Toyota’s Global Supplier Preparation Information Management System (GSPIMS) was breached by a security researcher who responsibly reported the issue to the company.
GSPIMS is the car manufacturer’s web application that allows employees and suppliers to remotely log in and manage the firm’s global supply chain.
The security researcher, who publishes under the pseudonym EatonWorks, discovered a “backdoor” in Toyota’s system that allowed anyone to access an existing user account as long as they knew their email.
In a test intrusion, the researcher found that he could freely access thousands of confidential documents, internal projects, supplier information, and more.
The issues were responsibly disclosed to Toyota on November 3, 2022, and the Japanese car maker confirmed they had been fixed by November 23, 2022.
EatonWorks published a detailed writeup about the discoveries today after 90 days disclosure process had passed.
Toyota did not compensate the researcher for responsibly disclosing the discovered vulnerabilities.
Breaching Toyota
Toyota’s GSPIMS app is built on the Angular JavaScript framework and used specific routes and functions to determine which users can access which pages.
The researcher found that by modifying the JavaScript for these functions so that they returned “true” values, he could unlock access to the app.
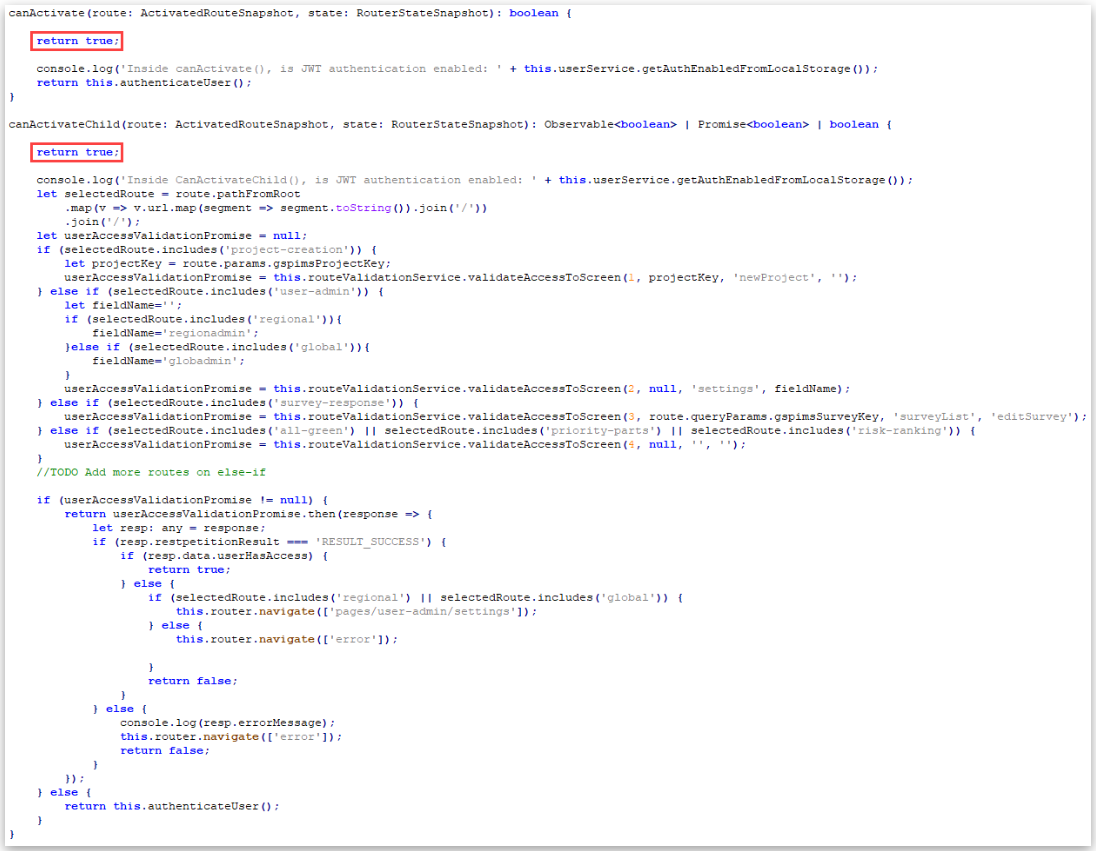
However, while the app was now loaded, it would not display any data as the researcher was not authenticated to the app.
The analyst soon discovered that the service was generating a JSON Web Token (JWT) for password-less login based on the user’s email address. Hence, if someone could guess a valid email address of a Toyota employee, they could generate a valid JWT.
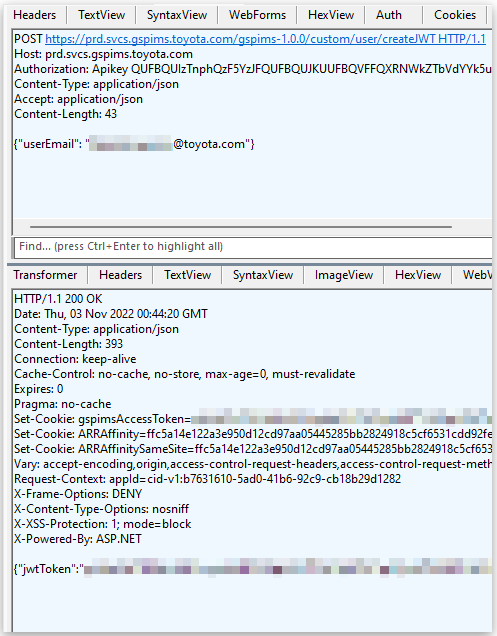
Simply Googling Toyota employees or performing OSINT on LinkedIn would be enough to find or formulate an email address, which is the pathway the researcher took for the intrusion, finding a regional admin account.
