Following the February 21 attack on Change Healthcare, scores of people in the US have been living with the brutal, real-world effects of ransomware.
Described by the American Hospital Association (AHA) President and CEO Rick Pollack as “the most significant and consequential incident of its kind against the US health care system in history,” the attack has stopped billions of dollars in payments flowing between doctors, hospitals, pharmacies and insurers. It has also created skyrocketing pharmacy bills, pushed some healthcare providers to the edge of insolvency, and led some small practices offering chemotherapy to warn that they are just weeks from turning patients away.
There are thousands of “big game” ransomware attacks like this every year—large scale cyberattacks that can bring entire organisations to a halt. They are always damaging and they always cause pain, but when they hit the healthcare system, the consequences—particularly the risk to life—are often more immediately obvious and shocking.
From time to time individual ransomware gangs will grandstand and say they don’t or won’t hit hospitals, but the truth is that healthcare has always been a major target.
Only three weeks ago, the Cybersecurity and Infrastructure Security Agency (CISA) issued a warning that ALPHV, the ransomware group behind the attack on Change Healthcare, was singling out targets in that sector, saying that “since mid-December 2023, of the nearly 70 leaked victims, the healthcare sector has been the most commonly victimized.”
ALPHV is just one gang among many targeting the sector. In the last 12 months, known ransomware attacks on US targets have increased an enormous 101% year-on-year, but attacks on healthcare have outpaced even that, increasing 137%.
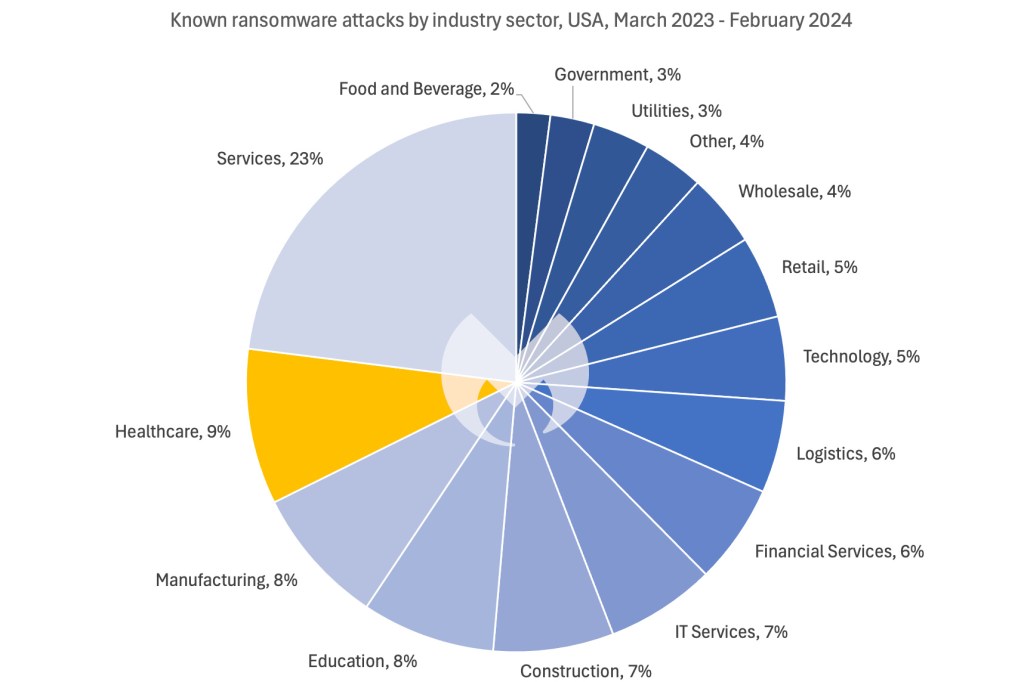
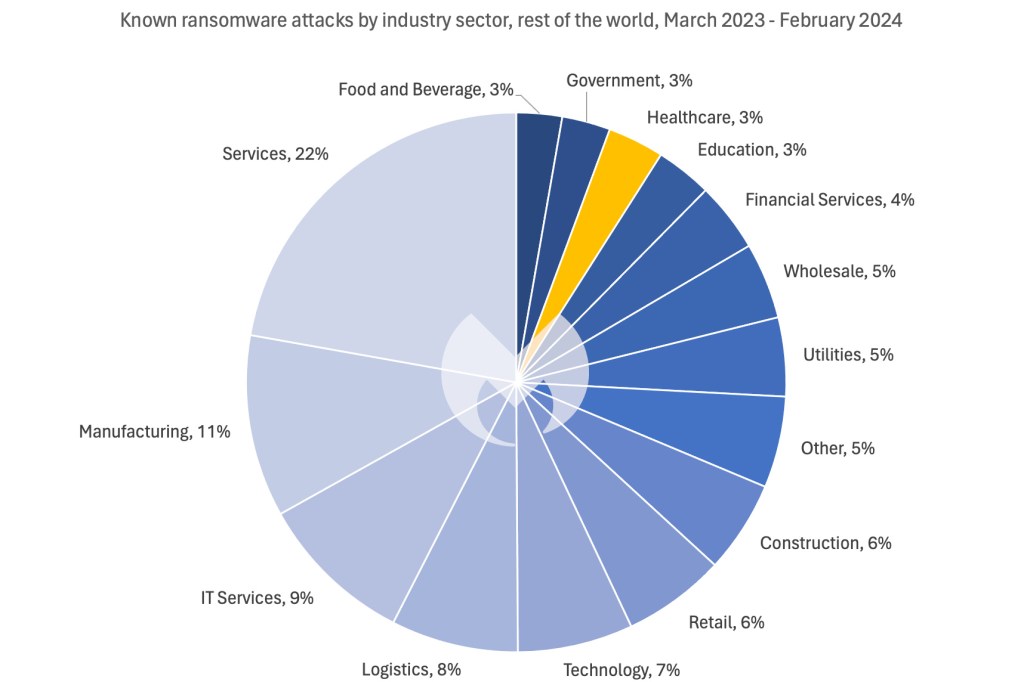
70% of all known attacks on healthcare happen in the US.
