Ransomware and supply chain attacks set records in 2025, with ransomware attacks up more than 50% and supply chain attacks nearly doubling – trends that suggest further trouble ahead in 2026.
Those are some of the data points from a new blog and annual threat landscape report from threat intelligence company Cyble.
There were 6,604 ransomware attacks in 2025, 52% higher than the 4,346 attacks claimed by ransomware groups in 2024, according to Cyble data. And the year ended on an upswing for threat groups, with a near-record 731 ransomware attacks in December, behind only February 2025’s record totals (chart below).
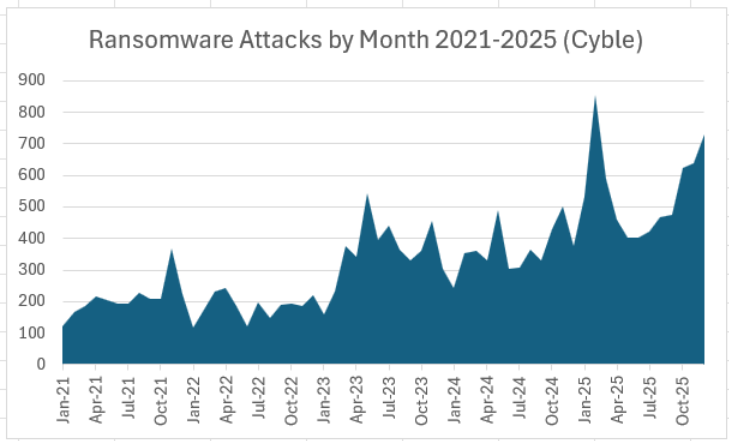

Ransomware groups remained resilient and decentralized in 2025, and ransomware affiliates were quick to gravitate toward new leaders like Qilin in the wake of law enforcement disruptions.
Supply Chain Attacks Soared in 2025
Supply chain attacks soared by 93% in 2025, according to Cyble dark web researchers, as supply chain attacks claimed by threat groups surged from 154 incidents in 2024 to 297 in 2025 (chart below).
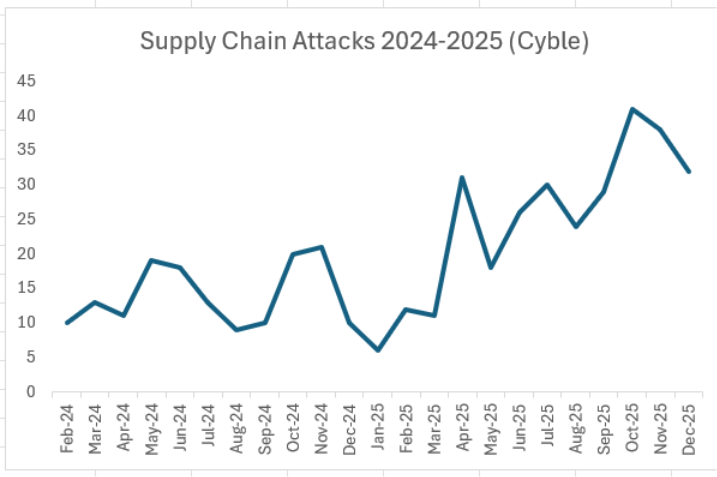

“As ransomware groups are consistently behind more than half of supply chain attacks, the two attack types have become increasingly linked,” Cyble noted.


