The Federal Bureau of Investigation (FBI) revealed in its 2022 Internet Crime Report that ransomware gangs breached the networks of at least 860 critical infrastructure organizations last year.
However, given that the FBI’s report only includes attacks reported to the Internet Crime Complaint Center (IC3), the actual number is likely higher.
“The IC3 received 870 complaints that indicated organizations belonging to a critical infrastructure sector were victims of a ransomware attack,” the FBI said.
“Of the 16 critical infrastructure sectors, IC3 reporting indicated 14 sectors had at least 1 member that fell victim to a ransomware attack in 2022.”
In total, ransomware victims filed 2,385 complaints throughout 2022, with adjusted losses of over $34.3 million.
While the FBI states that it received 870 complaints from affected critical infrastructure organizations, the graph that provides more detailed info for each sector totals only 860 hits.
The top three ransomware gangs linked to attacks targeting critical infrastructure last year, based on the number of attacks, were Lockbit (149), ALPHV/BlackCat (114), and Hive (87).
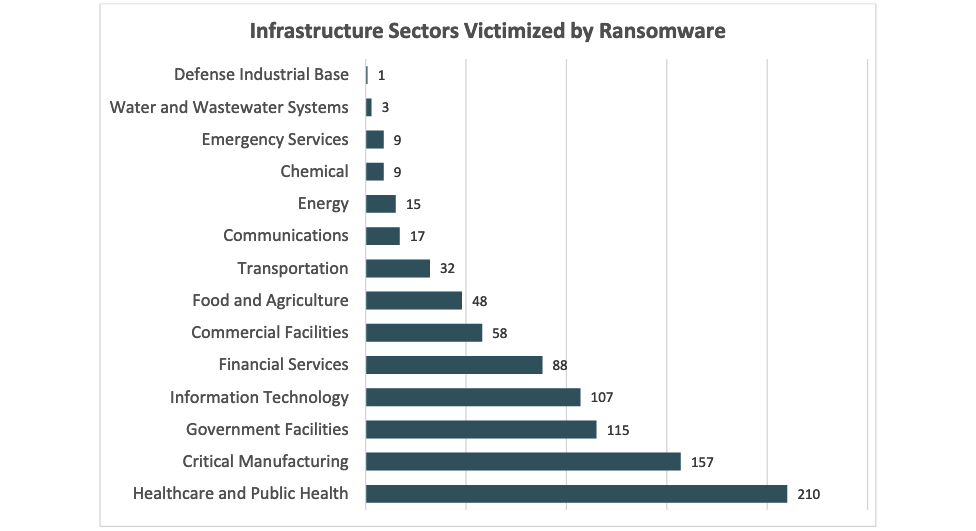
This year’s Internet Crime Report confirms the law enforcement agency last year’s prediction of an “increase in critical infrastructure victimization in 2022” when victims filed 649 complaints.
The FBI advises against paying ransoms to cybercriminals since payments don’t guarantee that victims will recover their files, may encourage further attacks, and will most likely be used to fund additional attacks.
Victims are urged to report ransomware incidents to the Internet Crime Complaint Center (IC3), which will provide crucial information to track their attackers and prevent future attacks.
FBI has issued multiple advisories, Private Industry Notifications (PINs), and flash alerts in recent years, warning of ransomware attacks against critical infrastructure, including Healthcare and First Responder networks, Water and Wastewater Systems, the Food and Agriculture sector, and education institutions.
It also revealed that Ragnar Locker ransomware breached at least 52 critical orgs, Cuba ransomware hit at least 49 U.S. critical infrastructure entities, and BlackByte ransomware was deployed on the networks of at least three others.
The FBI shared a list of immediate measures that can be taken to defend against ransomware attacks:
- Update your operating system and software.
- Implement user training and phishing exercises to raise awareness about the risks of suspicious links and attachments.
- If you use Remote Desktop Protocol (RDP), secure and monitor it.
- Make an offline backup of your data.
CISA also announced on Monday that it has been scanning critical infrastructure entities’ networks for ransomware-vulnerable devices since January 30, 2023, to warn and help them fix the flaws before they get hacked.