This relentless assault has made healthcare the second most attacked sector in the US, where it accounts for 9% of known attacks. In the same period, healthcare accounted for just 3% of known attacks in the rest of the world.
The stark difference between the US and everywhere else may reflect the enormous size of the US healthcare market, or it could be the result of deliberate targeting.
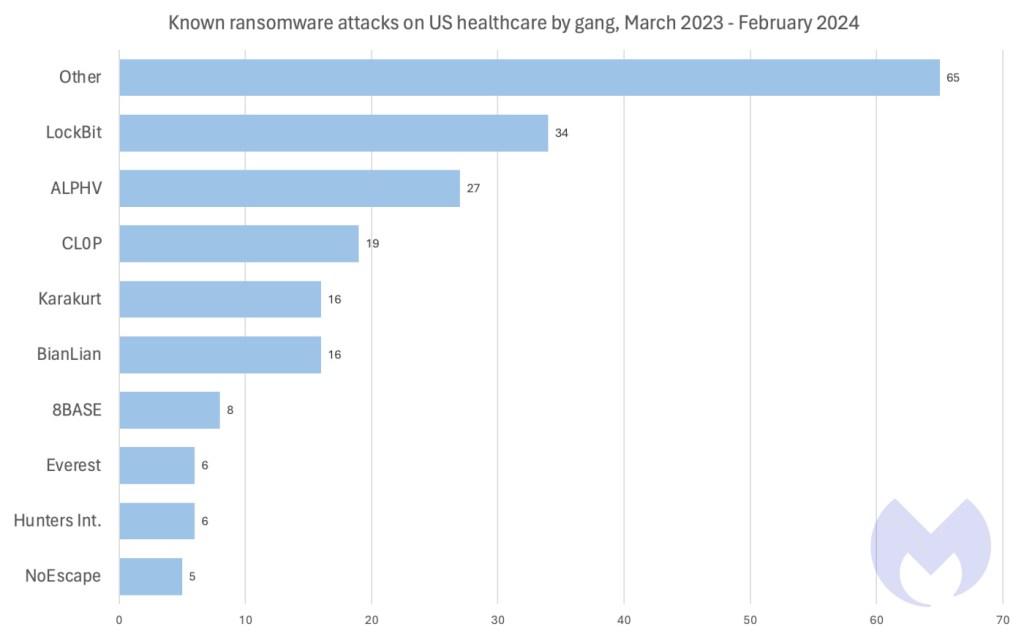
Given its unmatched global footprint, it’s no suprise that LockBit was responsible for more attacks on US healthcare than any other ransomware group in the last year. LockBit is the most widely used ransomware in the world, and tops the list of most active groups across a wide variety of different countries and industry sectors. What is most striking about attacks on US healthcare though is the number of different gangs involved.
In the last year, 36 different ransomware groups are known to have attacked US healthcare targets, and, unusually, the combined contribution of gangs making just a few attacks each vastly outweighs the efforts of big gangs like LockBit and ALPHV.
It’s easy to see why so many ransomare gangs might be drawn to the sector: US healthcare companies are custodians of people’s most private data, guardians of their health, and part of a marketplace worth trillions of dollars. In other words, healthcare isn’t just another industry sector, either for the people who use it, or the people who prey on it. It is a special case, and there is an argument for saying that attacks on organisations like Change Healthcare should be treated like an attack on critical infrastructure.
The last attack on US critical infrastructure, against Colonial Pipeline in 2021, was met with an immediate and ferocious response. Within a month, the FBI had recovered the vast majority of the ransom. The gang behind it, DarkSide, lost control of its infrastructure to US law enforcement (and possibly US military) before going dark, and was quickly hounded out of existence by the FBI after it attempted to remerge and rebrand as BlackMatter.
Knowing that, perhaps it’s not a surprise that the attack on Change Healthcare was one of the ALPHV gang’s last acts before it disappeared in a sloppily exectuted exit scam.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.