Researchers have exposed a systemic vulnerability within the Windows operating system, leveraging its “Best-Fit” charset conversion feature to bypass security checks and execute remote code.
The findings highlight widespread implications across various applications, with real-world exploitation scenarios impacting widely used tools such as Microsoft Excel, PHP-CGI, and others.
Charset Conversion and “Best-Fit” Behavior
Windows systems operate on dual encoding systems, Unicode (UTF-16) for modern compatibility and legacy ANSI for older applications.
To bridge these, Windows employs an internal feature called “Best-Fit” mapping, which approximates characters unsupported by a specific code page to their visually or functionally similar counterparts.
For example, the infinity symbol (∞) may be mapped to the digit “8.”While designed with compatibility in mind, researchers have demonstrated that this behavior inadvertently creates attack vectors, including Path Traversal, Argument Splitting, and Remote Code Execution (RCE).
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Exploited Vulnerabilities
The study revealed multiple CVEs, including:
- CVE-2024-4577 (PHP-CGI RCE):
An attacker can compromise PHP-CGI servers with Chinese or Japanese code pages by appending a specially crafted query string, ?%ADs, to bypass security checks. Here, the Unicode character “Soft Hyphen” (U+00AD) is mapped to a dash (“-“), enabling malicious argument injection—ultimately leading to RCE. - CVE-2024-49026 (Microsoft Excel RCE):
Researchers exploited Excel’s “Open-With” feature to bypass argument parsing controls. By renaming an Excel file using fullwidth Unicode characters and injecting malicious arguments, attackers achieved NTLM Relay-based RCE.
How the Exploits Work
Filename Smuggling
This attack relies on characters converted into path delimiters (/ or ) on specific code pages. For example, the Yen (¥) and Won (₩) symbols in Japanese and Korean code pages are converted into backslashes (), enabling directory traversal.
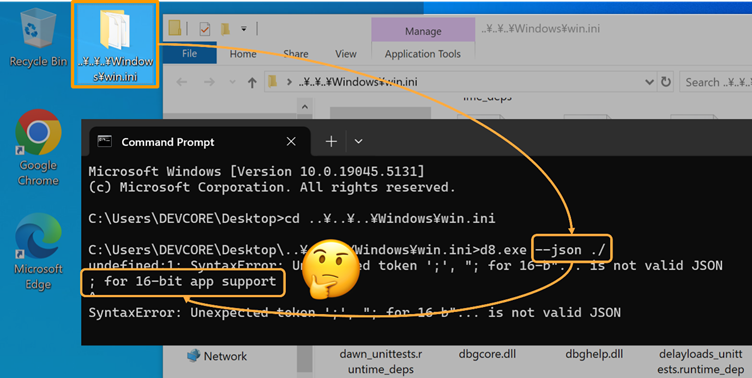
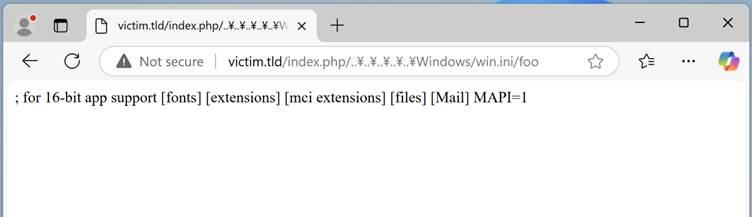
Unintended file access on the C:/windows/win.ini:
#include
int main() {
LPCWSTR filePath = L"AAAA¥..¥..¥..¥..¥..¥conf¥cuckoo.conf";
HANDLE hFile = CreateFileW(filePath, GENERIC_WRITE, 0, NULL, CREATE_ALWAYS, FILE_ATTRIBUTE_NORMAL, NULL);
CloseHandle(hFile);
return 0;
} In this exploit, malicious filenames bypass directory restrictions, exposing sensitive files like configuration settings.
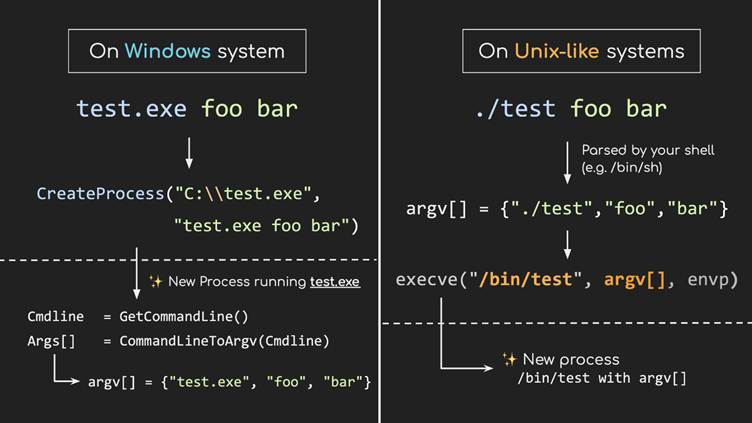
Argument Splitting
Using fullwidth versions of special characters (e.g., " for double quotes), attackers inject additional arguments into Windows command-line processes.

In a Python example:
subprocess.run(['wget', '-q', f"https://test.tld/{path}.txt"])Here, providing malicious input like " –use-askpass=calc " launches calc.exe by splitting the intended command into unexpected arguments.
Environment Variable Confusion
This attack exploits best fit behavior for environment variables. For example, query strings and HTTP headers passed via CGI scripts are manipulated to bypass character restrictions, resulting in Local File Inclusion (LFI) or other attacks.

Case Studies
- Cuckoo Sandbox Exploit:
Leveraging Python’s reliance on ANSI APIs, researchers infiltrated sandbox hosts by smuggling filenames that traversed into restricted directories. - ElFinder RCE:
A malicious tar archive name, crafted with fullwidth characters, injected arbitrary commands, launching calc.exe via GNU tar’s –use-compress-program flag.
Though severe, the vulnerabilities have sparked debate over responsibility and fix feasibility. While some vendors, like Putty, promptly patched their software, others, such as Curl, deferred to developers to sanitize inputs.
As per a report by Devco report, Microsoft acknowledged the severity of certain cases, such as CVE-2024-49026, but did not issue fixes for broader systemic issues tied to legacy Windows functionality.
- Prefer Wide-Character APIs: Using Unicode APIs (e.g., CreateProcessW) prevents unintended ANSI conversions.
- Sanitize Inputs: Ensure robust escaping or validation for all user-supplied data.
- Enable Secure Default Settings: Applications should enable UTF-8 by default, avoiding reliance on legacy code pages.
- Monitor Updates: Developers should stay vigilant about patches from affected vendors and libraries.
This revelation of deeply entrenched vulnerabilities, such as CVE-2024-4577 and CVE-2024-49026, underscores the risks of legacy compatibility features in modern software ecosystems.
As attackers capitalize on low-level quirks like Windows’ “Best-Fit” charset behavior, both developers and security experts must prioritize systemic changes and secure coding standards.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
