Security researchers have successfully extracted firmware from a cheap JieLi-based smartwatch by reviving an obscure 2000s attack technique that transmits sensitive data through display pixels.
The novel approach, which builds upon decades-old “blinkenlights” methodology, demonstrates a significant vulnerability in how budget smartwatch manufacturers handle memory access and screen rendering without proper validation checks.
The research began when the team purchased three suspicious €11.99 smartwatches from a local retail store in December 2024, noticing obvious quality red flags typical of fraudulent budget devices.
Upon disassembly, they discovered that the purported health sensors marketed as blood pressure and sleep-tracking capabilities were merely LEDs soldered to a flexible PCB, not functional sensors at all.
This discovery sparked a deeper investigation into the device’s internals and eventually led to uncovering a critical firmware extraction vulnerability.
The smartwatch’s system-on-chip (SoC), identified as a JieLi AC6958C6 processor, initially seemed difficult to extract firmware from without proprietary tools.
Blinkenlights Technique
After attempting various DIY approaches and facing extended wait times for official JieLi programmers, the researchers discovered a different path forward while fuzzing dial image offsets.
They realized the firmware parser failed to validate whether specified memory offsets remained within bounds, unthinkingly copying data from arbitrary SoC memory addresses directly to the display as image pixel data.
This discovery triggered the application of the “blinkenlights” technique, a classic attack method used initially in the 2000s to extract data from network devices by analyzing LED blink patterns.
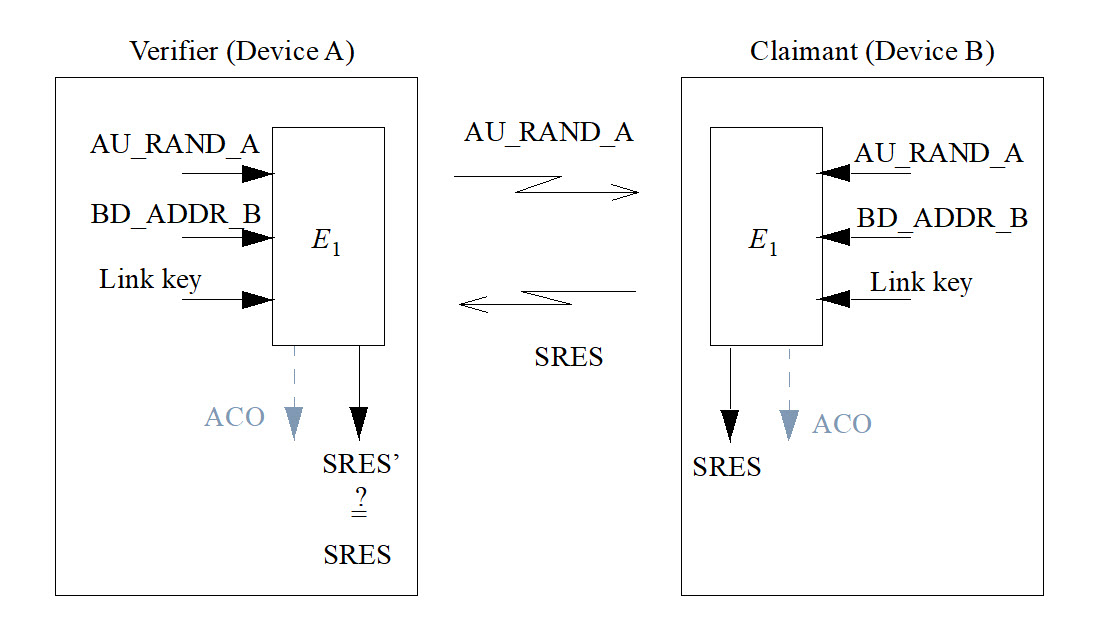
E1 function defined in the Bluetooth specification and used as its legacy authentication algorithm.
In this case, rather than LEDs, the researchers exploited the smartwatch TFT screen controller a NV3030B device to transmit memory contents as visible pixels.
The attack proved technically challenging, requiring either sophisticated optical capture equipment to photograph pixel states or direct interception of the screen controller communication lines.
The team pursued two parallel approaches. Thomas Cougnard attempted optical data recovery by capturing displayed pixels through specialized imaging equipment, while his collaborator Damien chose electronic interception using logic analyzers connected to the screen data lines.
As the IoT landscape expands with increasingly cheap connected devices, this case demonstrates the importance of proper input validation and secure firmware architecture to prevent unauthorized memory access and data exfiltration through physical side-channels like display outputs.
Smartwatch Security Flaws
Upgrading to a Raspberry Pi Pico–based analyzer capable of 100 Megasamples per second successfully decoded TFT screen commands and allowed firmware extraction by monitoring data transmissions to the NV3030B controller.
The vulnerability highlights a critical failure in the smartwatch’s firmware design: the lack of bounds checking on image offset values and the assumption that all memory regions were safe to transmit to the display.
This architectural oversight, combined with the predictable nature of TFT screen communication protocols, created an unexpectedly effective attack surface on what appeared to be a sealed consumer device.
The research underscores that budget hardware manufacturers often skip essential security validations, creating scenarios where decades-old attack methodologies remain viable threats.
Initial attempts using standard 8 Megasamples per second analyzers proved insufficient for the 25 MHz clock speed governing screen communication.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
