Between July and December 2025, cybersecurity firm Team Cymru conducted an extensive analysis of carding infrastructure, revealing a sophisticated network comprising 28 unique IP addresses and 85 domains that actively host illicit carding markets and forums.
The research employed technical fingerprinting methods crucial for financial institutions, law enforcement agencies, and fraud fusion centers working to combat payment card fraud campaigns.
Team Cymru’s infrastructure tracking capability provides the global defender community with early identification of carding-related IP addresses before cybercriminals can fully protect them.
Through internet-wide scanning, analysts can detect newly created or modified servers before they disappear behind obfuscation layers.
These early-stage IP addresses offer critical evidence for subpoenas, takedown operations, and evidence collection efforts.
Additionally, Team Cymru’s NetFlow analysis capabilities enable researchers to map related infrastructure directly connected to IP addresses used for carding operations.
Key Research Findings
The investigation identified 28 unique IP addresses hosting login pages or forum landing pages for carding markets and forums.
A significant finding revealed that many autonomous system numbers (ASNs) hosting this infrastructure belong to offshore infrastructure providers operating in jurisdictions with limited international law enforcement cooperation.
The research also uncovered that the most prevalent top-level domains (TLDs) used by carding infrastructure are .su, .cc, and .ru domains offering jurisdictional shielding and minimal oversight.
Team Cymru utilized large-scale internet telemetry and metadata analysis, leveraging internet-wide port scanning, passive DNS collection, and NetFlow data.
The methodology involved performing Regular Expression (Regex) searches across HTTP and HTTPS title banners on ports 80 and 443 to identify servers broadcasting carding-specific keywords such as “CVV,” “Dumps,” “Carding,” and “Shop.”
Analysts further refined their approach by indexing X509 certificates and analyzing Subject Common Names, enabling the clustering of related infrastructure based on reused certificate attributes.
The advantage of this internet-wide scanning is its ability to identify underlying origin servers before Content Delivery Networks (CDNs) like Cloudflare obscure them.
By capturing server identity and host IP addresses during initial configuration phases, researchers can bypass CDN-based obfuscation and map the bulletproof hosting environments where these illicit marketplaces reside.
Offshore Hosting Preferences
ASN distribution revealed that multiple carding markets were hosted on Privex servers, which advertise “privacy-minded infrastructure” offering dedicated virtual private servers (VPS).
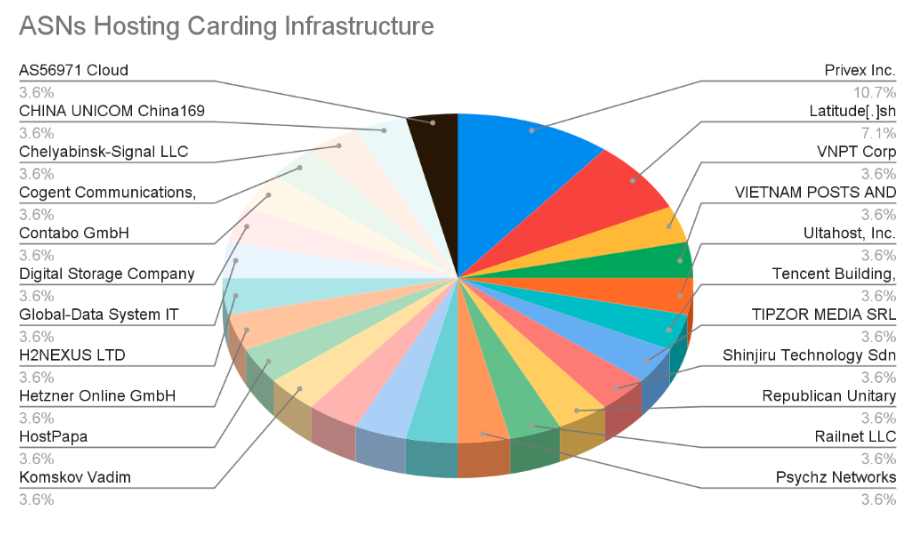
Criminals can purchase these servers without providing identifying information and host illicit content without facing consequences.
