Cybersecurity researchers have discovered a sophisticated attack technique that exploits Microsoft Azure Arc deployments to gain persistent access to enterprise environments.
The research, conducted during recent red team operations, reveals how adversaries can leverage misconfigured Azure Arc installations to escalate privileges from cloud environments to on-premises systems and maintain long-term persistence through legitimate Microsoft services.
Azure Arc, Microsoft’s hybrid cloud management platform, extends Azure’s native management capabilities to on-premises systems, Kubernetes clusters, and other non-Azure resources.
.webp)
While designed to streamline hybrid infrastructure management, the service’s deployment mechanisms and configuration processes have introduced new attack vectors that threat actors can exploit.
The research demonstrates how attackers can identify Arc deployments in enterprise environments and abuse common misconfigurations to achieve code execution with system-level privileges.
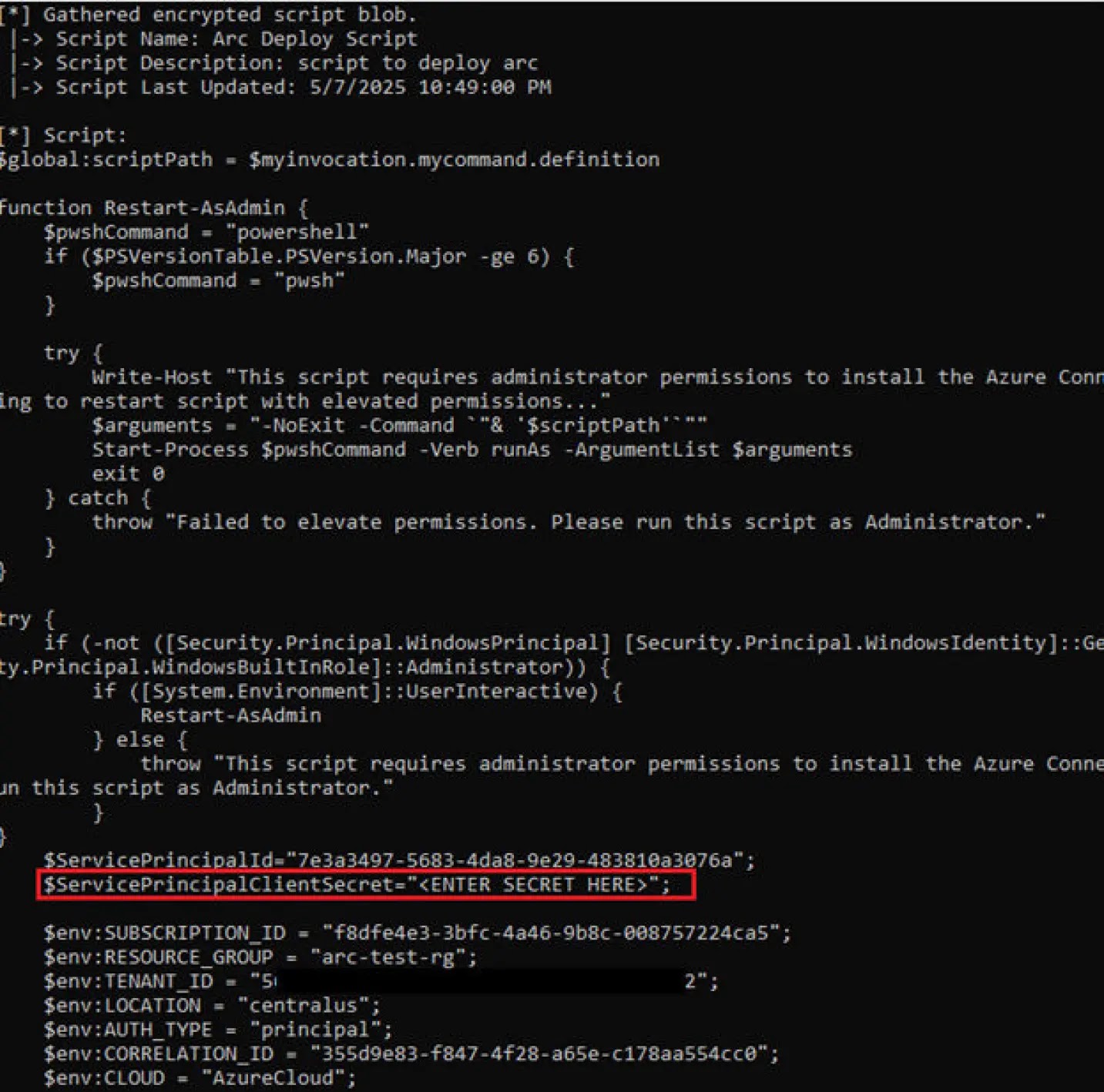
The attack techniques center around the exploitation of Service Principal credentials that are often hardcoded in deployment scripts or stored in accessible network shares.
.webp)
These credentials, originally intended for automated Arc client registration, can be recovered by attackers who gain access to deployment infrastructure or policy configurations.
Once obtained, these credentials can be weaponized to execute arbitrary code on Arc-managed systems through various Azure management interfaces.
IBM analysts identified multiple deployment vectors that introduce security vulnerabilities, including PowerShell scripts with embedded secrets, misconfigured System Center Configuration Manager (SCCM) deployments, and Group Policy Objects (GPOs) that store encrypted credentials using DPAPI-NG.
.webp)
The research team noted that these deployment methods, while following Microsoft’s official guidance, often result in credential exposure due to overly permissive access controls and inadequate secret management practices.
DPAPI-NG Exploitation and Credential Recovery
The most significant finding involves the exploitation of DPAPI-NG encrypted secrets stored in Azure Arc deployment shares.
When Arc is deployed via Group Policy, administrators create network shares containing deployment files, including an “encryptedServicePrincipalSecret” file protected by DPAPI-NG encryption.
However, this encryption is configured to allow any member of the domain computers group to decrypt the secret, effectively making it accessible to any compromised system in the domain.
The decryption process involves accessing the deployment share and using PowerShell commands to retrieve the encrypted blob.
Attackers can execute the following technique from any system with NT_AUTHORITYSYSTEM privileges:-
$encryptedSecret = Get-Content (Join-Path $SourceFilesFullPath "encryptedServicePrincipalSecret")
# DPAPI-NG blob configured to allow any member of domain computers group to decryptThis credential recovery method provides attackers with Service Principal access that can be immediately weaponized for code execution on Arc-managed systems.
The research demonstrates that these recovered credentials often possess elevated privileges beyond their intended scope, including the “Azure Connected Machine Resource Administrator” role, which grants comprehensive management capabilities over Arc deployments.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
