A sophisticated cyberattack has compromised Red Hat Consulting’s infrastructure, potentially exposing sensitive data from over 5,000 enterprise customers worldwide.
The breach, executed by the extortion group Crimson Collective, has raised serious concerns about the security of critical business documentation and source code belonging to major corporations, including Vodafone, HSBC, American Express, and Walmart.

Red Hat, the enterprise Linux and cloud computing giant, confirmed the security incident after Crimson Collective publicly disclosed the breach on their Telegram channel.
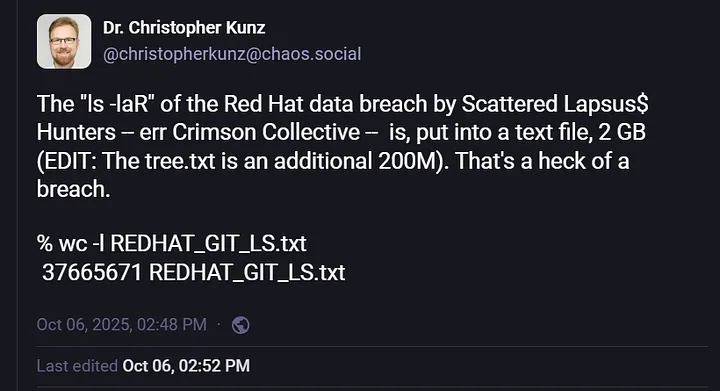
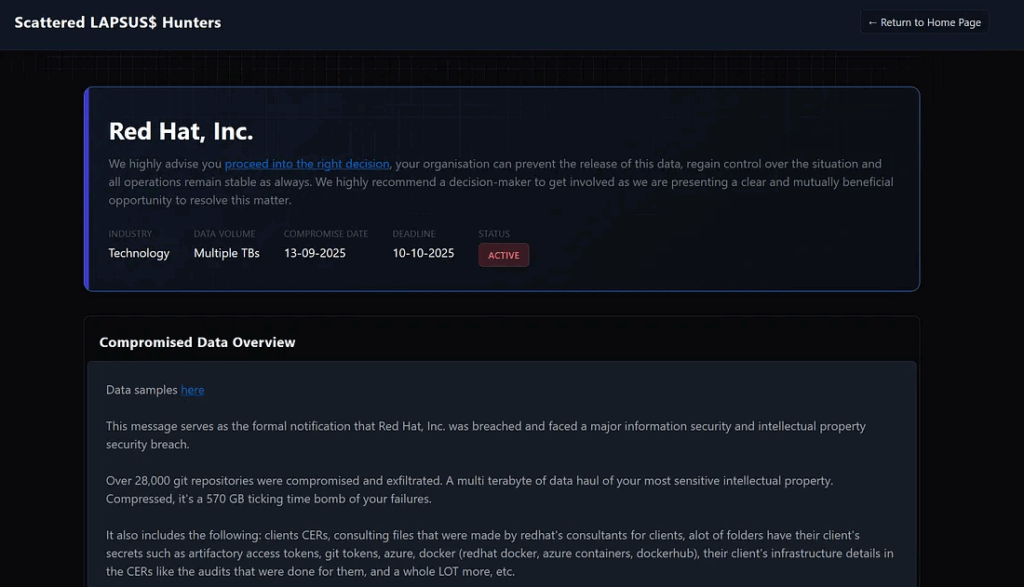
The threat actors claim to have exfiltrated an extensive trove of data containing 32 million files across 370,852 directories, including highly sensitive Consultancy Engagement Reports (CERs), proprietary source code, and private certificates.
LAPSUS$ Connection Emerges
Security researcher Kevin Beaumont have identified crashing similarities between this attack and previous LAPSUS$ operations, particularly through technical artifacts and behavioral patterns.
The breach exhibits characteristic LAPSUS$ signatures, including specific file naming conventions, HTML comment structures containing casual references, and the targeting of organizations previously victimized by the group.
Most notably, investigators discovered that “Miku,” allegedly the Telegram handle used by Crimson Collective, corresponds to Thalha Jubair, a UK teenager associated with LAPSUS$ who was recently charged by the National Crime Agency for the Transport for London cyberattack.
The timeline indicates the Red Hat compromise occurred on September 13, 2025, prior to Jubair’s arrest, raising questions about operational security within custody arrangements.
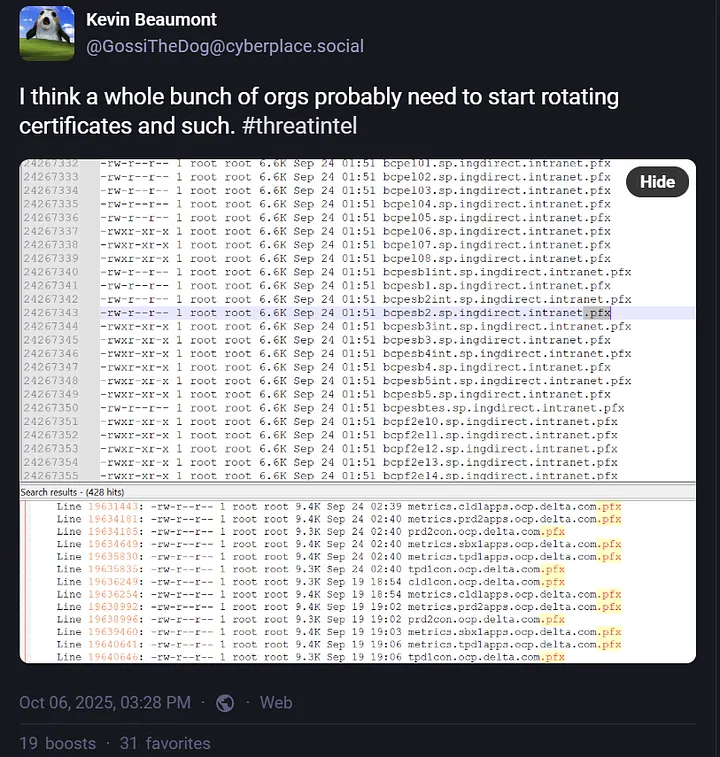
Technical analysis of the stolen data reveals concerns about the exposure of critical infrastructure components.
Kevin Beaumont stated that the breach includes .pfx certificate files from major financial institutions and airlines, which contain private keys that should never be publicly accessible.
These certificates, once compromised, can enable man-in-the-middle attacks, domain spoofing, and unauthorized system access across affected organizations.
The scope of compromised organizations spans multiple critical sectors, including financial services, healthcare, telecommunications, and transportation.
Sample data released by the attackers includes documentation from Atos Group (managing NHS Scotland systems), Bank of China, Delta Airlines, and ING Bank, highlighting the breach’s potential impact on essential services and sensitive customer data.
Red Hat Consulting’s role as a trusted systems integrator for complex enterprise environments amplifies the security implications.
The stolen documentation likely contains network architectures, authentication credentials, API keys, and implementation details that could facilitate secondary attacks against client organizations.
Security experts recommend immediate remediation measures, including certificate rotation, credential updates, and comprehensive security assessments.
Organizations should operate under the assumption that all documented information will eventually become public, as stolen data typically circulates within cybercriminal networks before widespread disclosure.
The incident underscores the growing sophistication of supply chain attacks targeting managed service providers and consulting firms that maintain privileged access to multiple enterprise environments simultaneously.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
