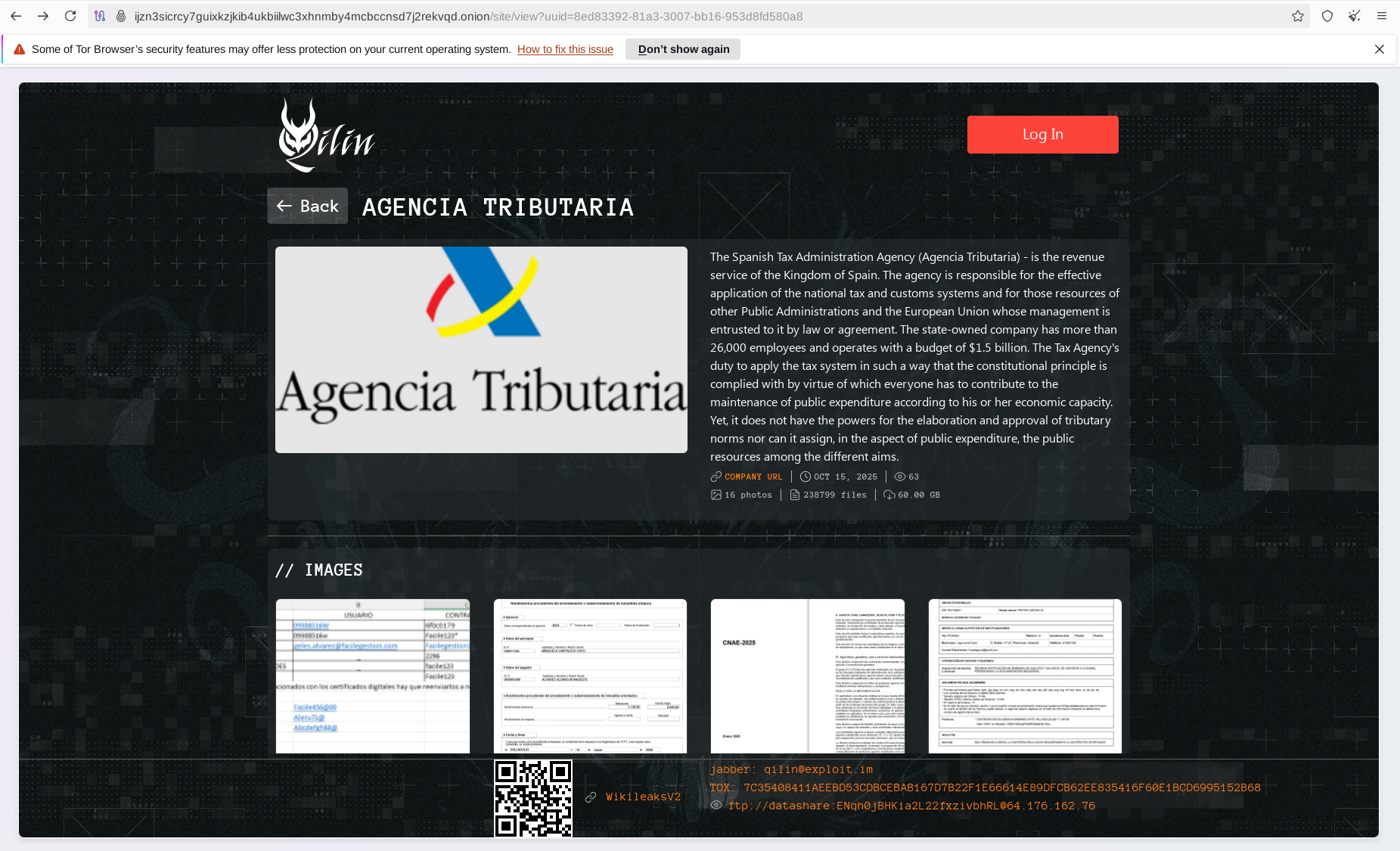
This agency employs more than 26,000 staff and operates with a budget of $1.5 billion, processing vast amounts of data from both private and public sectors.
Other hosting brands such as BearHost (now rebranded to voodoo_servers), Chang Way Technologies, and IPX-FZCO have been linked to Qilin’s infrastructure, often sharing addresses, administrators, or automated scanning servers designed for malicious reconnaissance.
These BPH operators leverage global regulatory arbitrage, establishing shell entities in Cyprus, Russia, and Hong Kong to evade transparency and abuse reporting.
Asahi Group Highlights Disruption
On September 29, 2025, Qilin unleashed its ransomware on Asahi Group Holdings, Japan’s largest beverage manufacturer.
According to our assessment, the root cause of the compromise could be insecure remote access and business email compromise (BEC) involving staff, based on historical indicators of malicious infections.


The attack paralyzed digital order processing, production scheduling, and shipping across 30 factories, forcing Asahi to revert to manual, paper-based order fulfillment.
Major retailers and restaurants reported nationwide shortages of Asahi products, and the company postponed the launch of 12 new items.
Asahi confirmed data exfiltration of some 27 GB and faced an 83 percent drop in domestic operating profit if the outage persisted. In mid-October, Qilin demanded $10 million USD for the stolen data, bypassing middlemen to accelerate pressure on its victim.
This incident bears resemblance to the Trinity of Chaos attack on Jaguar Land Rover, which halted global vehicle assembly lines and cost an estimated £72 million per day in lost sales.
Qilin’s targeting of high-value manufacturing and critical infrastructure underscores the gang’s strategic focus on industries where disruption inflicts maximal operational and financial damage.
Global Expansion and Future Threats
Throughout October 2025, Qilin announced new victims across Europe, North America, Africa, and Asia.
The symbiotic relationship between Qilin and BPH operators, now unified under an underground conglomerate spanning Russian-speaking and Hong Kong jurisdictions, presents a formidable challenge to cybersecurity defenders.

Recent disclosures include Spain’s Tax Administration Agency, several U.S. municipalities and healthcare providers, French municipal bodies, and African insurance technology firms.
The group appears to diversify its targets, striking a balance between large public-sector organizations and private enterprises in critical supply chains.
Past recruitment of North Korean actors highlights Qilin’s willingness to integrate foreign affiliates, suggesting evolving collaboration with state-sponsored or independent access brokers.
Disrupting these hosting ecosystems will require coordinated international law enforcement and regulatory pressure on the shell companies that underpin BPH services.
Until then, Qilin is poised to leverage these ghost hosting platforms for further high-impact ransomware campaigns.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




