An initial access broker tracked as Storm-0249 is abusing endpoint detection and response solutions and trusted Microsoft Windows utilities to load malware, establish communication, and persistence in preparation for ransomware attacks.
The threat actor has moved beyond mass phishing and adopted stealthier, more advanced methods that prove effective and difficult for defenders to counter, even if well documented.
In one attack analyzed by researchers at cybersecurity company ReliaQuest, Storm-0249 leveraged the SentinelOne EDR components to hide malicious activity. However, researchers say that the same method works with other EDR products, as well.
SentinelOne EDR abuse
ReliaQuest says that the Storm-0249 attack started with ClickFix social engineering that tricked users into pasting and executing curl commands in the Windows Run dialog to download a malicious MSI package with SYSTEM privileges.
A malicious PowerShell script is also fetched from a spoofed Microsoft domain, which is piped straight onto the system’s memory, never touching the disk and thus evading antivirus detection.
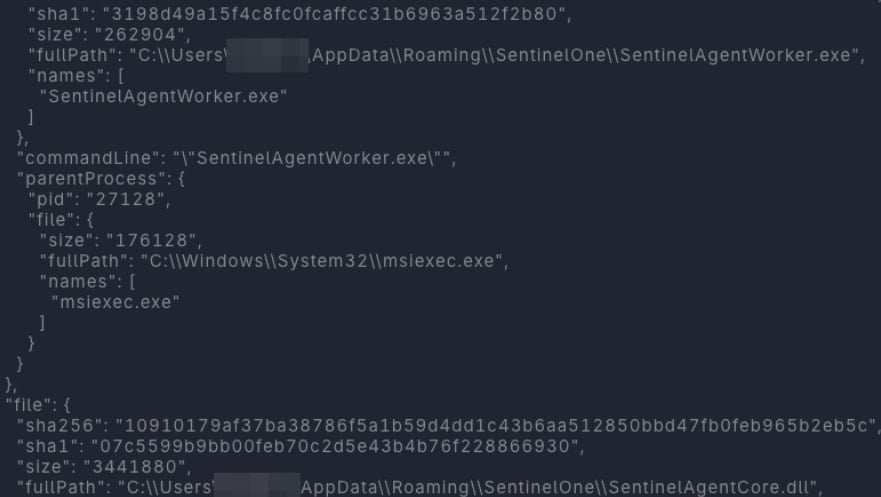
The MSI file drops a malicious DLL (SentinelAgentCore.dll). According to the researchers, “this DLL is placed strategically alongside the pre-existing, legitimate SentinelAgentWorker.exe, which is already installed as part of the victim’s SentinelOne EDR.”
Next, the attacker loads the DLL using the signed SentinelAgentWorker (DLL sideloading), executing the file within the trusted, privileged EDR process and obtaining stealthy persistence that survives operating system updates.
“The legitimate process does all the work, running the attacker’s code, appearing as routine SentinelOne activity to security tools and bypassing detection,” explains ReliaQuest.
Source: ReliaQuest
Once the attacker gains access, they use the SentinelOne component to collect system identifiers through legitimate Windows utilities like reg.exe and findstr.exe, and to funnel encrypted HTTPS command-and-control (C2) traffic.
Registry queries and string searches would normally raise alarms, but when conducted from within a trusted EDR process, they are treated as routine and ignored by security mechanisms.
ReliaQuest explains that the compromised systems are profiled using ‘MachineGuid,’ a unique hardware-based identifier that ransomware groups like LockBit and ALPHV use for binding encryption keys to specific victims.
This suggests that Storm-0249 conducts initial access compromises tailored to the needs of its typical customers, ransomware affiliates.
The abuse of trusted, signed EDR processes bypasses nearly all traditional monitoring. The researchers recommend that system administrators rely on behavior-based detection that identifies trusted processes loading unsigned DLLs from non-standard paths.
Furthermore, it is helpful to set stricter controls for curl, PowerShell, and LoLBin execution.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.