Supply chain attacks have declined since setting a record in October, but Cyble noted that “they remain above even the elevated trend that began in April 2025.”
Every industry and sector tracked by Cyble was hit by a software supply chain attack in 2025, but the IT and Technology sectors were by far the most frequently hit because of the potential for expanding attacks into downstream customer environments.
The sophistication of those attacks also grew.
Supply chain attacks in 2025 “expanded far beyond traditional package poisoning, targeting cloud integrations, SaaS trust relationships, and vendor distribution pipelines,” Cyble said. “Adversaries are increasingly abusing upstream services—such as identity providers, package registries, and software delivery channels—to compromise downstream environments on a large scale.”
Attacks on Salesforce through third-party integrations is one such example, as attackers “weaponized trust between SaaS platforms, illustrating how OAuth-based integrations can become high-impact supply chain vulnerabilities when third-party tokens have been compromised.”
Qilin Dominated Following RansomHub’s Decline
Qilin emerged as the leading ransomware group in April after RansomHub was hit by a possible act of sabotage by rival Dragonforce. Qilin claimed another 190 victims in December, besting a resurgent Lockbit and other leaders such as newcomer Sinobi.
Qilin claimed 17% of all ransomware victims in 2025, well ahead of Akira, CL0P, Play and SafePay (chart below). Cyble noted that of the top five ransomware groups in 2025, only Akira and Play also made the list in 2024, as RansomHub and Lockbit declined and Hunters apparently rebranded as World Leaks.
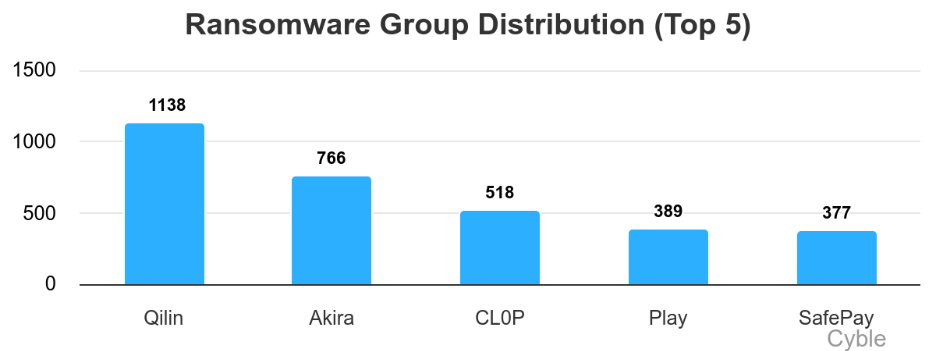

Cyble documented 57 new ransomware groups, 27 new extortion groups and more than 350 new ransomware strains in 2025. Those new strains were “largely based on the MedusaLocker, Chaos, and Makop ransomware families,” Cyble said.
Among new groups, Devman, Sinobi, Warlock and Gunra have targeted critical infrastructure, particularly in Government & Law Enforcement and Energy & Utilities, at an above-average rate. RALord/Nova, Warlock, Sinobi, The Gentlemen and BlackNevas have focused on the IT, Technology, and Transportation & Logistics sectors.
The U.S. was by far the most attacked country, suffering 55% of all ransomware attacks in 2025. Canada, Germany, the UK, Italy and France rounded out the top six (chart below).


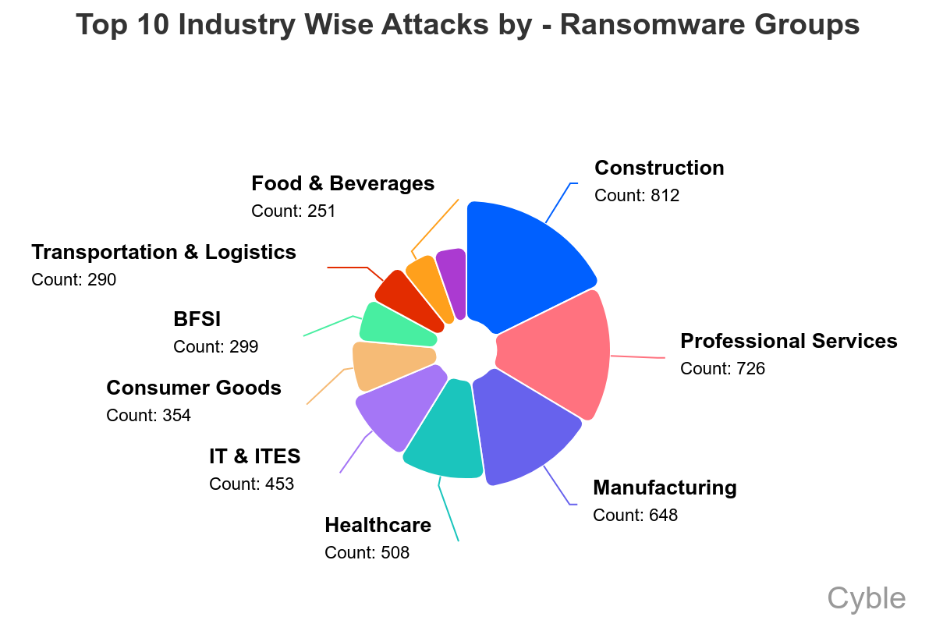
Construction, professional services and manufacturing were the industries most targeted by ransomware groups, followed by healthcare and IT (chart below).

“The significant supply chain and ransomware threats facing security teams as we enter 2026 require a renewed focus on cybersecurity best practices that can help protect against a wide range of cyber threats,” Cyble concluded, listing best practices such as segmentation and strong access control and vulnerability management.
