Microsoft warned today that ransomware gangs are actively exploiting a VMware ESXi authentication bypass vulnerability in attacks.
Tracked as CVE-2024-37085, this medium-severity security flaw was discovered by Microsoft security researchers Edan Zwick, Danielle Kuznets Nohi, and Meitar Pinto and fixed with the release of ESXi 8.0 U3 on June 25.
The bug enables attackers to add a new user to an ‘ESX Admins’ group they create, a user that will automatically be assigned full administrative privileges on the ESXi hypervisor.
“A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management by re-creating the configured AD group (‘ESXi Admins’ by default) after it was deleted from AD,” Broadcom explains.
“Several ESXi advanced settings have default values that are not secure by default. The AD group “ESX Admins” is automatically given the VIM Admin role when an ESXi host is joined to an Active Directory domain.”
While a successful attack requires high privileges on the target device and user interaction, Microsoft says several ransomware gangs exploit it to escalate to full admin privileges on domain-joined hypervisors.
This allows them to steal sensitive data stored on the hosted VMs, move laterally through the victims’ networks, and encrypt the ESXi hypervisor’s file system.
Microsoft has identified at least three tactics that could be used to exploit the CVE-2024-37085 vulnerability, including:
- Adding the “ESX Admins” group to the domain and adding a user.
- Renaming any group in the domain to “ESX Admins” and adding a user to the group or using an existing group member.
- ESXi hypervisor privileges refresh (assigning other groups admin privileges will not remove them from the ‘ESX Admins’ group).
Exploited in Black Basta and Akira ransomware attacks
So far, the vulnerability has been exploited in the wild by ransomware operators tracked as Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest in attacks that have led to Akira and Black Basta ransomware deployments.
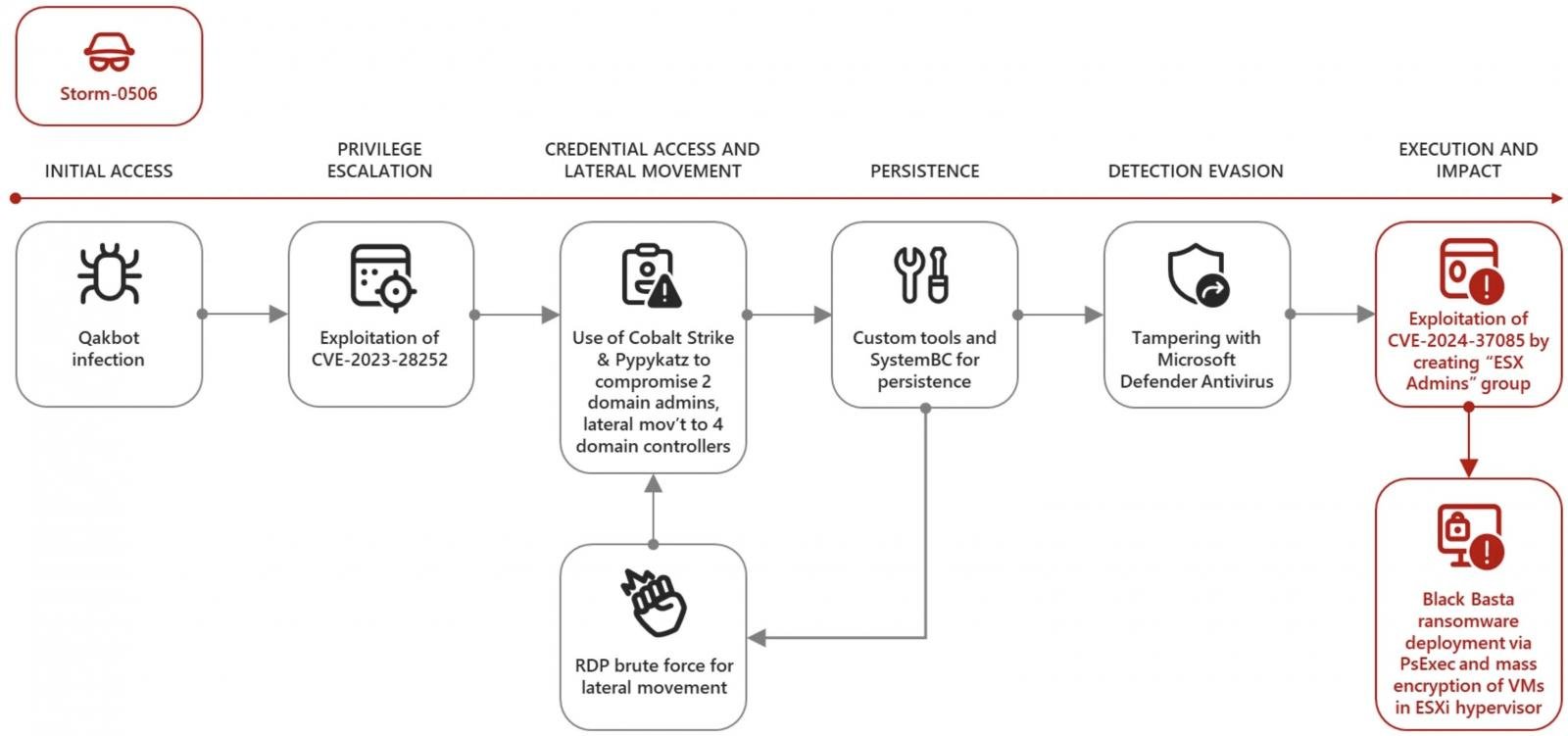
For instance, Storm-0506 deployed Black Basta ransomware on the ESXi hypervisors of a North American engineering firm after elevating privileges by exploiting the CVE-2024-37085 flaw.
“The threat actor gained initial access to the organization via Qakbot infection, followed by the exploitation of a Windows CLFS vulnerability (CVE-2023-28252) to elevate their privileges on affected devices,” Redmond says.
“The threat actor then used Cobalt Strike and Pypykatz (a Python version of Mimikatz) to steal the credentials of two domain administrators and to move laterally to four domain controllers.”
For years, there has been a growing trend of targeting an organization’s ESXi hypervisors. Ransomware groups have started focusing on ESXi virtual machines (VMs) after many enterprises began using them to host critical applications and store data due to their efficient resource handling.
This happens because taking down ESXi VMs can cause major outages and disrupt business operations while encrypting files and backups stored on the hypervisor, severely limiting victims’ options to recover their data.
However, ransomware groups have focused on creating lockers dedicated to encrypting ESXi VMs rather than targeting specific ESXi vulnerabilities (like CVE-2024-37085) that would provide them a quicker way of acquiring and maintaining access to a victim’s hypervisors.
The Play ransomware group is the latest such operation to start deploying an ESXi Linux locker in their attacks.
“The number of Microsoft Incident Response (Microsoft IR) engagements that involved the targeting and impacting ESXi hypervisors have more than doubled in the last three years,” Microsoft warned.




