
Security researchers successfully exploited vulnerabilities in the StealC malware infrastructure, gaining access to operator control panels and exposing a threat actor’s identity through their own stolen session cookies.
The breach highlights critical security failures in criminal operations built around credential theft.
XSS Vulnerability Exposes StealC Operators
StealC, an information-stealing malware operating under a Malware-as-a-Service model since early 2023, faced a significant setback when researchers discovered a cross-site scripting (XSS) vulnerability in its web panel following a code leak in spring 2025.
By exploiting this flaw, CyberArk Labs collected system fingerprints, monitored active sessions, and captured authentication cookies from the infrastructure designed to steal them.
The irony proved significant: operators specializing in cookie theft failed to implement basic security features, such as the httpOnly flag, that would have prevented cookie hijacking via XSS attacks.
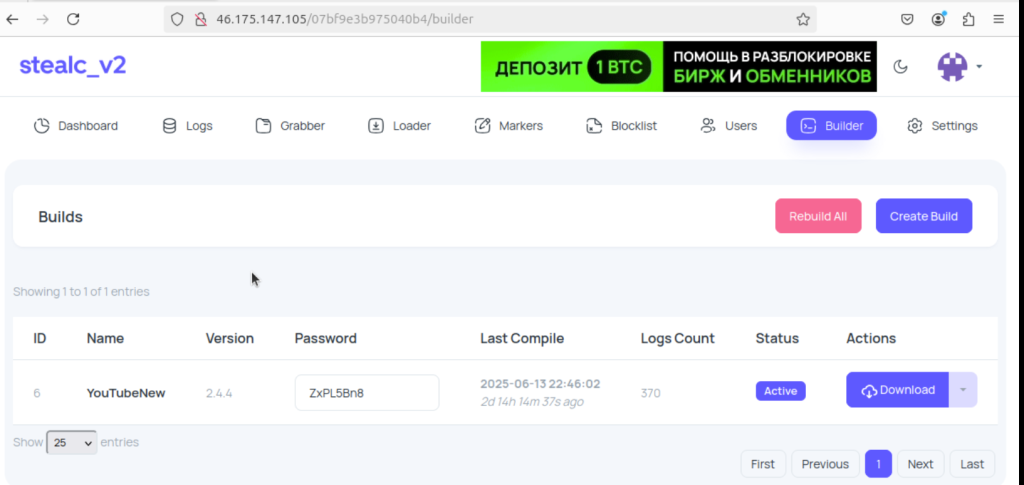
Through panel access, researchers tracked a single operator designated “YouTubeTA” (YouTube Threat Actor) who maintained over 5,000 infection logs containing 390,000 stolen passwords and 30 million cookies.
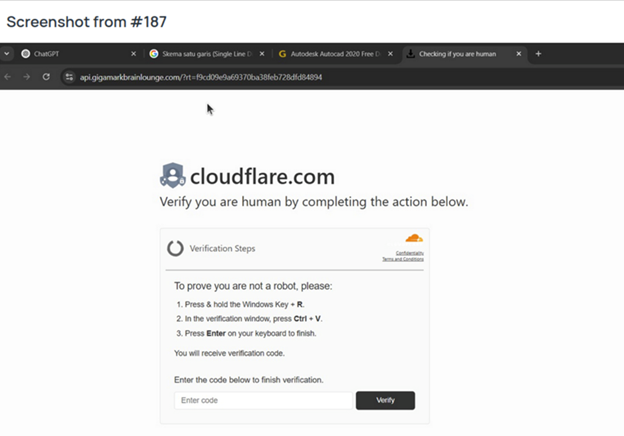
Screenshots captured by the malware showed victims searching for cracked versions of Adobe Photoshop and After Effects on YouTube, suggesting that YouTubeTA compromised legitimate YouTube channels with established subscriber bases to distribute StealC.
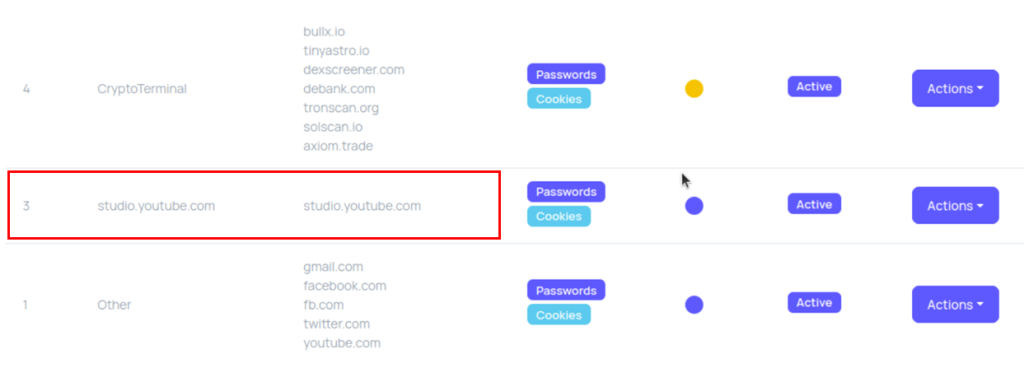
The operator’s panel configuration included specific markers for studio.youtube.com credentials, indicating a strategy to hijack content creator accounts and expand malware distribution networks.
Panel fingerprinting identified YouTubeTA as a single operator using an Apple M3 processor, with consistent hardware signatures across all sessions, as reported by CyberArk Labs .
Language preferences showed support for English and Russian, while timezone data indicated GMT+0300 (Eastern European Summer Time).
A critical operational security failure occurred when the operator briefly connected without VPN protection, revealing an IP address associated with Ukrainian ISP TRK Cable TV.
This breach demonstrates how MaaS supply chain vulnerabilities expose both infrastructure weaknesses and operator identities to security researchers.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