Notably, Privex AS210083 also hosts offensive security tools like Sliver, demonstrating that hosting services preferred by carders typically support multiple types of malicious campaigns simultaneously.
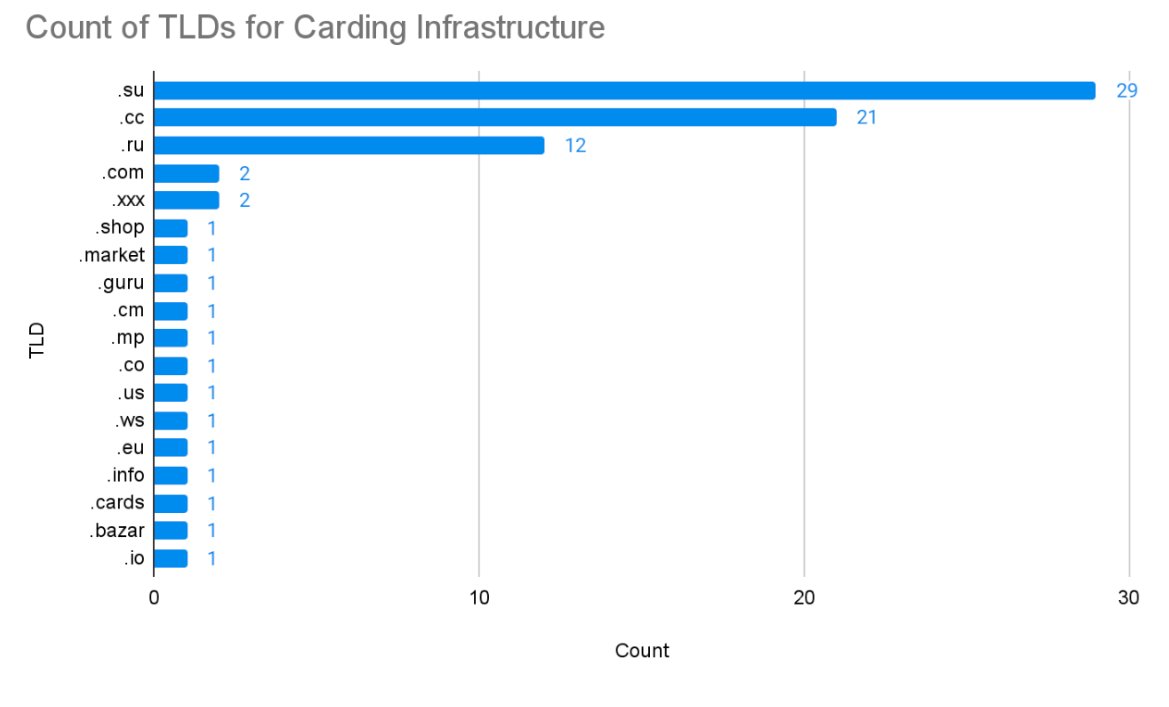
Across the 28 unique IP addresses, researchers identified 85 unique carding-related domains. The heavy concentration of .su, .cc, and .ru TLDs reflects strategic choices by cybercriminals.
The Soviet Union .su TLD, belonging to a defunct nation, operates under loose registration and abuse policies.
The .cc domain is favored because it can represent “credit card” while remaining inexpensive and easy to register in bulk. Meanwhile, .ru domains provide effective insulation from Western court orders when servers are physically located within Russia.
Team Cymru researchers continue investigating cybercrime infrastructure using internet telemetry collection capabilities.
Through Team Cymru Scout, customers can execute sophisticated search queries to identify carding markets and their hidden backend servers proactively.
NetFlow analysis uncovers linked infrastructure, enabling fraud teams to connect individual fraudulent transactions to broader criminal networks.
This methodology transforms network intelligence into a proactive disruption tool, raising operational costs for threat actors worldwide.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
