Ransomware gangs are now targeting a recently patched critical vulnerability in JetBrains’ TeamCity continuous integration and deployment server.
The flaw (tracked as CVE-2023-42793 and tagged with a 9.8/10 severity score) allows unauthenticated attackers to gain remote code execution (RCE) after successfully exploiting an authentication bypass weakness in low-complexity attacks that don’t require user interaction.
Swiss security firm Sonar (whose researchers discovered and reported the vulnerability) published full technical details one week after JetBrains addressed the critical security issue with the release of TeamCity 2023.05.4 on September 21st.
“This enables attackers not only to steal source code but also stored service secrets and private keys,” Sonar vulnerability researcher Stefan Schiller explained.
“And it’s even worse: With access to the build process, attackers can inject malicious code, compromising the integrity of software releases and impacting all downstream users.”
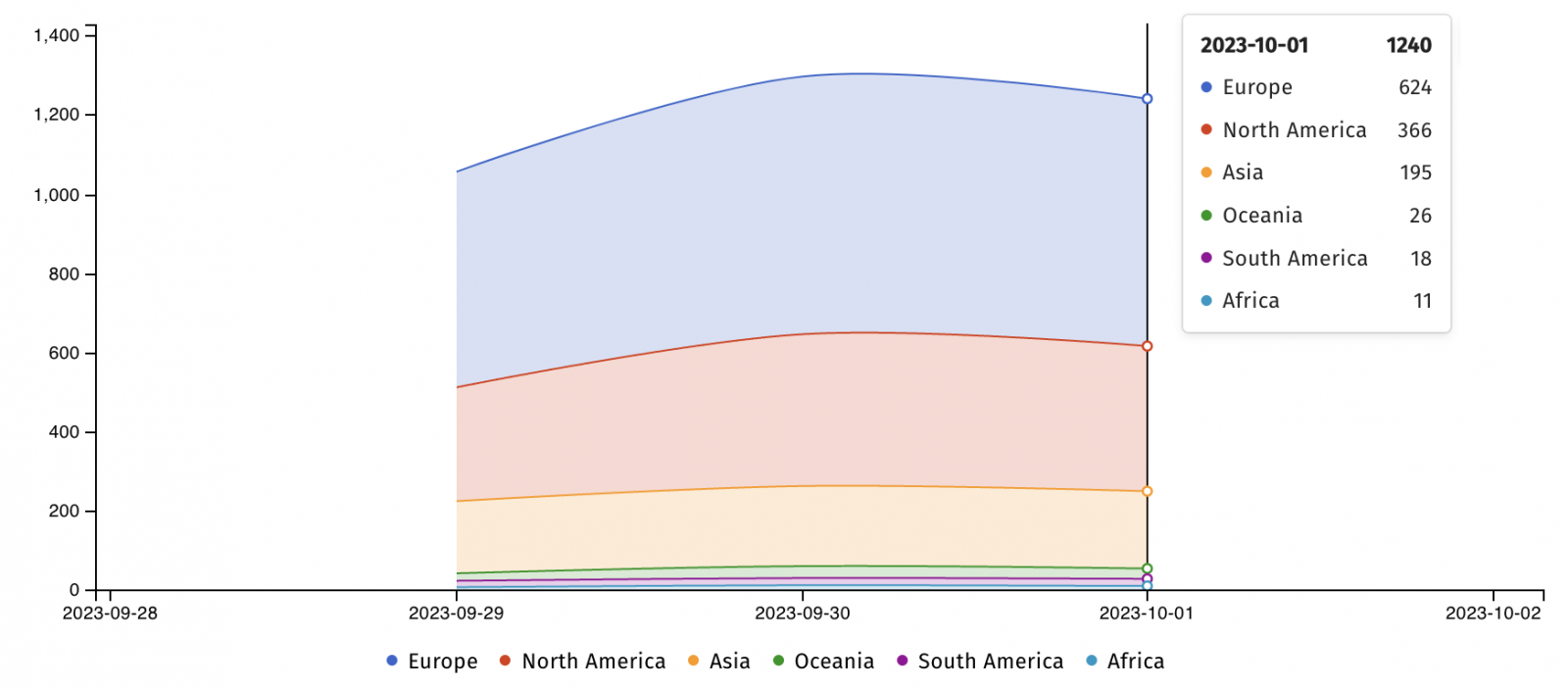
Security researchers at the nonprofit internet security organization Shadowserver Foundation found 1240 unpatched TeamCity servers vulnerable to attacks.
Targets set on vulnerable TeamCity servers
Just days after Sonar published their blog post, multiple attackers started exploiting this critical auth bypass flaw, according to threat intelligence companies GreyNoise and PRODAFT.
PRODAFT said that multiple ransomware operations have already added CVE-2023-42793 exploits to their arsenal and are using them to breach vulnerable TeamCity servers.
“Many popular ransomware groups started to weaponize CVE-2023-42793 and added the exploitation phase in their workflow,” PRODAFT warned over the weekend.
“Our BLINDSPOT platform has detected multiple organizations already exploited by threat actors over the last three days. Unfortunately, most of them will have a huge headache in the upcoming weeks.”
Attacks originating from at least 56 different IP addresses were seen by GreyNoise actively targeting Internet-exposed JetBrains TeamCity servers in concerted efforts to infiltrate unpatched installations.
Two days earlier, GreyNoise cautioned all organizations that failed to patch their servers before September 29th that there’s a high likelihood their systems have already been compromised.




