The Ransomed VC hacker group has added Linktera to their dark web portal. They have claimed to have successfully executed the Linktera data breach and gained unauthorized access to their database.
The threat actor domain is suspended, leaving Ransomed VC to operate with impunity through their dark web channels.
The Linktera data breach, according to the threat actor, involved gaining access and executing a calculated move to delete all backups from the servers. Their demand for a ransom of $23,000 hangs ominously over the situation.
Linktera data breach and $23,000 ransom
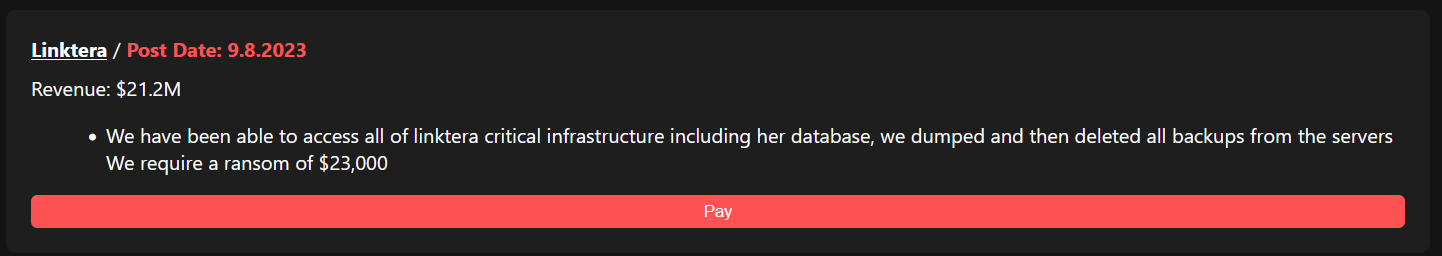
Accompanying this Linktera data breach announcement is a conspicuous “Pay” button that redirects users to a dedicated page, where the victim is expected to remit the ransom to regain control over their information and access.

Furthermore, the Ransomed VC hacker group has made the same ransom demand of $23,000 public, reiterating their demand in exchange for restoring access to Linktera’s systems.
Additionally, their message on their dark web channel reveals a staggering revenue figure of $21.2 million for Linktera.
Despite the hacker group’s claims of a successful breach, visiting Linktera’s website shows no discernible signs of a data breach or any cyber attack. However, there could be a compromise at the website’s backend or databases.
The Cyber Express, to learn more about this Linktera data breach, reached out to the organization for an official statement. Regrettably, as of the time of writing, no response had been received, leaving the claims of the Linktera data breach hanging to stand unconfirmed.
Who is the Ransomed VC hacker group?
The Ransomed VC hacker group, while making bold claims against prominent companies, remains shrouded in mystery. Their origins and motivations remain largely unknown, with little information available beyond their activities in hacking forums.
According to Ron Kaminsky, an Incident Response Analyst, “Ransomed VC” represents a unique and newly identified extortion group that employs an unconventional tactic involving European GDPR laws.
Their modus operandi involves gaining access to websites and subsequently leveraging the specter of GDPR fines to intimidate and extort companies.
Under GDPR, the potential fines for violations are substantial. Minor infractions can result in penalties of up to $10,000,000 or 2% of a company’s annual revenue from the preceding year.
Meanwhile, serious violations can lead to fines of up to $20,000,000 or 4% of the annual revenue.
This novel approach to cyber extortion exploits laws initially designed to safeguard individuals’ privacy and data rights, signaling a concerning development among cybercriminals and hackers.
By leveraging GDPR, the Ransomed VC group is willing to exploit legal frameworks for their financial gain, departing from the traditional data encryption model and ransom demands.
In the face of such audacity and sophistication, the cybersecurity community is left with a pressing challenge: to adapt and fortify defenses against this new breed of cyber threat.
The Linktera data breach is an ongoing story, and we will update this story once we have more information or official confirmation from the company.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.