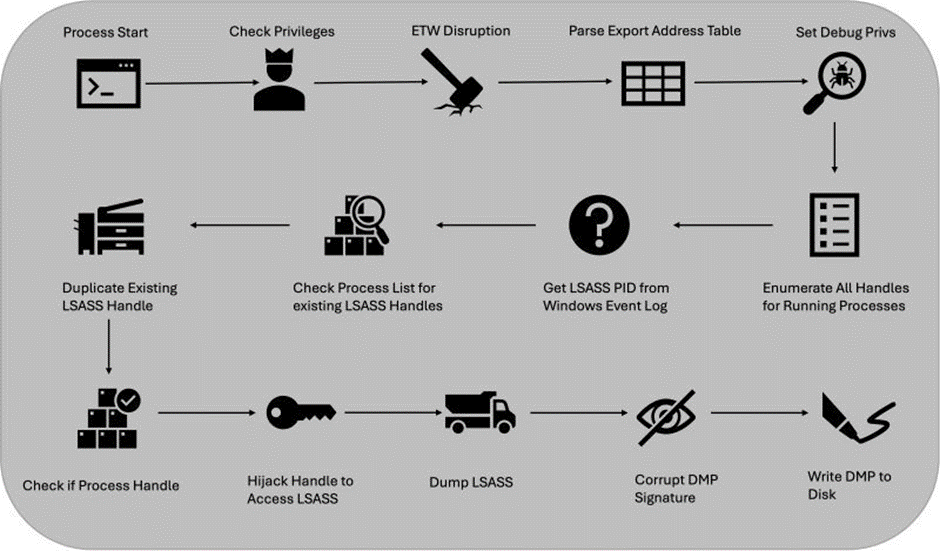
Security researcher Meowmycks unveiled a new tool named LetMeowIn, designed to harvest credentials from the Local Security Authority Subsystem Service (LSASS) process on Microsoft Windows systems.
This tool has raised significant concerns within the cybersecurity community due to its advanced evasion techniques and ability to bypass everyday endpoint security products.
How LetMeowIn Works
According to the BinaryDefense report, LetMeowIn employs the MiniDumpWriteDump function from dbghelp.dll to create a memory dump of the LSASS process.
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
However, instead of writing the dump directly to disk, it first manipulates the dump in memory using MINIDUMP_CALLBACK_INFORMATION.
This allows the tool to alter the dump data before it is written to disk, enhancing its stealth capabilities.
Obfuscation
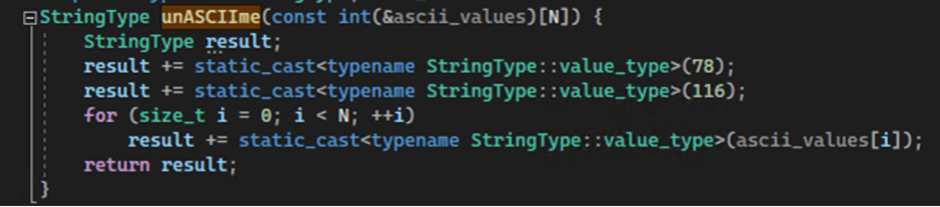
LetMeowIn uses various obfuscation methods to avoid detection.
For instance, it splits the library name “dbghelp.dll” into an array of single characters and reads it into a variable.
Similarly, it obfuscates Windows API functions by encoding their names with Unicode Code Points and storing them in an array.
A function named unASCIIme decodes these arrays back into the original function names.
Indirect Syscalls
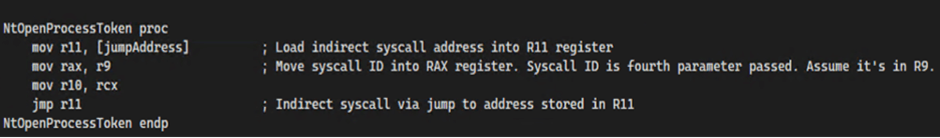
Indirect syscalls are another evasion technique used by LetMeowIn.
Instead of directly invoking system calls, the tool uses an intermediary step involving code obfuscation or redirection.
This makes it difficult for standard detection mechanisms to recognize the system calls.
