Accounting software provider Tipalti says it is investigating a claim by ransomware group ALPHV that they have gained access to Tipalti’s systems.
Tipalti makes software for accounting and payment automation and has some big names among its customers. In what seems to be a typical supply chain attack, ALPHV aka BlackCat are now threatening some Tipalti customers, including Roblox and Twitch:
“We are systematically reaching out to affected clients of Tipalti, the first batch (consisting of organizations with the most data exfiltrated), have been sent communications requesting initial contact.”
Organizations who share these file lists, samples or notes with Tipalti run the risk of having their data leaked immediately.
The ransomware group claim to have had access since September 8, 2023. Since then, they say they have stolen 265 GB of data, including data for Twitch and Roblox, who they say they will extort separately.
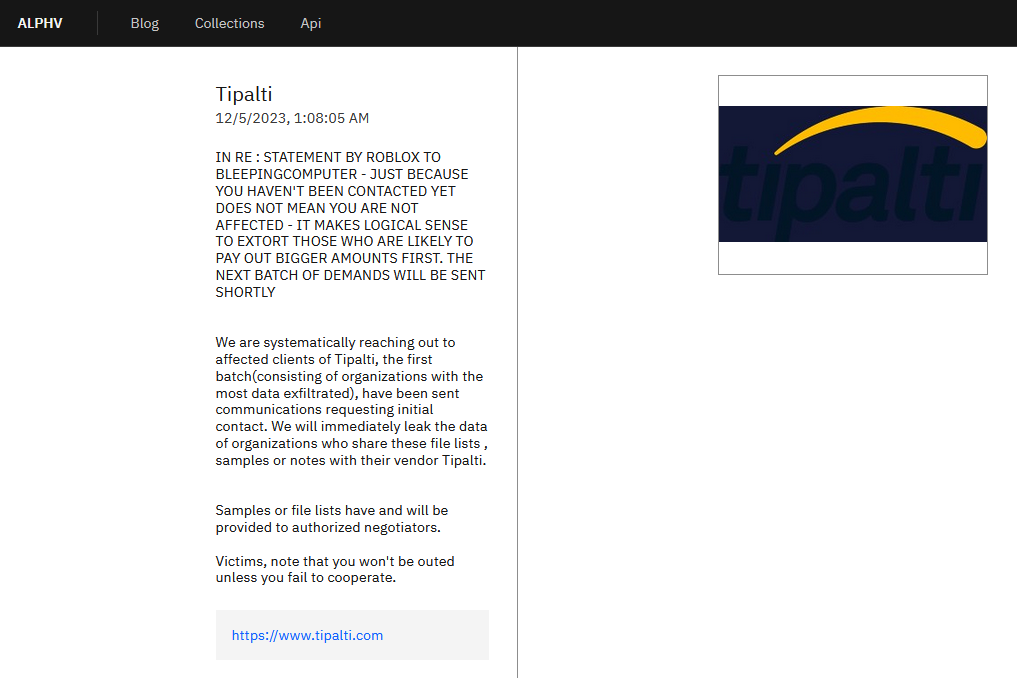
Screenshot of the ALPHV leak site
A Roblox spokesperson told BleepingComputer that the company is working with Tipalti to investigate the claims, but is currently unaware of any impact on its systems. The spokesperson stated they haven’t been contacted by anyone about the security incident, to which ALPHV responded on their leak site:
“Re: statement by Roblox to BleepingComputer. Just because you haven’t been contacted yet, does not mean you are not affected.”
ALPHV is one of the most active ransomware-as-a-service (RaaS) operators and regularly appears in our monthly ransomware reviews as one of the top 5 most active groups. Recently they made headlines when one of their affiliates, known as Scattered Spider attacked MGM. They also last week filed a SEC complaint about one of their victims for failing to disclose a breach.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
