Royal ransomware group has added Livingston International, the North American provider of customs brokerage services, to its victim list. A post on the group’s leak site claimed to have information, including employee documents, financial details, and network structure data of Livingston International.
Livingston International provides customs brokerage, trade consulting and international freight forwarding services to importers and exporters throughout North America and around the globe. Cybersecurity analyst Dominic Alveiri tweeted about the data leak along with this image:
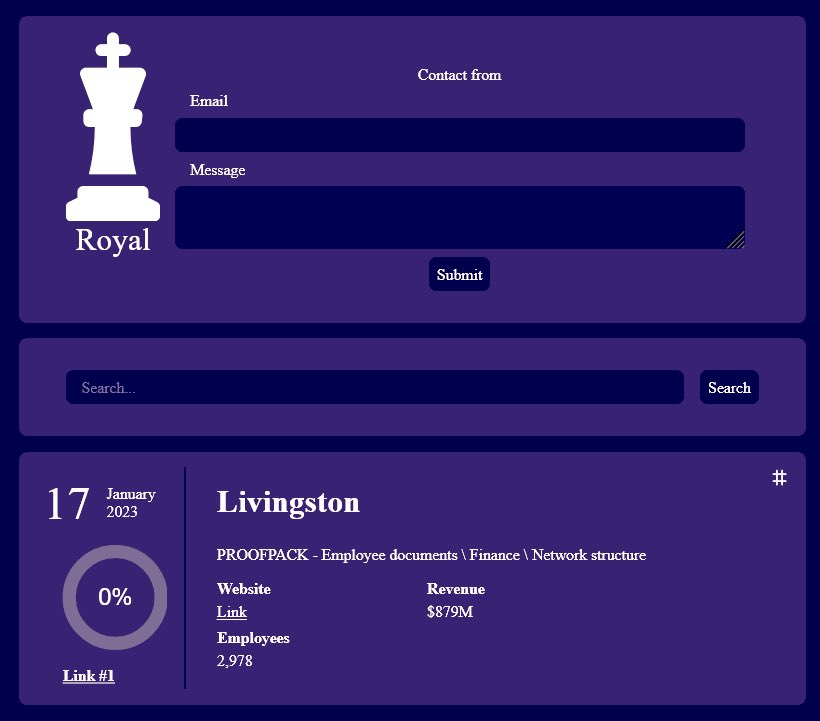
“Toronto based Canadian international customs broker Livingston International is breached by Royal Ransomware,” read the tweet. The post revealed to have information of 3,200 employees, 30,000 customers, and 125 key border entry points.
Alvieri also shared details about a cyberattack on the Australian Carinya Christian School by the same group. The tweet, posted on January 17, suggested that LockerRoyal, which is the name of the group’s Twitter account, was behind the breach.
The Royal ransomware group also claimed to be behind several data breaches. They revealed so via its Twitter account on January 13. These include:
- Intrado (Telecommunications Company – United States) with revenue of $3.5 billion
- AONTTAGL (Agostini insurance brokers – Headquartered in West Indies) with revenue of $33 million
- The Queensland University of Technology (QUT – Australia) with revenue of $669 million
- Suzhou Dongshan Precision Manufacturing Co. Ltd. (China) with revenue of
- Bevolution Group (Beverage Company – United States) with revenue of $50 million
- LEK/ HABO (Manufacturing and Engineering – Netherlands) with a revenue of $21 million
Royal ransomware group
The Royal ransomware was discovered in January 2022 and uses phishing emails or malicious advertisements to reach targets.
They also target individuals via calls or posing as food delivery agents. Their phishing emails tend to urge targets to click on malicious subscription renewal for food or software they may use.
When unsuspecting users call the number provided in the email, they are convinced to make changes to their software or to install remote access software. Their systems are breached using the access gained via this installation.
They earlier used BlackCats encryptor but now use their own ZEON encryptor. Their ransomware note resembled the ones by the Conti ransomware group.

Royal also uses the Google Ads platform to insert malicious and infected content mimicking legitimate advertisements. The group revamped its techniques and attack tactics in September 2022. The group uses several ransomware and places the .Royal extension on encrypted files of the target.

The group is also suspected to be behind the attack on Silverstone Circuit, a famous racing circuit based in the United Kingdom. Its ransom demand ranges between $250,00 to $2,000,000.
