Rhysida ransomware group added one of the largest public health insurance agencies for the elderly in Latin America to its victim list.
The National Institute of Social Services for Retirees and Pensioners, or Programa de Atencion Medica Integral (PAMI) in Spanish, was named a victim by the Rhysida group.
The targeted website was not accessible at the time of writing after the alleged PAMI cyber attack.
PAMI cyber attack
The PAMI cyber attack claim posted about by the Rhysida ransomware group on its dark web portal was with a deadline of six days. Threat Intelligence platform Falcon Feeds tweeted screenshots of the PAMI cyber attack from the hacker’s website.
The tweets were made on August 12, indicating the deadline being reduced to four days.
The ransomware group made a demand of 25 BTC for the data from the PAMI data breach. Samples with records of the exfiltrated data were posted with identity cards bearing photos of people.
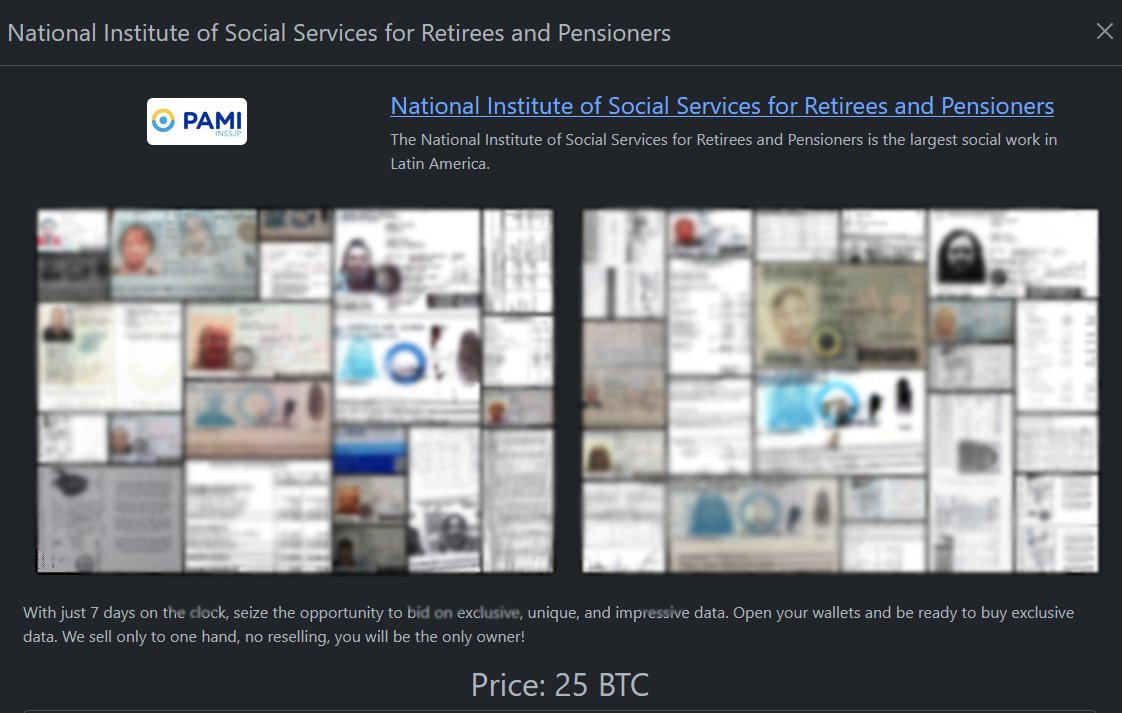
“With just 7 days on the clock, seize the opportunity to bid on exclusive, unique, and impressive data,” wrote the hackers from Rhysida.
The Rhysida ransomware group threatened to leak the data from the PAMI data breach and called buyers on the dark web for the stolen data.
Details about the National Institute of Social Services for Retirees and Pensioners (PAMI)
The parent agency of the insurer PAMI is the Ministry of Health of Argentina. The Cyber Express emailed the Ministry of Health for comments about the hacker claims. We will update this report based on their response.
Catering to its beneficiaries, a Wikipedia page outlines that PAMI operates under the umbrella of the Instituto Nacional de Servicios Sociales para Jubilados y Pensionados (National Institute of Social Services for Retirees and Pensioners, INSSJP). PAMI is dedicated to serving senior citizens and veterans of the 1982 Falklands War.
PIMA operates 37 regional offices and provides free medicines to 650,000 pensioners and retirees. It has over 4 million enrollees.
Rhysida ransomware group targeting healthcare
The ransomware group Rhysida was discovered in May 2023 and they use ChaCha20 in its payload for file encryption. They reach their targets via phishing emails deploying the payload using several methods including Cobalt Strike.
Researchers found that Rhysida’s ransom notes are written in PDF documents and saved in the affected folders of the targeted system. They demand a ransom in Bitcoin alone and ask the targets to reach out for negotiations via their TOR-based portal.
Recently, Rhysida has been found targeting the healthcare sector including the cyber attack on Ejercito de Chile. They leaked data from the Ejercito de Chile cyber attack on its dark web portal in June.
The cyber attack on Prospect Medical Holdings is also suspected to be by Rhysida which resulted in a system outage impacting all its facilities and clinics across the U.S.
The Center for Wound Healing, Urgent Care Center, and Women’s Center for Wellness and Evergreen Imaging Center among others remained closed after the cyber attack.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