From there, EatonWorks escalated to a system administrator account by exploiting an information disclosure flaw in the system’s API. After that, the researcher simply switched to a more privileged account by finding and using a sysadmin’s email address.
Full access to classified docs
A system administrator on GSPIMS can access sensitive information like classified documents, project schedules, supplier rankings, and user data for 14,000 users.
For each of them, the admin can access their projects, tasks, and surveys, change user details, modify or delete data, add redundant backdoor users, or lay the ground for a targeted phishing campaign.
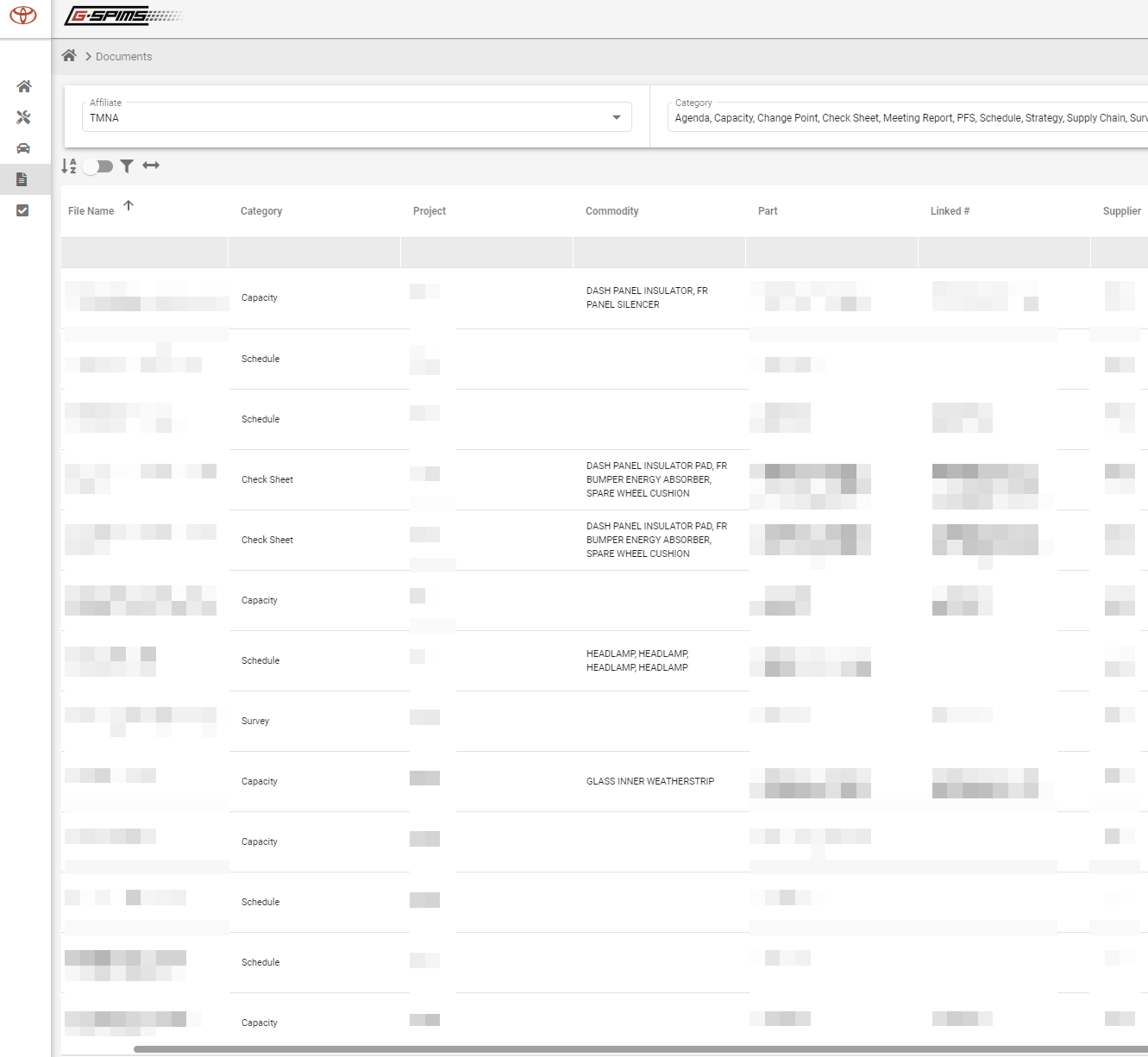
The nastiest aspect of this attack is that a malicious actor could have silently gained access to Toyota’s system and then copied data without modifying anything, keeping the likelihood of discovery very low.
It is impossible to determine if something like that may have already happened, but there have been no massive Toyota data leaks, so it’s assumed that EatonWorks was the first to find the login bypass flaw.
This disclosure comes after a string of breaches, data leaks, and other vulnerabilities discovered over the past year.
In February 2022, the Japanese automaker announced that it was forced to stop car production operations due to a cyberattack on one of its suppliers, Kojima Industries.
In October 2022, Toyota customers suffered a data breach after a contractor developing Toyota T-Connect, the brand’s official connectivity app, left a GitHub repository containing client data publicly exposed.
In January 2023, a security researcher published the details of multiple API security flaws impacting several automakers, including Toyota, which could potentially expose owner details.