ETW Tampering
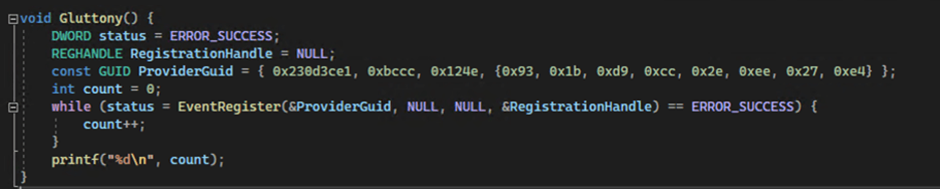
Event Tracing for Windows (ETW) is a logging mechanism endpoint security solutions use to gather telemetry data.
LetMeowIn includes Gluttony, which prevents ETW providers from gathering information by maxing out the number of providers a single process can have.
This technique was first documented by a researcher known as “acebond.”
To avoid detection by antivirus and endpoint detection and response (EDR) solutions, LetMeowIn uses a technique to hijack an existing open handle to the LSASS process.
This is done using the NtDuplicateObject function. The tool then dumps the contents of LSASS to extract credentials.
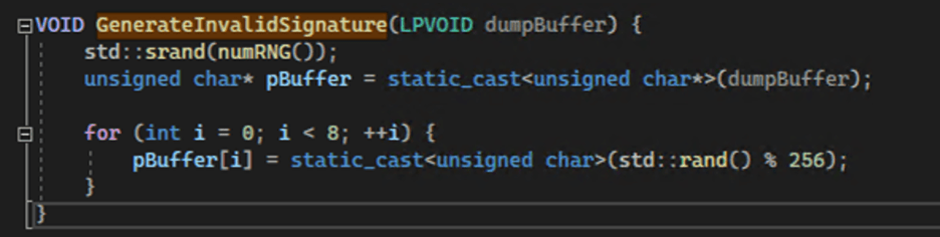
Anti-analysis for Dump Files
Before writing the dump file to disk, LetMeowIn corrupts the file’s MDMP signature using a function called GenerateInvalidSignature.
This prevents common analysis tools from confirming whether the dump file contains credentials.
A Python script in the LetMeowIn project can restore the proper file signature, allowing tools like Mimikatz to extract the credentials.
Detection Opportunities
- Process Creation (4688/Sysmon 1)
One of the simplest detection methods is auditing process creation events for “LetMeowIn.exe.”
However, defenders should know that the process name can be easily modified.
- Image Load (Sysmon 7) for dbghelp.dll
Monitoring for the loading of dbghelp.dll can generate a Sysmon Event ID 7.
Although the binary could be built statically to avoid this event, its absence does not rule out suspicious activity.
- Querying Event Log for 4608
Look for processes querying the event log for Event ID 4608, which can be used to obtain the PID of lsass.exe.
This event signifies a system audit policy change and includes lsass.exe’s process ID.
- Processes with High Volume Calls to NtTraceControl
LetMeowIn registers an event provider repeatedly until the maximum number of providers for a process is reached.
Monitoring for high-volume syscalls to NtTraceControl by a single process can help in detection.
- Auditing Handle Manipulation (4690, 4658, 4656 events)
Enable auditing for handle manipulation to capture events such as handle duplication, closure, and opening.
These events can be correlated to trace actions on lsass.exe.
- Monitoring Registry Access
Monitor interactions with the registry key HKLMSOFTWAREMicrosoftWindows NTCurrentVersionMiniDumpAuxiliaryDlls.
Set a System Access Control List (SACL) restricted to the SYSTEM account to capture access attempts.
The memory dump is typically written to C:tempdebug.dmp.
Watch for file creation in this location, though the path can be easily changed in the code.
- Process Creation for Pause Command
Monitor for another process creation event with the command line C:Windowssystem32cmd.exe /c pause.
This results from the system(“pause”) command but could be removed to avoid detection.
Implementation and Monitoring Strategy
Set up Windows to log process creation events and configure Sysmon for enhanced monitoring.
Enable handle manipulation auditing to log relevant events.
Use scripts or SIEM tools to correlate ProcessID, SourceProcessId, and TargetProcessId across relevant events to track activities associated with lsass.exe.
Apply a SACL on HKLMSOFTWAREMicrosoftWindows NTCurrentVersionMiniDumpAuxiliaryDlls for SYSTEM-only access.
Enable Object Access auditing to capture registry access events.
Monitor the predefined dump file location and employ heuristics or behavioral analysis to identify memory dump creation attempts.
The release of LetMeowIn highlights the ongoing arms race between attackers and defenders in the cybersecurity landscape.
By understanding the techniques used by LetMeowIn, defenders can better prepare to detect and mitigate such threats.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
