Security researchers at CyberProof have uncovered critical connections between two sophisticated banking trojans Maverick and Coyote that are actively targeting Brazilian users through WhatsApp.
The discovery came after investigating a suspicious file download incident flagged through the messaging platform, leading to a comprehensive threat analysis that reveals alarming similarities between the two malware families.
The investigation began when CyberProof’s SOC team and threat hunters detected malicious file activity originating from WhatsApp downloads.
While the complete infection chain proved elusive due to failed command-and-control connections, VirusTotal hunting techniques allowed researchers to collect additional samples tied to the Brazilian-targeting campaign.
Cross-referencing this data with public research from security firms, including Kaspersky, Sophos, and Trend Micro, confirmed the relationship between these banking trojans and earlier variants, such as the WhatsApp worm and Sorvepotel malware.
The technical analysis reveals striking parallels between Maverick and Coyote, suggesting possible code sharing or development by related threat actors.
Both malwares spread through WhatsApp and employ identical infection chains beginning with shortcut (.lnk) files that spawn PowerShell processes in multi-stage attacks.
They utilize the same encryption algorithms to decrypt targeted banking URLs and implement nearly identical routines for monitoring banking applications.
Both families are written in .NET and specifically target Brazilian financial institutions and their users.
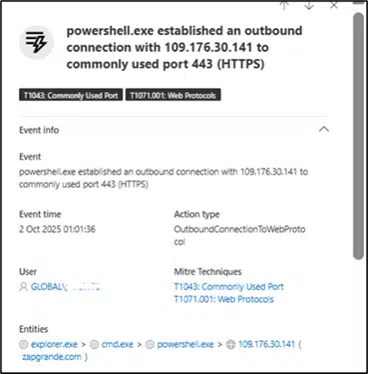
The next PowerShell.exe established an outbound connection with 109.176.30.141.
The attack chain observed in Maverick infections demonstrates sophisticated obfuscation techniques. Researchers identified a malicious zip file downloaded from web.whatsapp.com containing obfuscated code that constructs complex PowerShell commands using nested for-loop structures combined with Base64 and UTF-16LE encoding.
This approach fragments malicious commands across multiple variables, avoiding detection by string-matching security tools. When executed, these commands download second-stage payloads from attacker-controlled infrastructure, turn off Microsoft Defender protections, and disable User Account Control (UAC).
The second-stage payload operates as a .NET loader employing fileless execution techniques. This loader performs anti-analysis checks to detect reverse engineering tools before establishing command-and-control communication. Only when the C2 is live, it proceeds to next stages- according to Kaspersky research.


Upon successful connection, it downloads specialized modules, including a component designed to hijack WhatsApp Web sessions and a banking information-stealing module embedded with the primary agent.
Shared Infrastructure and Attack Patterns
Maverick specifically targets Brazilian financial institutions, including major banks like Bradesco, Banco do Brasil, Itaú, and cryptocurrency exchanges such as Binance and Foxbit.
Similar encryption seen to decrypt Brazilian banking website URLs targeted seen in both Maverick and Coyote. Both are known to use AES + GZIP to decrypt bank URLs stored in base64.


The malware maintains persistence by deploying batch files in Windows startup folders with naming patterns following the format “HealthApp-[GUID].bat.” These persistence mechanisms establish contact with command-and-control servers to receive additional payload stages.
The threat actors employ several evasion strategies, including browser detection routines and geolocation checks to ensure the malware only operates within Brazil.
The malware also includes comprehensive code to monitor browser windows and intercept banking session data when users access targeted financial platforms.
CyberProof researchers have released a detailed hunting query designed for SOC teams and threat hunters to identify suspicious files downloaded through WhatsApp within their environments. This query correlates file download events from WhatsApp origins with subsequent PowerShell execution patterns, enabling organizations to detect similar attack chains before malware becomes operational.
The discovery of these strong technical connections between Maverick and Coyote highlights the evolving sophistication of Brazilian-focused banking malware campaigns.
Organizations operating in the financial sector and their customers should remain vigilant regarding suspicious WhatsApp file downloads and implement robust endpoint protection, application whitelisting, and behavioral analysis capabilities to defend against these persistent threats.
Indicator of Compromise
| Domain | IP Address | ASN |
|---|---|---|
| casadecampoamazonas[.]com | 181.41.201.184 | 212238 |
| sorvetenopote[.]com | 77.111.101.169 | 396356 |
| zapgrande[.]com | 109.176.30.141 | 212238 |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
