Ransomware attacks soared 30% in October to the second-highest total on record, Cyble reported today.
The 623 ransomware attacks recorded in October were second only to February 2025’s record attacks, when a CL0P MFT campaign drove the total number of ransomware attacks to 854. October was the sixth consecutive monthly increase in ransomware attacks, Cyble noted in a blog post.
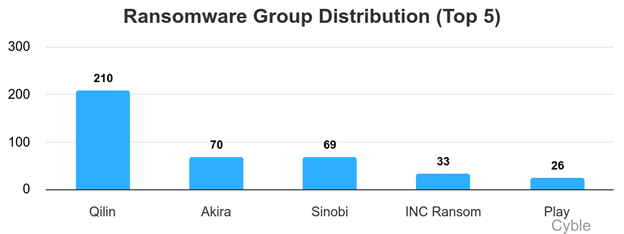
Qilin once again was the most active ransomware group, for the sixth time in the seven months since the decline of RansomHub. Qilin’s 210 claimed victims were three times greater than second-place Akira (chart below). Just behind Akira was Sinobi with 69 victims, a remarkable rise for a group that first emerged in July.
Construction, Professional Services, Healthcare, Manufacturing, IT and Energy/Utilities were the most targeted sectors (chart below).


Cyble noted that 31 incidents in October may have affected critical infrastructure, and another 26 incidents had possible supply chain implications.
The U.S. once again was the most attacked country, its 361 attacks 10 times greater than second-place Canada (chart below).
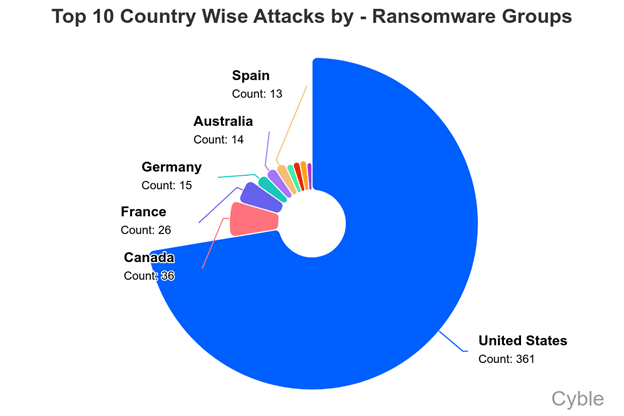

“Of concern is the emergence of Australia as a top five target, as the country’s rich resources and high per-capita GDP have made the country a rich target for threat actors,” Cyble noted.
Ransomware attacks are up 50% so far this year, with 5,194 ransomware attacks through October 31, Cyble said, “as new leaders like Qilin, Sinobi and The Gentlemen have more than made up for the decline of former leaders such as LockBit and RansomHub.”
Vulnerabilities Exploited by Ransomware Groups
Critical IT vulnerabilities and unpatched internet-facing assets have fueled a rise in both ransomware and supply chain attacks this year, Cyble said. Vulnerabilities targeted in October included:
- CVE-2025-61882 in Oracle E-Business Suite – targeted by Cl0p
- CVE-2025-10035 in GoAnywhere MFT – exploited by Medusa
- CVE-2021-43226 a Microsoft Windows Privilege Escalation vulnerability – Exploited by unknown ransomware groups, according to a CISA advisory
- CVE-2025-6264 in Velociraptor – targeted by Warlock ransomware operators
- CVE‑2024‑1086 in the Linux kernel’s netfilter :nf_tables module – Exploited by unknown ransomware groups, according to a CISA advisory
Ransomware Attacks and Key Developments
Below were some of the most important ransomware developments in October, according to Cyble.
Ransomware operators are “increasingly hijacking or silently installing legitimate remote access tools” such as AnyDesk, RustDesk, Splashtop, and TightVNC after credential compromise to gain persistent access, control, antivirus neutralization and ransomware delivery.
Recent BlackSuit campaigns used Vishing to steal VPN credentials for initial access and DCSync on a domain controller for high-privilege access, and used AnyDesk and a custom RAT for persistence. “Other measures included wiping forensic traces with CCleaner, and using Ansible to deploy BlackSuit ransomware across ESXi hosts, encrypting hundreds of VMs and causing major operational disruption,” Cyble said.
Qilin affiliates deployed a Linux-based ransomware binary on Windows machines by abusing remote-management tools like WinSCP, Splashtop, AnyDesk, and ScreenConnect, and leveraging BYOVD (Bring Your Own Vulnerable Driver) attacks, among other tools and tactics.
Trigona ransomware operators brute-forced exposed MS-SQL servers and embedded malware inside database tables and exporting it to disk to install payloads.
DragonForce posted on the RAMP cybercrime forum that it is opening its partner program to the public, offering services like professional file analysis/audit, hash decryption, call support, and free victim storage. Registration requires a $500 non-refundable fee. Affiliates were warned to follow the group’s rules “or face account blocking or free decryptor distribution.”
Zeta88 — the alleged operator of The Gentlemen ransomware — announced updates to their Windows, Linux and ESXi lockers, including a silent mode for Windows that encrypts without renaming files and preserves timestamps, and self-spread capabilities across networks and domains. The release also introduced multiple encryption-speed modes, Windows operating modes, and a universal decryptor.
The full Cyble blog also included recommended best practices and recent high-confidence Qilin indicators of compromise (IoCs).



