January has registered a dip in public ransom notes, compared to the previous month as well as the same period last year. However, this does not mean an absolute fall in ransomware attacks, say researchers.
“Apparent inactivity by ransomware gangs is complicated by the fact that their Dark Web leak sites only show companies that didn’t pay a ransom, so an extremely successful month for them also looks like an inactive month,” said the monthly ransomware review by Malwarebytes Labs.
“A month where nobody refused to pay would be hugely unusual though,” it added.
Ransomware take down – Hive ransomware report
Malwarebytes published a ransomware report highlighting the number, victims, sectors, etc., of ransomware attacks in January 2023, and others discussing the changing landscape of ransomware. Based on activities seen on the dark web, and onion sites of attackers, it was inferred that the Hive ransomware group and BlackBasta were possibly out of the threat scenario.
LockBit continued to top the list of the most active ransomware groups with 51 cyberattacks followed by ALPHV with 23. In January 2023, the United States was targeted the most with nearly 71 cyberattacks followed by 17 in the United Kingdom, 9 in Australia, and 6 each in Canada and France.
Hive activities were thwarted by the team effort of the United States Department of Justice (DOJ) and the legal authorities of several other countries. The DOJ reported over 1,500 cyberattacks in more than 80 countries in hands of Hive so far.
Ransomware report on its falling revenue

(Photo: Chainanalysis)
While the revenue generated via ransomware attacks made headlines in 2020 when it shot up to $765 million. However, a decline was noted later when it dropped to $457 in 2022. Researchers are speculating that the denial of paying a ransom is one of the main reasons behind the ransomware revenue crash.
Other reasons could include increased awareness of ransomware, solidarity with the other victims in respective sectors, and the actions of regulatory and legal bodies around the punitive measures in the aftermath of ransomware attacks.
Attempts to be adaptable
LockBit, in its Russian language leak site, wrote that it is looking to ‘’expand the arsenal in the panel.’ The group had tried a Conti-based encryptor called LockBit Green which they used to attack nearly five entities. This was the third encryptor recorded by the group, with the others being LockBit Red and LockBit Black.
It is speculated that ransomware groups are trying to invite other affiliates using encryptors from other groups.
January 2023 sector-wise ransomware report

(Photo: Malwarebytes)
Among the reported and known ransomware attacks service related sectors suffered 53 attacks, education 21, retail 16, and manufacturing sector, 14. This was followed by the wholesale and technology sector which suffered about 12 major cyberattacks. Construction and healthcare suffered nearly 7 ransomware strains while food and beverages had nearly 6 attacks.
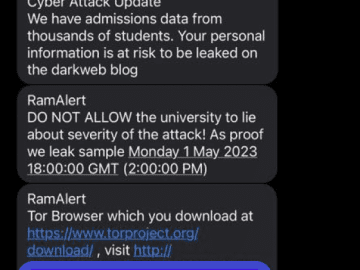
Vice ransomware group continued its attacks on the education sector. The Endurance gang, apparently run by a single threat actor, sprung up in the threat landscape last month. Autotrader was targeted by Endurance allegedly stealing the data of nearly 1.4 million users.
Ransomware criminals also have a modus operandi that dictates whether they will take a hiatus after launching a cyberattack or otherwise. It is up to legal authorities to catch them when and from where they are not expecting.